An Easy Way to Get Your Own Binary Repository
If you don't want to upload your artifacts to public repositories, or if you work on a private network with no connection to public repositories, you need to be able to store dependencies offline in a private repository and push or pull them locally.
A Binary Repository Manager (BRM), according to Wikipedia, is “a software tool designed to optimize the download and storage of binary files used and produced in software development”, such as .jar, .tar, or .zip archives. Being a critical component of most DevOps toolchains, BRM resides right after the build pipeline. It is why it is sometimes called “build repository”, “artifact repository” or “pipeline state repository”.
A traditional DevOps pipeline expects the source code that is automatically validated, tested, packaged, and versioned into an artifact (a binary file). Then, the artifact must be stored outside of the source code repository and available for later stages of the continuous delivery pipeline. Being a central point for management of binaries and dependencies, and an integrated depot for building promotions of internally developed software, the BRM is supposed to host these artifacts.
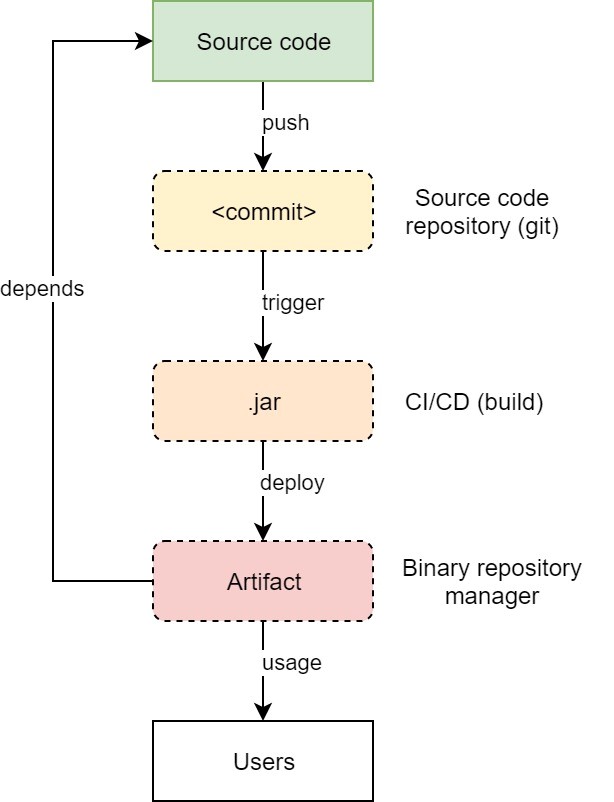
A software project of almost any size needs to keep its binary artifacts in a repository to enable access to them by programmers or by tools that ensure Continuous Integration (CI), Delivery (CD) and Deployment (CD). Since the quality of the software that manages the repository matters, the BRM should meet such requirements as
Integrability–there are plenty of build automation tools for each programming language, like Maven for Java, Npm for JavaScript, or Rake for Ruby. There are also many continuous integration tools, like Jenkins or Travis. Since automation is the most important aspect of DevOps, it is expected to have plugins for each or most of them, enabling seamless integration with the BRM.
Availability–artifacts are important components of a software development process and they must be available to a programmer or a build tool immediately when needed, without even minor delays, and delivered at the highest possible speed.
Scalability–most build artifacts are large binary files; some of them may be larger than 1Gb, for example, Docker images or .war (production-ready Java archives). The BRM must be able to maintain large data sets, up to almost no size limitation.
Reliability–the ability to corrupt the data because of software or hardware failures must be excluded as much as it is possible.
Artipie
Artipie is a free binary artifact management tool. Artipie is not just a binary artifact web server - it's an artifact management constructor, which comprises many components built into server assembly. It is an open-source project that started in 2020 and is actively growing.
All Artipie components are based on reactive, asynchronous, non-blocking, and back-pressured streams and principles, allowing Artipie to withstand heavy workloads with a small number of kernel threads.
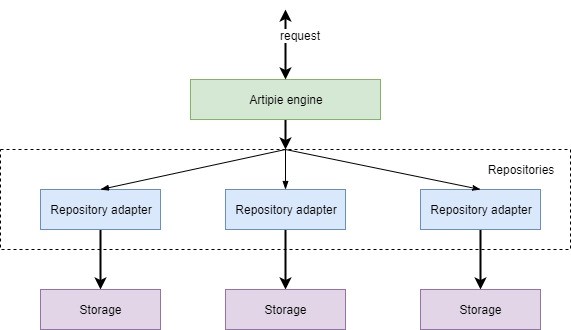
The Artipie architecture consists of 3 essential parts:
1. Artipie HTTP engine
2. Repository adapters
3. Storages
 \\
\\
Artipie HTTP Engine
The Artipie engine is a Java application, which exposes an HTTP endpoint for repository access and management operations. It routes HTTP requests to the repository adapter and provides authentication mechanisms. The Artipie HTTP engine, built on the Vert.x and RxJava frameworks, provides lightweight flexibility and scalability to the project through asynchronous, reactive, and non-blocking operations.
The most common data flow for the Artipie upload action is as follows: the client is sending some binary artifact to the server, which finds a responsible repository adapter to process the request; the repository adapter saves the stream to the storage; after completing, it updates the metadata of the repository (some repositories work differently, for example, Docker uses metadata as a path).
