Integration: Data, Security, Challenges, and Best Solutions

Explore the essentials of integration and lays a theoretical foundation for integrating systems using cloud and on-premises.
This article highlights the scope of the integrations extends to data and systems integration and explains why it requires the incorporation of both technical and non-technical domains. Explore the essentials of integration and lays a theoretical foundation for the integration of systems using cloud and on-premises. It reviews its definition, players, detailed info on issues that are expected to be addressed, and effective solutions. It will introduce the Safety Cube theory to outline these fundamental aspects of data and system integration. Example applications are provided at the end of the article.
Whether it is on-premises or cloud integration depends on how well you define the process and can be able to get all of your data together in one place. The interface will enable you to achieve this.
Interfaces are becoming not expensive and user-friendly to design with the available advanced tools and software coming into the computer industry. They can decrease a decent portion of the cost of any system implementation project.
Managing integrity between multiple data sources is becoming easy and effective nowadays with cloud computing solutions. There will most likely be real-time, transactional transactions during the integration.
Replications and fetching information between systems using cloud platforms need to be elaborate.
Simple Architecture
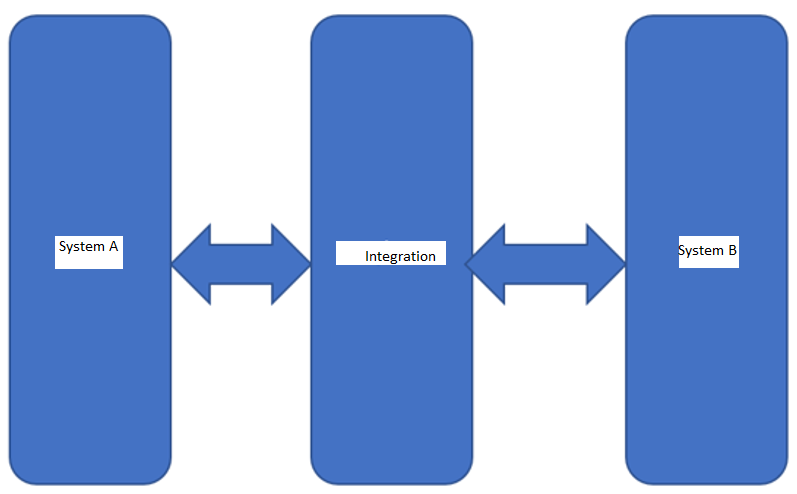
Description and Players
Integration of data using cloud and on-premises platform benefits not only customers but the health of the business. This is an improvement compared to performance, depending on the product line. These results are the combined result of heroic effort and scalable processes.
Today, integration solutions-focused teams are divided into many divisions: Reactive Support, Product Support, and Easy solutions.
Deployment Models in Cloud
- Public Cloud (or External Cloud): In this model, computing resources are dynamically provisioned over the Internet via web applications or web services from trusted third-party providers. Public clouds are run by third parties, and applications from different customers are likely to be mixed together on the cloud’s servers, storage systems, and networks. Although the public cloud has compelling advantages, there exists the hidden risk of security, regulatory policy compliance, and quality of service (QoS) requirements.
- Private Cloud (or Internal Cloud): In the private cloud deployment, computing resources are used and controlled by a private enterprise. It is generally deployed in the enterprise's data center and managed by internal personnel or service provider. The main advantage of this model is that the security, compliance, and QoS are under the control of the enterprises.
- Hybrid Cloud (or Mixed Cloud): The Hybrid Cloud environment intersects and combines multiple public and private cloud models. It enables the enterprise applications to run the state-steady workload in the private cloud and request the public cloud for intensive computing resources when peak workload occurs. Hybrid clouds introduce the complexity of determining how to distribute applications across both a public and private cloud.
- Community Cloud (or Group Cloud): In this Community deployment model, several organizations jointly construct and share cloud infrastructure as well as policies, requirements, values, and concerns. The cloud community forms a degree of economic scalability and democratic equilibrium. The cloud infrastructure could be hosted by a third-party vendor or within one of the organizations in the community. This is an emerging cloud used by many social networking websites like Facebook, Orkut, etc.
The integration team is critical to the success of any company, especially high demanded sectors. Cloud hosting services maintain retention records, which can be anywhere for comparable products.
API: APIs are the foundation of digital transformation. Whether developing applications in cloud-native and serverless architectures or providing a backend for applications, APIs enable the exchange of data and communication between applications and databases.
Example:
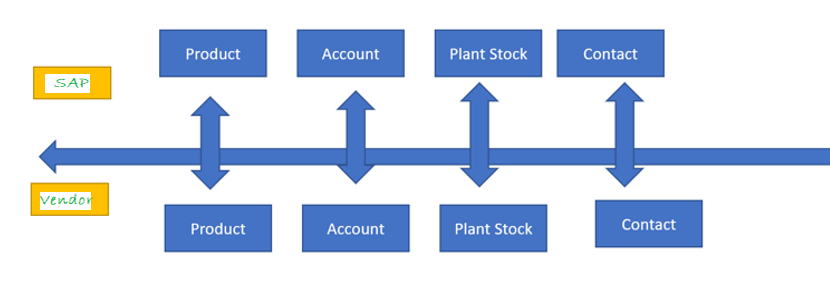
Uses Integration (Cloud or On-Premises)
- Effective and productive technology infrastructure.
- Easy to integrate with maximum efficiency and flexibility.
- Maintenance of software and hardware.
- Cost-effective
Integrations Issues and Reasons
Motivated attackers are increasingly targeting Data, Systems, or APIs as the pathway to their target’s underlying infrastructure and database; there might be a critical threat to an organization’s sensitive data. What's more, security teams don't often have visibility into the Interfaces and APIs that technical teams are creating or deploying, making them a dangerous blindspot.
