Application Security Predictions Over the Next 12 Months

Exploring the potential of artificial intelligence and blockchain within the next year.
Cybersecurity is evolving with companies investing in artificial intelligence (AI) and machine learning (ML) to bolster security capabilities. Hacking incidents are becoming the norm at the enterprise level, and companies are leveraging AI technology in response to these growing cyber threats. From Equifax, Hotel Marriot, NetEase, and Yahoo, these companies suffered major data breaches that exposed personal information and accounts. Social media companies have not been spared from hacking. Facebook, LinkedIn, and the Chinese social platform Sina Weibo have come under attack from cybercriminals in the past.
The human intervention seems less effective today given the rise of malware attacks, phishing, and ransomware. The explosion of data and devices in the current digital environment has further escalated cybersecurity threats, giving cybercriminals more loopholes for the attack. On average, a data breach costs a company close to $4M, considering that most enterprises detect threats in their systems after six months. These statistics paint a dim picture of the current cybersecurity landscape with most companies lacking a solid cybersecurity plan in 2021.
Figure 1
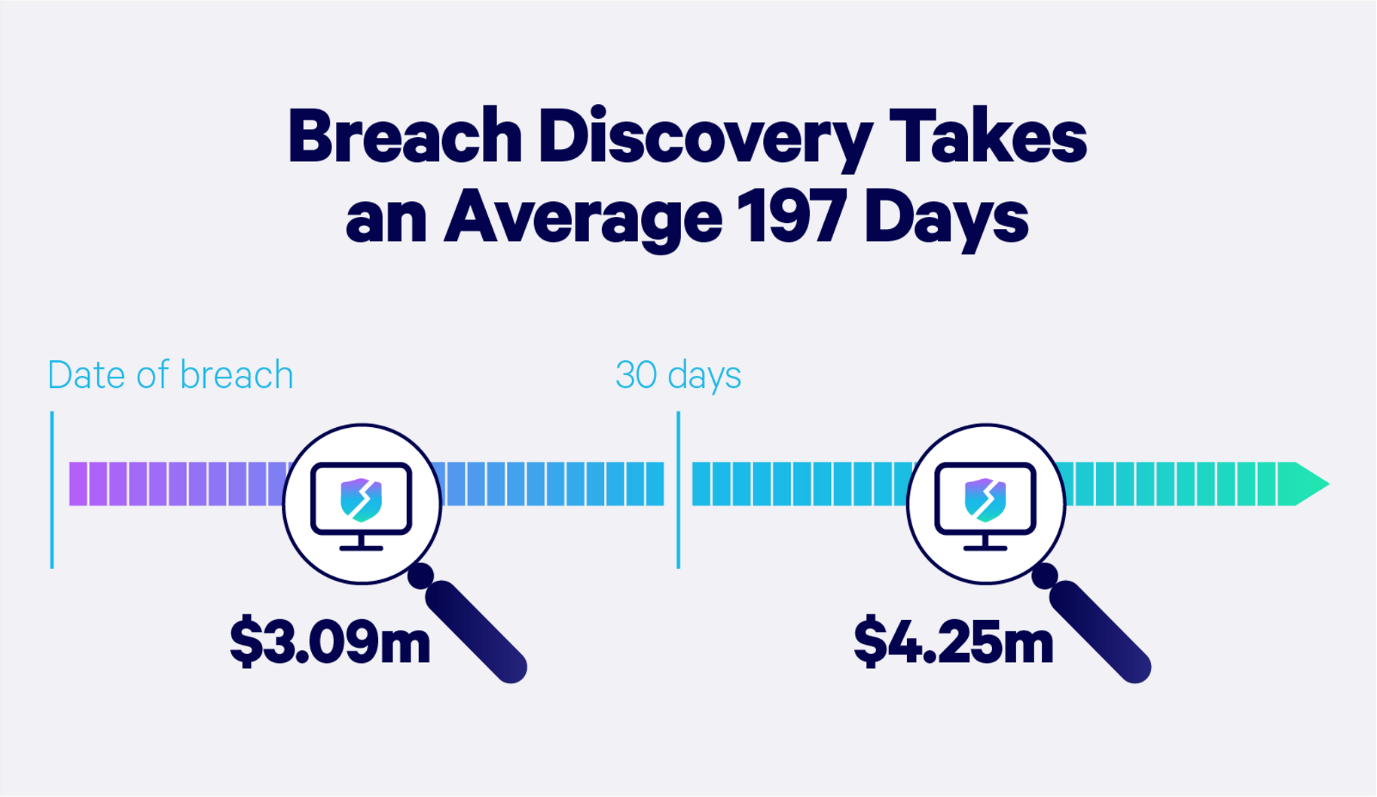
This is where artificial intelligence and machine learning can step in and take charge of enterprise security systems. Machine learning algorithms detect threats within a system, report them for prompt action, and reduce the time required to address cyber threats. A good example is a threat intelligence tool that utilizes ML capabilities for detecting cyber incidents. The precision of a system improves because of AI capabilities, which further improves threat detection.
