Establishing Kubernetes Governance Strategy

Kubernetes governance implements policies for cluster allocation, deployment, redeployment, and scaling. Let’s understand in detail why we need Kubernetes Governance.
Governance is all about bringing consistency and repeatability, ensuring quality never gets deprioritized. Mapping out a Kubernetes governance model helps in keeping the entire organization on track. Furthermore, policies proposed in the Kubernetes governance model are not meant to be limited to security baselines of resources and deployments.
However, the real question is – in our cloud-native journey, Where and Why we do need Governance and Policy for Kubernetes?
Yes, Kubernetes offers Role-based Access Control (RBAC) feature, which helps define accesses in a very granular manner. Thereby differentiating between the level of access possessed by an Operator or Administrator.
The limitation of RBAC is that it doesn’t enable us to set limits on resource usage. Setting these limitations on resources is essential in defining policy boundaries.
Let’s dive right into the blog to understand Kubernetes Governance and its significance.
What Is Kubernetes Governance?
We all understand ‘governance,’ the ability to enforce certain rules and policies across all groups, departments, and/or the entire organization. Similarly, when talking about Kubernetes governance, we’re referring to specific standards being followed across all Kubernetes clusters and also to the applications running on them.
It’s easier to understand that we want standard processes to keep things predictable and secure. When you have fewer clusters, and one person is handling all of them, incorporating standardization might look a little too much. Yet, with time it translates into putting in great effort in maintaining the clusters.
Here, let’s take a break and understand what are the dimensions of governance. And how we can prevent having too many overlapping policies.
Dimensions of Governance
There are three dimensions to Kubernetes governance.
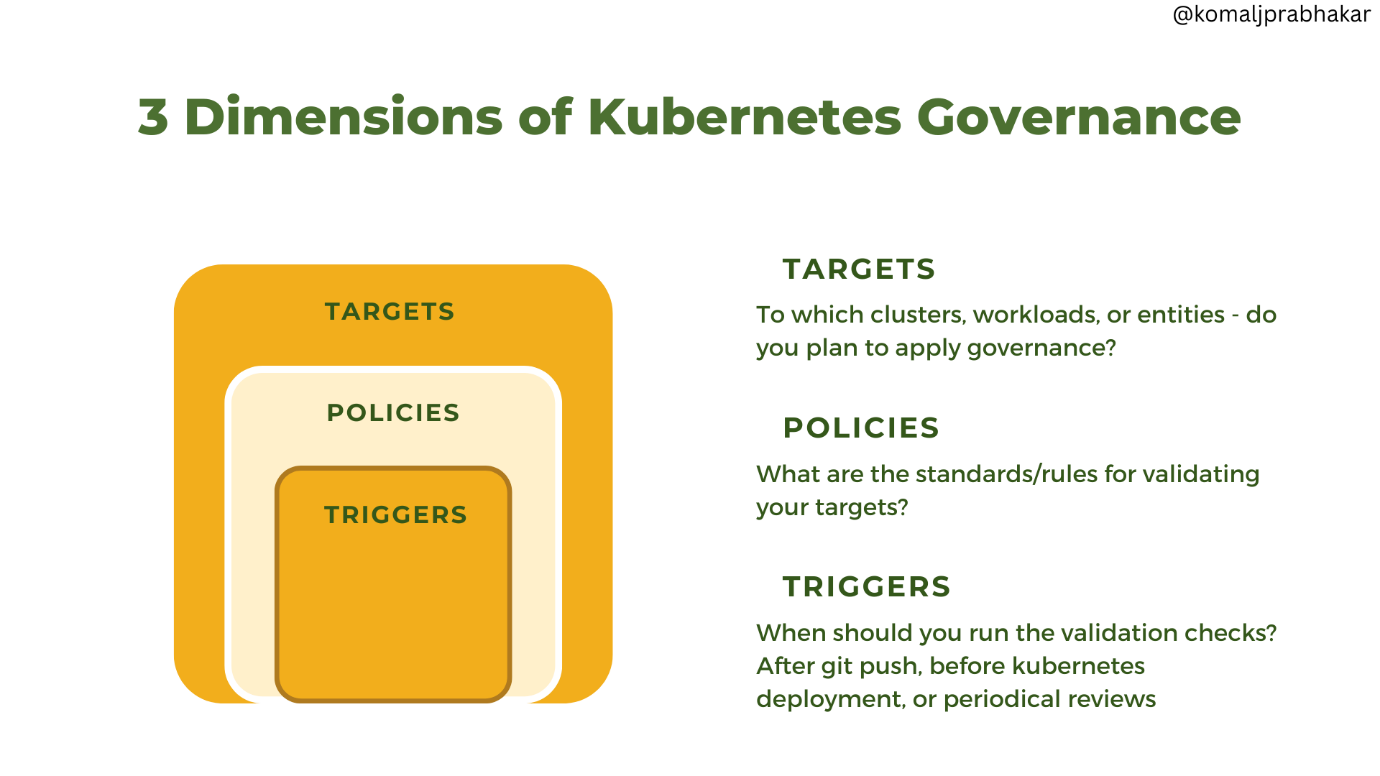
Dimensions of Kubernetes Governance.
It needs to be implemented in terms of organizational units and technical units. The organizational unit consists of users, groups, teams, and departments.
The technical units comprise cloud providers, data centers, regions, groups of clusters, label selectors, namespaces, etc. The scope can also be defined in terms of capabilities ranging from static lists to dynamic rules.
Coming to policy targets, there’s a lot to explore in terms of security policies, image management, networking policy management, and Configuration constraints and policies. Let’s understand them in detail.
What Are the Governance Targets?
We can divide Kubernetes governance targets into the following categories:
- Security Policies
- Container Image Management
