Best Practices to Secure Your SDLC Process
Best Practices to Secure Your SDLC Process
A well-structured Software Development Life Cycle is of the utmost importance. Each phase in the SDLC requires its own set of security tools. Let's discuss!
Introduction
In the development of a robust software system, a well-structured Software Development Life Cycle (SDLC) is of utmost importance. An SDLC is a meticulously structured roadmap neatly sectioned into various phases in the software development process, allowing the stakeholders of the project to effectively collaborate and keep track of the progress—from planning to designing, and deployment to maintenance, and SDLC ensures easy evaluation at each step of the software development journey and its fool-proof execution.
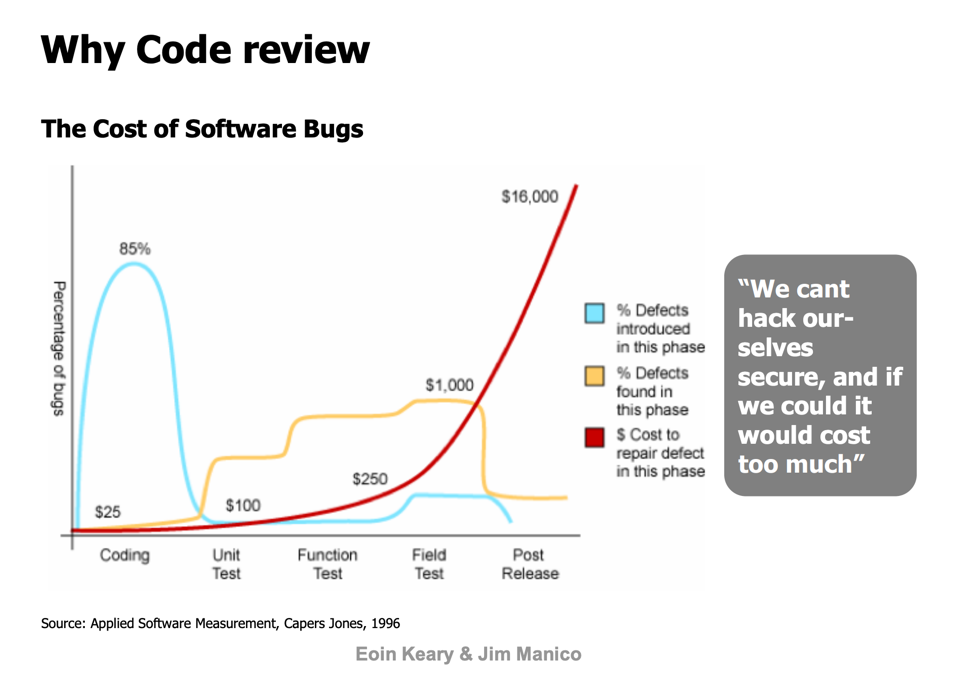
In the past, security-related tasks were limited to only the testing phase of the SDLC. As a result, several issues would get discovered very late into the process and some not at all. As a consequence, businesses were perpetually at high-security risk and the cost of software maintenance and troubleshooting would spiral out of control.
To avoid unforeseen expenses, reduce risks, deliver highly efficient software products, and increase revenue, an effective strategy has been formulated that advocates the integration of security activities across all phases of the SDLC.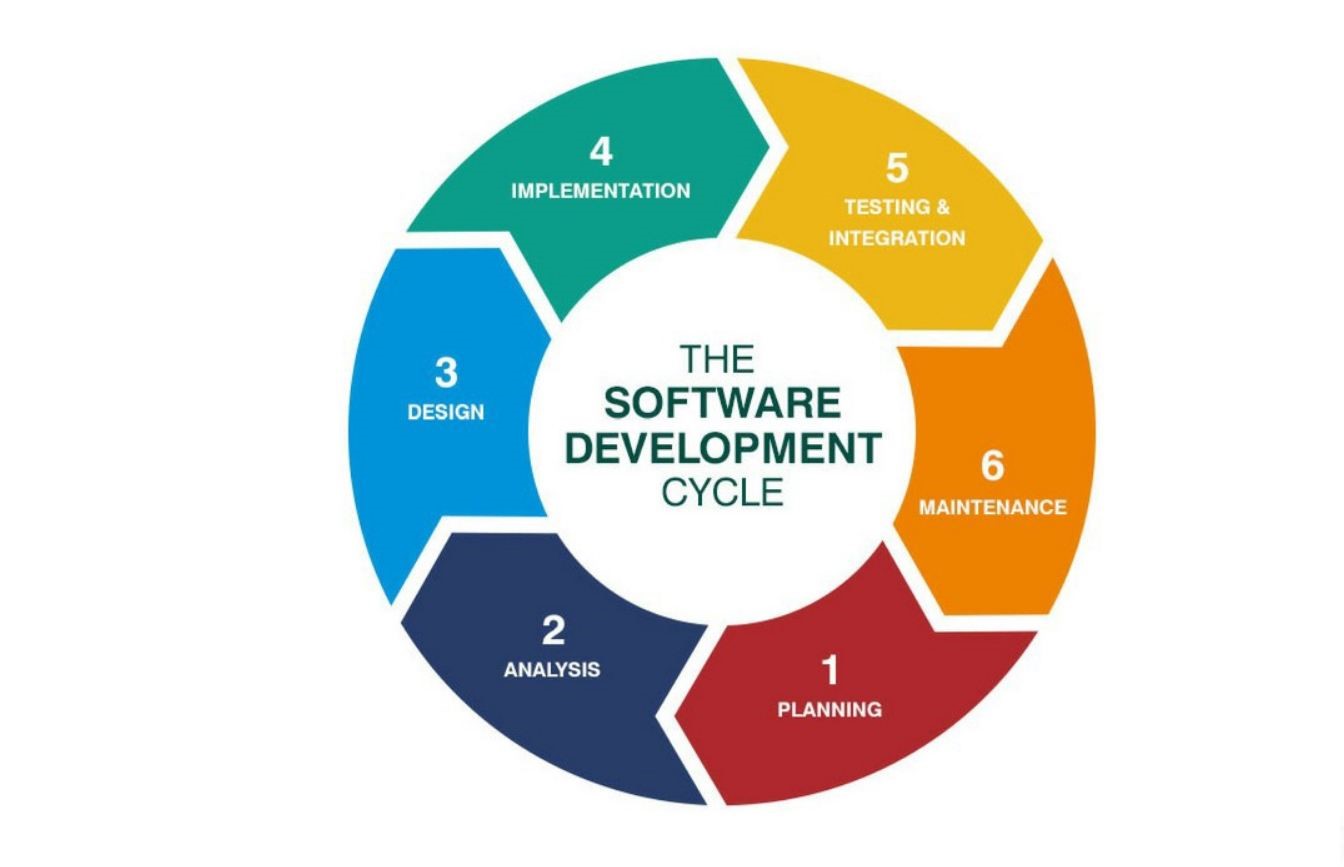
Integrating Security Across All Phases of the SDLC
Each phase in the SDLC requires its own set of security tools that need to be mapped with the teams’ IDEs, code repositories, build servers, and bug identifying tools to gauge any scope of risk and to address them as soon as they crop up.
Let us talk about the phase-wise security integration of the SDLC and the best practices:
1. Planning and Analysis
At the very onset of the software development journey, a very well-thought-out plan is a must. Upon receipt of the project requirement from the clients, security and development teams collaborate to analyze the scope of the project, calculate costs, build workflow, set deadlines, identify potential risks and ensure technical feasibility.