Blockchain is coming of age in the current digital environment as enterprises leverage the technology, which prevents hackers from accessing sensitive information. The decentralized nature of blockchain makes it difficult for cyber criminals to attack the system because there is no single point of target. Because network traffic and storage of data are not in a single hub, security systems become stronger, giving hackers a hard time breaking through the database.
This article will explore application security predictions for artificial intelligence and blockchain, including threats, technologies, and practices.
This is an excerpt
from DZone's 2021 Application Security Trend Report.
For more:
Read the Report
<!--[if !supportLineBreakNewLine]-->
<!--[endif]-->
Technologies and Practices
1. Crime Management and Security
Public safety is critical to a functioning society, and while human intervention has not succeeded in reducing cybercrime, artificial intelligence is augmenting us by offering real-time information on system threats. The Avata Intelligence application in California is helping authorities predict and understand chances of terror attacks. By using game theory and artificial intelligence, the Avata Intelligence tool is bolstering the safety of California and enabling data-driven decision-making.
Smart drones are also trending with authorities using them for surveillance and mapping regions for crime evaluation. Drones cover large areas that the police cannot manage to oversee, and by relaying data in real time, cities around the world are using smart drones to safeguard against crime. The Armorway software used by the Coast Guard makes the surveillance of ports easier as the technology offers security status in Boston and New York. Port security is critical, and the Armorway software attests to the adoption of technology for improving security across different areas.
2. Vulnerability Evaluation
Hacking incidents find companies least prepared — by the time intervention measures come up, the damage has already occurred. This gives hackers more power to keep exploiting company systems on servers and using loopholes to cause harm to data. Databases are using AI and machine learning to assess the vulnerability status and improve controls to prevent cyber-attacks. Database companies are using ML capabilities to secure client databases with advanced security measures.
A User and Event Behavior Analytics (UEBA) tool ensures that companies can review their system security across endpoints and servers. Anomalies within systems come in different forms; a UEBA tool — with the aid of artificial intelligence — ensures that enterprises detect these systemic issues early and offer intervention measures.
3. Security of Data Centers
The data center infrastructure is critical for healthy functioning of enterprise security controls. AI technology is enabling optimization in areas like power consumption of data centers, cooling systems, rate of bandwidth, and backup systems. By offering insights into these areas of data center management, companies secure their systems by using analytics to understand the performance of data centers. Tech companies such as Google have achieved success by using AI for data center management, including the reduction of power and cooling expenditures.
4. Internet of Things Security
The Internet of Things (IoT) explosion has created new threats that organizations are using AI and ML to implement strengthened IoT security. AI predictive tools for companies such as AT&T are assisting in understanding customer sentiment and offering personalized services in real time. AT&T’s use of predictive tools across their data centers has helped the company improve the customer experience and educate company leaders on their performance status across the board. The data processing at AT&T offers a glimpse of artificial intelligence and machine learning processes at work in enterprises committed to drive business growth by leveraging technology.
E-commerce companies are tapping into the power of AI to understand customer preferences and recommend products based on their previous shopping or search results.
Network analytics platforms are on the rise with a good example of IBM Watson for IoT, which offers real-time data on the condition of assets and provides solutions to improve the assets in bad condition. The demand for network analytics platforms will spike in the next decade as companies look to use AI for optimization of assets and cost management.
