A Concise Guide to DevSecOps and Their Importance in CI/CD Pipeline
What is DevSecOps and its importance? Understand DevSecOps pipeline and its Implementation in the CI/CD pipeline. Also, learn about various security benchmarks.
Leveraging continuous integration and delivery (CI/CD), many businesses today automate the software development life cycle. CI/CD is a part of the DevOps process, which aims to accelerate software development while minimizing errors. Continuous delivery automates the entire software release process up to production, whereas continuous integration produces and tests code automatically. However, security still possesses a significant concern. That brings us to the critical question, why is security a primary concern?
CI/CD pipeline enhances your software development capabilities by providing several benefits. These include fewer code modifications, a shorter mean time to fix issues, more reliable tests, quicker release cycles, a lower backlog of products, and more customer satisfaction.
Unfortunately, hackers are also taking advantage of vulnerabilities in the CI/CD pipeline. They have the ability to steal data, mine cryptocurrencies, and introduce malware into programs. Therefore, industry leaders created the DevSecOps methodology to secure it.
What Is DevSecOps, and Why Should We Use It?
DevSecOps is a theory that advocates integrating security procedures into the DevOps process. It is also used to define a software development life cycle that emphasizes continuous delivery and security. Finding the security flaws at the conclusion of the SDLC can be very frustrating. Security engagement is encouraged to become a significant component of the software development life cycle by introducing DevSecOps (SDLC) to the CI/CD pipeline’s best practices.
A streamlined process is created by DevSecOps. Performing security testing without slowing down delivery cycles, it is consistent with lean techniques. It enables teams to resolve problems as they are discovered rather than waiting for an attack. This makes it possible for all three teams to benefit from agile methodologies without compromising the objective of writing secure code.
Relationship Between DevSecOps and CI/CD
Every open source library that you use can be the breeding ground for security vulnerabilities. With tons of developers working on multiple projects simultaneously, manual testing is not a scalable option. DevSecOps offers continuously to the CI/CD pipeline by securing the software deliverables. DevSecOps also verifies the authenticity of any external libraries used in the project, the risks and vulnerabilities associated with licenses, etc. Any confidential information, such as a password or login information, is put into a git repository along with the code.
Integrating automated security checks with CI/CD gives early warnings of any security vulnerabilities that may be present during any stage. This makes it feasible for your business to scale as it expands.
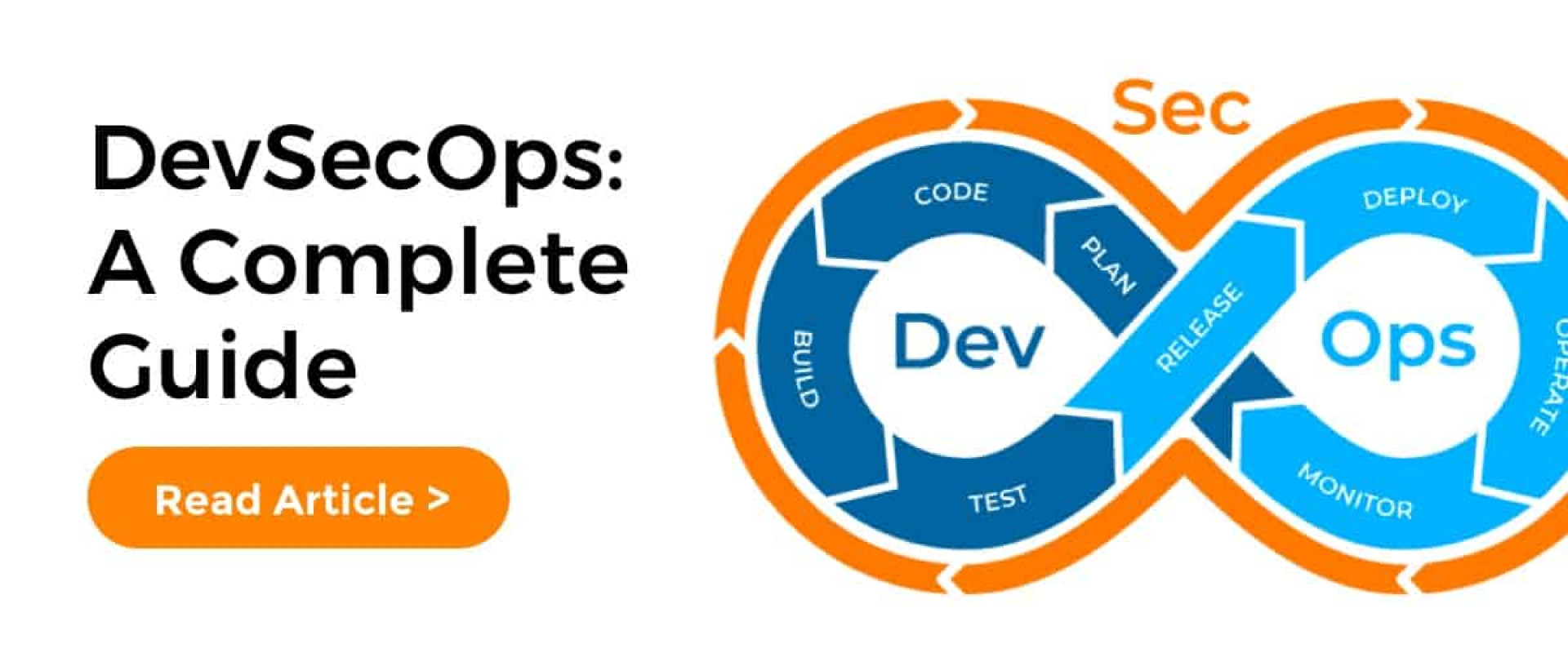
Steps in the DevSecOps Pipeline
DevSecOps pipeline is a little bit different from a typical DevOps pipeline. A DevOps pipeline includes - Plan, Code, Build, Test, Release and Deploy. In the DevSecOps pipeline, specific security checks are conducted in each phase of the DevOps cycle. Usually, the DevSecOps pipeline consists of five steps as follows -