The stakeholders identify policies and mandates applicable to the software; decisions regarding technology, languages, and frameworks are taken, and the risks involved in the use of tools selected are evaluated.
A significant step in this phase is the architectural risk analysis that identifies security flaws in the very nascent stage of the SDLC, followed by the development of the CIA (Confidentiality, Integrity, Availability) matrix that is crucial in securing software design.
2. Architecture and Design
The second phase involves the designing of the software while adhering to the guidelines devised to address risks evaluated during the planning phase. With the help of processes such as threat modeling and architectural risk analysis incorporated early on in the design phase, vulnerabilities are addressed in advance, ensuring a successful and smooth development phase.
This phase includes a comprehensive Product Security Risk Assessment, also called ‘Static Assessment,’ which is a review of the programs from a security standpoint to identify security-related shortcomings pertaining to the design. Detected risks are then addressed by the project team.
3. Development
During the development phase, secured coding standards must be ensured. Besides the carrying out of the best practice necessary, this phase involves the training of the developers on keeping a far-sighted approach in detecting security vulnerabilities, as well as potential issues from the business perspective.
To ensure that developers abide by robust secure coding practices, guidelines should be set and awareness campaigns must be conducted regularly. A routine source code review ensures that the quality is maintained while complying with the secure coding checklist.
Threat modeling assessment is recommended in this phase as well, alongside the incorporation of static analysis tools (SAST) and dynamic analysis tools (DAST).
A Static Code Assessment is conducted in this phase to analyze the secure code of the software by deploying an automated scanning tool that functions via plugins installed on developer systems. The defects identified in this assessment are analyzed and fixed by the security team.
This analysis is carried out on every code generated to check for any security risks.