5. Consumer Information Evaluation
The application of technology for consumer information management continues to evolve with companies using data to understand populations. The healthcare sector’s use of data and personal information is rising, and this helps in understanding solutions for better health care. Despite concerns about invading personal privacy by using health records of patients, the healthcare industry represents another area ripe for technological innovation.
Thanks to the explosion of big data, it is becoming easier to understand populations by using social media platforms to gauge their health patterns and recommend data-based healthcare outcomes while respecting their privacy.
Threats
Artificial intelligence can improve security controls or necessitate vulnerabilities at the same time. This is a trend happening where hackers use AI technology in datasets to corrupt the data. Security systems come under attack in such an instance due to the manipulation of the learning system. Attacks also occur through transfer learning within ML systems because they are pre-trained. This gives hackers an opportunity to access systems because they understand the training models.
Training ML systems by use of manipulated inputs is growing as hackers develop their own training models. Hackers are going even further by training models again for system manipulation. Data privacy is at stake when hackers invade systems. This is a growing threat that could continue causing more harm if not addressed. Cyber criminals are developing effective mechanisms to infiltrate systems despite security control interventions.
Figure 2
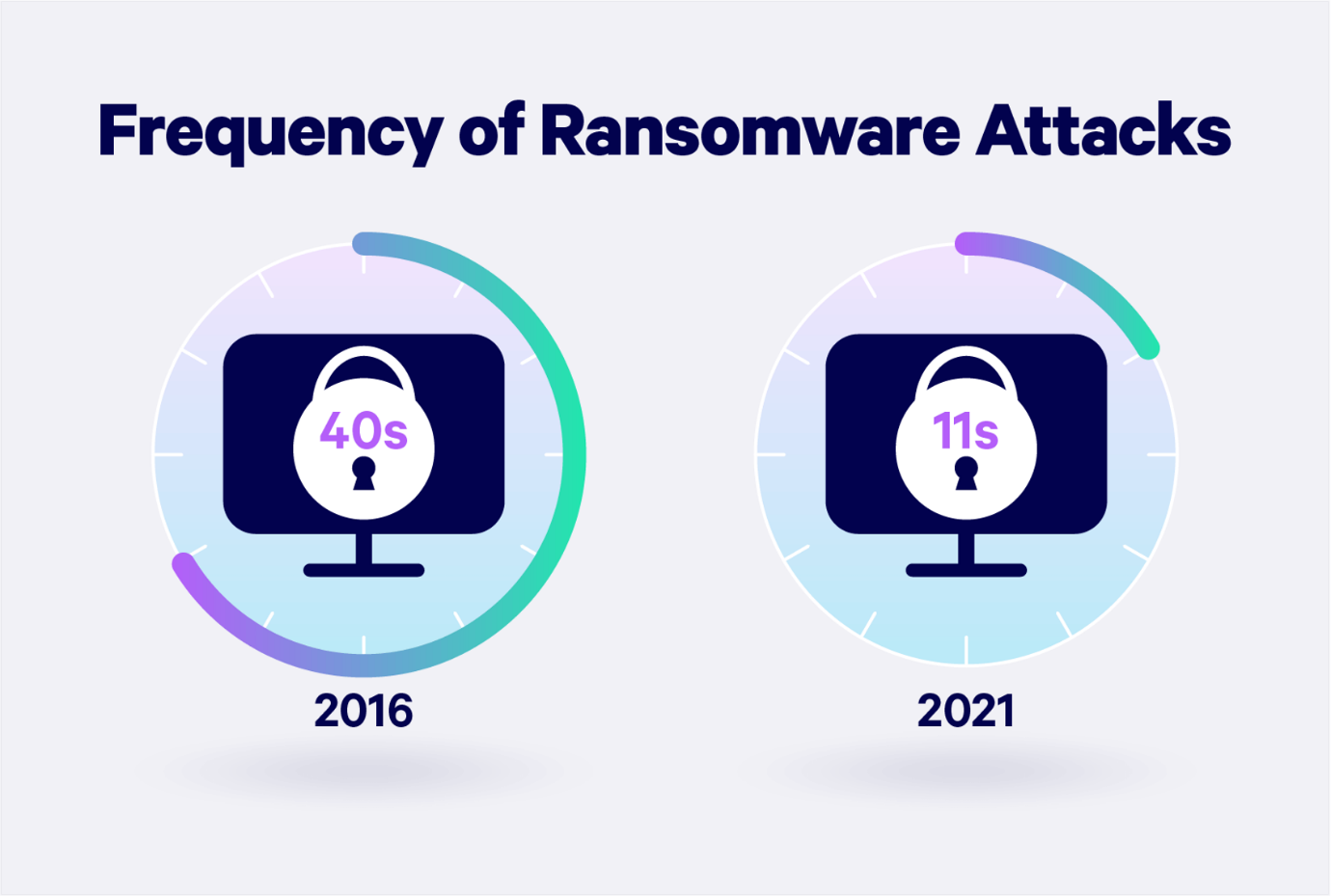
Blockchain
Blockchain is proving an effective tool for cybersecurity because of the ledger technology that makes record-keeping public, thereby increasing security. Due to the decentralized nature of blockchain, detecting hacker activity is often quicker because the system training enables it to understand hacker attempts and threats, thereby reducing cybercrime.