- Networking Policy Management
- Access Administration and Management
- Configuration Constraints and Policies
Security Policies
When we’re talking about security policies, there are various
areas that our Ops Team needs to have control of.
Framing security settings that ensure –
- Who will have access to the cluster or app?
- Customizing accesses for different departments.
- Specifying the extent to which OS capabilities are used by applications.
For instance, how all this should work is like for all the clusters created by the data science department, the users will be able to access only a specific default namespace.
Container Image Management
Another governance area would be Image Management. In this case, organizations can make a set of rules which say –
- The type of container images to use in which clusters.
- What are the criteria for using a container image for the production environment?
- Regulation criteria for container registries to opt for and how to prevent them from being compromised.
Networking Policy Management
Organizations need to focus on defining which pods or containers
can communicate with each other. Simply put, we need to ensure pod security
constraints through governance. There might be cases where security frameworks
do solve this.
It’s always good to have a common governance framework that covers security as
well as other areas, such as cluster topology and general cluster configuration
constraints.
Access Administration and Management
Bringing in the popular concept of RBAC i.e., Role-based Access Control Policy.
Through this, we, as Admins, can limit access to the Kubernetes clusters. There
are various Kubernetes objects that play a role in defining the RBAC policy,
like Role, ClusterRole, RoleBinding, and ClusterRoleBinding. With them,
we can define the access limitations in detail.
Configuration Constraints and Policies
This is about defining resource configurability rights and also resource access and limits. How this works is – suppose we have different software teams. Through our policies, we have allowed team A to create clusters on Azure and AWS, where we have defined the limits up to which team A can utilize resources. Point to be noted that team A cannot change these configuration specifics.
Governance rules related to deployed applications are pretty much similar to the security rules discussed above. These include networking policies and defining how pods can interact (known as application-level constraints). Resource usage, requests, and limits for all applications can also be constrained.
Importance of Kubernetes Multi-cluster Management and Governance
Prime advantages of implementing multi-cluster management and governance include –
- Reduced Management Complexity – When engineering teams comply with a set of rules, it’s easier to prevent any form of wastage/over usage.