Integration or API Security empowers customers to protect critical applications and infrastructure from online fraud, API abuses, DDoS attacks, and more.
It is required that API Security should automatically detect API endpoints to enable comprehensive API visibility for security teams. There should not be manual intervention in the creation of a positive security model.
Security uniquely solves two significant challenges that every business faces today: protecting the APIs that enable innovation while monitoring and securing the underlying data. This differentiated ability brings to life protecting data and all paths to it.
Integration and API Security bridge the gap between the domains by providing holistic visibility in a SaaS that can be quickly deployed in any environment.
If organizations overcome security issues will be a significant achievement that paves the way for a new standard in security SaaS products to deliver value beyond the security team and enable secure innovation within the development lifecycle.
Security During Integration
Several functionalities would help to eradicate data silos by having a centralized interface of information to improve processes and workflows.
There are multiple data touchpoints that need to be assessed and monitored from a security and compliance perspective.
Some of the key areas are:
- Cyber Intelligence Discovery
- Monitoring and Vulnerability Assessment
- Assets Level Monitoring
- Network Monitoring
The best security options for data during integration are using encryption/decryption and two-factor authentication.
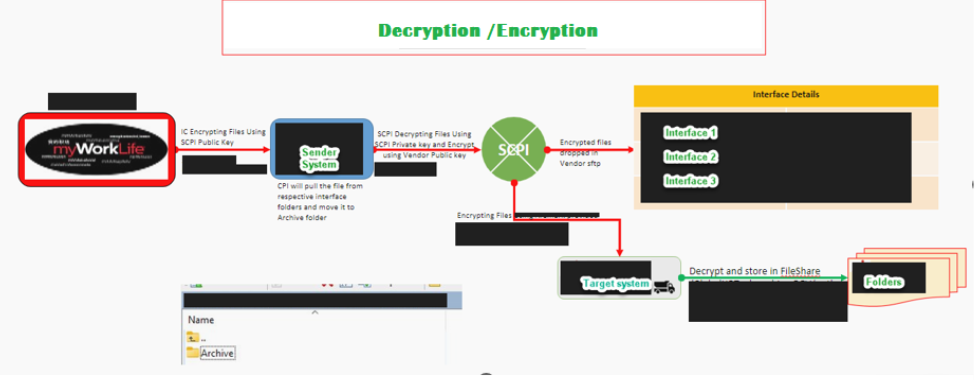
Decryption/Encryption
There is a lot of unique code decrypter and encrypt tool available that helps to decrypt or encrypt data with different encryption algorithms.
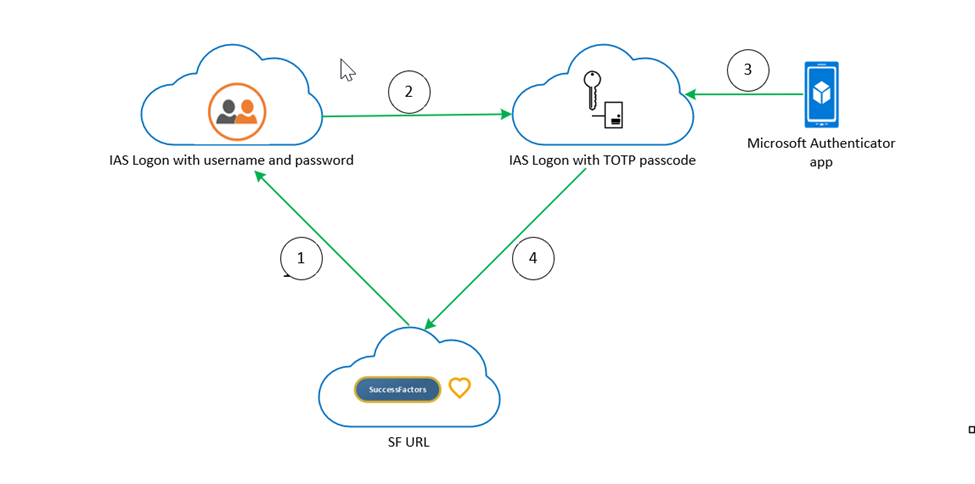
Two-Factor Authentication (TOTP)
Two-factor authentication is a process where a user is prompted during the sign-in process with a password for an additional form of identification. The Authenticator application displays the time-based, one-time passwords (TOTP) help to safeguard access to data and applications of the target system while maintaining password login users. It acts as an extra layer of security checks to verify a user’s identity by requiring a second form of authentication. You can also use many authenticators such as Microsoft, SAP, or Google Authenticator.
Conclusion
Companies should try to develop shelf-sufficient integration services of their own with absolute safety and security measurements of data. Various functionalities are available to design and facilitate integration with new as well as existing applications and systems. The main purpose of this document is to understand the features, issues, and availability of the best solutions related to data and system integrations. Overall, the integration of area-hosted applications produced incredible results throughout the years. The Integration technology increased customer satisfaction in the face of a massive organizational overhaul.
We Provide consulting, implementation, and management services on DevOps, DevSecOps, Cloud, Automated Ops, Microservices, Infrastructure, and Security
Services offered by us: https://www.zippyops.com/services
Our Products: https://www.zippyops.com/products
Our Solutions: https://www.zippyops.com/solutions
For Demo, videos check out YouTube Playlist: https://www.youtube.com/watch?v=4FYvPooN_Tg&list=PLCJ3JpanNyCfXlHahZhYgJH9-rV6ouPro
If this seems interesting, please email us at [email protected] for a call.
Recent Comments
No comments
Leave a Comment
We will be happy to hear what you think about this post