Let us explore trends in application security predictions for blockchain in the next 12 months.
Data transmission creates attack windows for hackers, but progress is happening in blockchain technology with the development of encryption features. Encryption can prevent hackers from accessing data. In the next 12 months and beyond, companies will use blockchain and encryption to address the data transmission gap that often creates attack points for cybercriminals.
The Keyless Signature Infrastructure (KSI) offered through blockchain is another trend that addresses encryption problems by pinpointing weak points and safeguarding the system from external threats. KSI offers scalability for enterprises by building security infrastructures and improving solutions. The distributed nodes in blockchain make privacy easier — with the personal rights of users facing threats in the current situation, blockchain addresses this problem. The decentralization of data in blockchain allows personal information to be safeguarded, and this a win for individual privacy rights on data.
Contract management is another problem in the current security technologies environment where parties disagree over terms once a deal happens. Moreover, with cyber criminals who can manipulate contracts, the distributed ledger technology from blockchain will ensure that contracts uphold principles such as not reversible. Blockchain will solve this problem by fostering smart contracts, including both parties’ tracking of contracts.
Blockchain Application Security Use Cases
MobileCoin is leveraging blockchain to enable companies to handle ledger information across networks in a simple way. Because most businesses have not transitioned to blockchain, MobileCoin is a company working to educate businesses on securing their ledgers. Coinbase implements blockchain through the storage of passwords, which requires users to provide security verification prior to accessing resources. This reduces fraud due to its strict encryption measures. Hashed Health is another organization adopting blockchain to combat security vulnerabilities, offering consulting services to enterprises on implementing blockchain technology with a focus on healthcare companies.
Lastly, the Australian government adopted blockchain technology by successfully securing public records through distributed ledger technology. Australia ranks among the top countries in the world to successfully adopt and implement blockchain technology for cybersecurity measures. More governments, including in Europe, are moving toward blockchain adoption.
Cybersecurity Systems with Artificial Intelligence and Blockchain
Data breaches in 2020 and in previous years remind us about the increasing need for security protocols to secure personal information and ensure businesses use data for the right use cases. With the privacy debate raging on every year, companies must pivot to AI and machine learning for system threat detection to consolidate network security.
Governments are also adopting security measures like Australia, using blockchain’s distributed ledger technology. In the United States, the Transportation Security Administration (TSA) is using AI to bolster security systems across all airports by comparing data from passengers. Machine learning algorithms at the TSA are improving screening processes and reducing lines while facilitating crime detection and prevention. Additionally, the collaboration between individuals and machines in Europe through the Horizon Program enabled by artificial intelligence is a new era in security training.
Conclusion
Adopting a digital
strategy starts with using AI and ML technologies for cybersecurity, real-time
data processing, and ledger technology through blockchain. The traction toward
blockchain as an alternative cybersecurity control of choice will spike in 2022
as companies become more data-driven. Businesses must create value within their
operations — and securing vital company resources with state-of-the-art security
practices and technologies is a good start.
Relevant Blogs:
LinkedIn Security Vulnerability: A Lesson for Security Engineers
Should We Target Zero False Positives?
Security Matters: Vulnerability Scanning Done Right!
Top 5 Recent Data Breaches: Causes and Lessons
Recent Comments
No comments
Leave a Comment
We will be happy to hear what you think about this post