- Enhanced Cluster Visibility – Better workload management and enables optimal usage of resources. Prevents uneven application pod distribution across our nodes.
- Better Application Availability – It’s easier to deploy our application in the nearest available zone
- Improved Monitoring and Logging – Easier troubleshooting of issues. Minimizes downtime.
- Ensured Conformance and Compliance – Employees abiding with the defined policies bring uniformity and make things predictable.
- Reduced Latency – With robust monitoring in place, it’s easier to predict any aberrations and makes us better prepared.
- Improved Disaster Recovery
- Enables us to deploy legacy and cloud-native applications across Multi/Hybrid Cloud Environments.
- Standardization with built-in automation to reduce operational costs and improve efficiency.
- Enhanced Security Posture – with all-around visibility, centralized control, consistency, and standardization.
How to Implement Kubernetes Governance Framework?
Before that, we need to understand – What a Kubernetes Governance Framework looks like?
It combines multiple specialized governance frameworks into one comprehensive solution. This includes going for different tools that work for different objectives like cloud cost management, cloud resource management, observability and monitoring, security, etc. The problem with one comprehensive solution is that these different tools don’t necessarily communicate and integrate with each other.
The best approach is to go for a Kubernetes Management Platform. A low-code platform that follows the best practices regarding security, observability, cost management, etc.
Best practices for Security
- A
robust image scanning process integrated
within the CI/CD pipelines ensures every enterprise application is scanned
during the build and run phases of the SDLC.
- Using
tools that work in line with CIS
Benchmarks (Center for Internet Security benchmarks).
-
Restricting
access to
confidential systems or data.
- Manages
digital authentication credentials (secrets) better with tools like HashiCorp Vault.
Best Practices for Monitoring and Observability
- Monitoring
strategy that focuses on giving granular visibility of what is happening
inside the Kubernetes cluster.
- Automated service discovery that
performs detailed application monitoring and provides action-oriented
recommendations in real time.
Best Practices to Mitigate Networking Challenges
A custom setup that supports –
- Container Networking Interface (CNI) – As the complexity of service communication increases, so does the vulnerability to security threats. A CNI plugin to inset a network interface into the container network namespace.
- Deploying the “convention over configuration” by creating Public and Protected Ingress.
- Deploying a service mesh that integrates with the infrastructure layer of the application. Thereby making the communications between services over the network secure and reliable.
Cloud Cost Management Practices
- Cost
Optimization with Spot
Instances (AWS)/ Spot VMs (Azure)/ Preemptible VMs (GCP):
For tasks that are not mission-critical can run on spot instances. An
intuitive platform supports here by ensuring that the data doesn’t get
deleted when these instances are withdrawn.
-
Downtime
Scheduler:
For all the environments that are running without purpose can be shut
down, saving infrastructure costs.
- Use
of ReplicaSet that
guarantees the availability of a specified number of identical Pods at any
point in time.
Wrapping Up
By prioritizing Kubernetes governance, enterprises are implementing the necessary guardrails to protect their most prized assets with success. Furthermore, it helps them in achieving scalability, which makes them more secure and robust.
Thanks for reading, and happy measuring!
We Provide consulting, implementation, and management services on DevOps, DevSecOps, Cloud, Automated Ops, Microservices, Infrastructure, and Security
Services offered by us: https://www.zippyops.com/services
Our Products: https://www.zippyops.com/products
Our Solutions: https://www.zippyops.com/solutions
For Demo, videos check out YouTube Playlist: https://www.youtube.com/watch?v=4FYvPooN_Tg&list=PLCJ3JpanNyCfXlHahZhYgJH9-rV6ouPro
If this seems interesting, please email us at [email protected] for a call.
Relevant Blogs:
A Comprehensive Guide to Cloud Application Security Audits
How to Build Security for Your SaaS User Communications
17 DevOps Metrics You Should Be Tracking
Why Kubernetes Observability Is Essential for Your Organization
Recent Comments
No comments
Leave a Comment
We will be happy to hear what you think about this post