Top Secure Coding Practices Include the Following:
Inputs from untrusted resources to be checked and validated so as to mitigate the majority of risks before these inputs are used in the processes.
Strict adherence to the warnings laid out by the compiler to eliminate any construction errors in the code. Code compilation must ensure that the highest warning level is incorporated. Any warnings must be addressed by code modification [C MSC00-A, C++ MSC00-A]. To eliminate any other security-related issues, static and dynamic analysis must be conducted.
Sanitizing of all data being sent back to the user from the database
Open-source libraries to be checked for risks before being used
In the development of the software, high-level, programmer-friendly languages such as C, C++, PHP, and Java are used. These languages are comprehensible, easy to debug and maintain, and can adapt to any platform environment.
4. Verification Testing
Although security tests are carried out at every step, the fourth phase of the SDLC is the testing-only phase where rigorous assessments and analyses, such as the Dynamic Code Analysis, a kind of an Application Security Testing, also called the Open Web Application Security Project, are carried out. It assesses the operability of various features of the programs and evaluates them for any security-related vulnerabilities.
While static code analysis runs scans that identify known security loopholes, dynamic testing tools check whether the implementation of the application is secure.
Another comprehensive assessment—Vulnerability Analysis and Penetration Testing (VAPT) is carried out which assesses the binaries and helps identify risks and prevent hackers and costly data breaches.
This assessment is primarily conducted to identify the Database Vulnerabilities and Server Vulnerabilities and other vulnerabilities. Since this test forms the last stage of security assessment, it also includes thorough verification of any issues, defects, and risks that were reported earlier.
Any vulnerabilities missed out during the previous phases, are eliminated in the verification testing phase, a testing process that is thorough and robust and generally conducted during run-time to assess software applications for security loopholes more accurately.
To ensure high efficiency, scanners need to operate effortlessly, without much being invested in their maintenance and should record a low number of false positives.
There are quite a few robust, lightweight, and efficient scanners available, such as Arachni, W3AF- Web Application Attack and Framework, Acunetix, etc.
5. Deployment
In the deployment phase, monitoring of the product is carried out both in its production and post-production environment. Under production, the developed software is tested again. When deployed, all identified issues and vulnerabilities are addressed.
6. Maintenance
Even after an extensive process of integrating security at each level of SDLC, there is always a scope of new vulnerabilities to crop up. Therefore, teams need to be ever-ready to tackle them and continuously update products to keep them from being compromised.
The following must be kept in mind for successful completion of the project:
1. A robustly secured SDLC is a result of various initiatives, such as:
a. Secure coding guidelines
b. Extensive training on awareness and secure coding imparted to the developers
c. Keeping remediation SLAs in place that will demonstrate how quickly the issues need to be identified and fixed
2. Simplified requirements for the developers: To ensure an error-free and strongly secured SDLC, it is essential that client requirements are comprehensible for the developers. All the security recommendations and guidelines should be clearly stated so as to avoid any ambiguities during the execution of the processes.
3. Incorporating industry standards on security: Developers must adhere to the standard industry compliance practices and policies to ensure that no scope for error remains unaddressed.
4. Assigning responsibility roles for software security: A security team must be appointed to carry out quality checks such as threat modeling from time to time and to assess each and every aspect of the software development
5. Selecting a good software architecture: A good software architecture is key to a robustly secure SDLC. A strong software architecture that has the right architectural pattern and defines quality attributes, such as scalability, resolvability, adaptability, resilience, etc. thoroughly assesses the software system before it is developed, helping in mitigating risks and preventing cost overruns.
Conclusion
A secure SDLC with code reviews, penetration and architecture analyses ensure that the security of the product is robust throughout the development process.
A secure SDLC, with security enforcement tools mapped into and security assessments such as code review, penetration testing, and architectural analysis carried out in each step, empowers the developers to create an innovative product that is much more secure than it could ever be if only traditional methods were to be used in the SDLC.
Needless to mention, the expenses involved in remediating post-production security vulnerabilities are much higher as opposed to tackling those in the nascent stages SDLC.
ZippyOPS Provide consulting, implementation, and management services on DevOps, DevSecOps, Cloud, Automated Ops, Microservices, Infrastructure, DataOPS, and Security
Services offered by us: https://www.zippyops.com/services
Our Products: https://www.zippyops.com/products
Our Solutions: https://www.zippyops.com/solutions
For Demo, videos check out YouTube Playlist:
https://www.youtube.com/watch?v=4FYvPooN_Tg&list=PLCJ3JpanNyCfXlHahZhYgJH9-rV6ouPro
If this seems interesting, please email us at [email protected] for a call.
Relevant Blogs:
Recent Comments
No comments
Leave a Comment
We will be happy to hear what you think about this post