1. Planning - Prepare a plan for how, where, and when testing will take place by doing a security analysis.
2. Code - Use linting tools and Git controls to secure API keys and sensitive passwords.
3. Build - Use SAST(static application testing) tools to track down bugs before production deployment
4. Test - While testing, DAST or dynamic application security testing tools are leveraged for error detection that is directly linked with user authentication, SQL injection, and API endpoints.
5. Release - The vulnerability scanning and penetration testing processes are carried out using security analysis tools. Use these tools just before releasing the code.
Implementing Security in CI/CD Pipeline Using DevSecOps
Leverage SAST and DAST Tools
The SAST code analyzers find security flaws in both your code and imported libraries. Choose a SAST scanner that is compatible with your programming language because these tools are tailored to specific programming languages. SAST can potentially indicate false positives, so it is advised to proceed with caution. False positives can make the team frustrated to the point that they stop responding to notifications from damaged pipelines.
Unlike SAST, dynamic application security testing tools or DAST verifies your program while it is operating from the outside, much like an intruder would. Since they work with external applications, DAST scanners don't require any particular languages. Integrate both of these strategies into our workflow to provide you with early notification of any security flaws.
Managing Secrets
Secrets contain sensitive information and demand special attention. Secrets and credentials are also used by cloud workloads to access additional resources and services that are essential to their operation. There are various ways to share these secrets. The secrets can be baked right into the image when deploying your system as packages using VM images or containers. By doing so, it can only be accessible in a file when the workload executes. Another way of keeping a secret is to encrypt and keep it in source control. The workload can then retrieve, decrypt, and use the secrets after receiving the decryption key.
Know Your Dependencies
We also need to take into account the application's dependencies as an additional attack surface. It is crucial first to understand the dependencies and any known weaknesses. We can perform an analysis on the program and develop a software bill of materials for it to assist us with that.
Finally, we can continuously monitor what is happening in our Kubernetes cluster, just as we occasionally check for the images kept in the registry. By doing this, it will be made sure that there are no suspicious activities, such as unusual network queries, running images with significant CVEs, etc.
Container Security Benchmarks
Containerization technology is widely popular. It involves using containers to put your application into serverless infrastructure. Although containers are secure in general, however Center of Internet Security (CIS) offers guidelines on the correct use of containers in any application. Following these benchmarks are mandatory for someone using docker and Kubernetes.
IST SP 800-190
In its application container security guide, the National Institute of Standards and Technology (NIST) of the U.S. government describes containers as a type of virtualized operating system.
PCI
A framework that aids in the protection of data in the retail and e-commerce sectors is the payment card industry (PCI) standards.
HIPAA
Patient data protection in healthcare is governed by the Health Insurance Portability and Accountability Act (HIPAA).
Conclusion
Clearly, DevSecOps is a valuable addition to your CI/CD pipeline for incorporating security with continuous delivery. If you have any other important DevSecOps implementation pointers in mind, do let us know in the comments below.
We Provide consulting, implementation, and management services on DevOps, DevSecOps, Cloud, Automated Ops, Microservices, Infrastructure, and Security
Services offered by us: https://www.zippyops.com/services
Our Products: https://www.zippyops.com/products
Our Solutions: https://www.zippyops.com/solutions
For Demo, videos check out YouTube Playlist: https://www.youtube.com/watch?v=4FYvPooN_Tg&list=PLCJ3JpanNyCfXlHahZhYgJH9-rV6ouPro
If this seems interesting, please email us at [email protected] for a call.
Recent Comments
No comments
Leave a Comment
We will be happy to hear what you think about this post