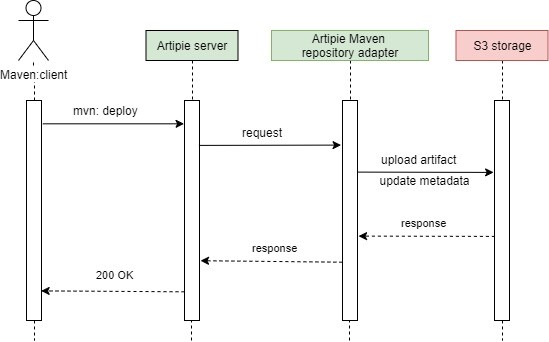
Repository Adapters
Repository adapters are independent projects, aimed at implementing an API to interact with the repository client and meta information generation layers for a specific package type (npm, maven, etc.). The Artipie engine uses adapters in order to provide BRM functionality. Each repository adapter encapsulates storage API to access binary blobs and metadata files.
Artipie supports the following types of repositories:
Docker - private Docker registry for images.
Maven - Java, Kotlin, Groovy, Scala, Clojure artifacts and dependencies of varying types like a .jar, .war, .klib and etc.
NPM - JavaScript code sharing and packages store.
PyPI - Python packages index.
Anaconda - built packages for data science for Python, R, Lua, C, C++, etc.
RPM - .rpm packages repository for RHEL, PCLinuxOS, Fedora, AlmaLinux, CentOS, openSUSE, OpenMandriva, Oracle Linux, etc.
Gem - RubyGem hosting service for Ruby.
Go - Go package storage.
Files (binary) storage - host any files you like.
Helm - Helm charts repository.
NuGet - hosting service for .NET packages.
Debian - package repository for Debian-based Linux distributions: Ubuntu, MX Linux, Mint, Raspberry Pi OS, Parrot OS, etc.
Composer - package source for PHP packages.
Storage
Repository adapters place the uploaded and created binary files in the storage. Artipie has abstract storage that provides an abstraction over a physical data storage system. The simplicity makes it easy to implement the interface for almost any data storage system. It has two major operations: to put and get an item from storage with a few additional functions, such as to check if an item exists, to list storage items, or to obtain the item metadata.
At the moment, there are the following storage implementations:
1. File system storage
2. Redis storage
3. S3 based storage
Abstract storage also provides an interface that can be implemented to support any type of storage you need.
Start Using Artipie
You have two options for working with Artipie:
Run
Artipie Docker image with Docker Compose
Run Artipie jar archive on JVM
I will show a simple example of how to run Artipie locally with Docker Compose and configure it as a repository for Docker images on a Windows machine.
Preparing
To run Artipie, you need to have Docker installed,
then you can simply clone the GitHub
repository with the example on the path C:\, or follow
the steps:
1. Make a
folder for the Artipie project (e.g. C:\artipie)
2. Create a
folder for the Artipie configuration (e.g. C:\artipie\config) and place
in the folder the yml file with the Artipie server configuration. In my
example, the file is called artipie.yml. You must
specify the path where Artipie will find all repository configurations. I
specify the configuration path of the Docker repository as var/artipie/repo, because I
mount the folder from the local Windows machine C:\artipie\repo to
directory /var/artipie/repo in Artipie Docker container,
when setting-up docker-compose.yml in
step №4.
3. Create a folder for the repository configuration files
(e.g. C:\artipie\repo), then put
in the folder the yml file with the repository configuration. The name of this
file will be the name of the repository to be created. For example, the file
will be named my-docker.yml and
the repository will be named my-docker accordingly.
To configure storage with the FileStorage type, it is enough to set the path
where Artipie will store all the items. The system must read and write
permissions to create files on this path. In my example, the path will be /var/artipie/images.
Launch
Now, open the CLI, go to the folder with the docker-compose.yml file
and start Artipie with the console command: docker-compose
up.
In the CLI, we see that Artipie has started on port 8080 and
found a repository configuration file my-docker.yml.
Usage
Before pushing any images, let's pull an existing one from
Docker Hub. My choice is an alpine image. Pull the alpine image with the
command: docker pull alpine:
With the next command, we create our docker image called myfirstimage from the alpine image for pushing it to our Artipie repository:
docker image tag alpine
localhost:8080/my-docker/myfirstimage. Check that docker has 2
images: alpine and localhost:8080/my-docker/myfirstimage, with
the command: docker images:
Now, we have to login into our own registry with the default
user artipie|artipie, because the Docker registry supports only authorized
users: docker login --username artipie localhost:8080:
Conclusion
A binary repository is a key element in any DevOps pipeline and various projects need various types of binary repositories to store artifacts. Almost every programming language ecosystem has its own kind of artifact repository. Artipie provides a wide range of adapters for the major packaging formats in one product, enabling the management of all artifacts from one place. Artipie is growing and developing rapidly, and it provides the ability to add the implementation of its own binary data storage, in addition to File, Redis, and S3 storage.
Artipie is a good choice for storing binary artifacts because it is simple for configuration. It has support for many types of repositories. As an open-source product, it is absolutely free for use.
We Provide consulting, implementation, and management services on DevOps, DevSecOps, Cloud, Automated Ops, Microservices, Infrastructure, and Security
Services offered by us: https://www.zippyops.com/services
Our Products: https://www.zippyops.com/products
Our Solutions: https://www.zippyops.com/solutions
For Demo, videos check out YouTube Playlist: https://www.youtube.com/watch?v=4FYvPooN_Tg&list=PLCJ3JpanNyCfXlHahZhYgJH9-rV6ouPro
If this seems interesting, please email us at [email protected] for a call.
Relevant blogs:
Top 5 Data Science, AI, And ML Trends for 2022
Infra: A Promising Way To Manage Kubernetes Users
Protect the Pipe! Secure CI/CD Pipelines With a Policy-Based Approach
Role of AI and ML in DevOps Transformation
Recent Comments
No comments
Leave a Comment
We will be happy to hear what you think about this post