Is Windows 11 Safer Than Windows 10?

Let's take a look at what Microsoft has changed in terms of security and privacy in its operating system. Does Windows 11 protect users’ data better than Windows 10?
Windows 11 is already here. Let's take a look at what Microsoft has changed in terms of security and privacy in its operating system. Does Windows 11 protect users’ data better than Windows 10? How does Windows 11 resist cyberattacks?
Windows 11 was released on October 4, 2021. Earlier it produced plenty of hype with its version for testing. Even a simulator was created. I would like to note that this article was prepared before the official release of the new OS version. Some functions could have been changed, removed, or improved as it happened for example, with the minimum system requirements. Initially, Windows 11 was not intended for everyone (at least 8th generation Intel processors were required). However, the Windows community found a way to bypass the installation lock. Microsoft decided that it would not take action to restrict installations. In its blog, the corporation disowned possible problems, including problems with drivers on old PCs.
New Security Features in Windows 11
With each new release of Windows, Microsoft states that it wants to focus on the security and stability of the operating system. And it happened this way again. System requirements were increased. They touch upon not only the computing power but also the PC hardware. Apparently, it looks like Microsoft plans to shield its users from vulnerabilities that allowed ransomware viruses to spread over the past few years.
Trusted Platform Module 2.0
TPM, or Trusted Platform Module, is an optional security component. It can store information in a protected form (the specification is not fully disclosed). In the case of Windows, it helps with storing BitLocker encryption keys.
The module is supplied either soldered on the motherboard or as a separate physical element. In the second case, you need to consider the motherboard compatibility. Many modern processors have a program for emulating this device. And here comes the most interesting thing: to install Windows 11, this module is required, but its form is not specified.
It follows that either a module or a new processor is needed.
Considering that there are already publicly available programs that can guess the BitLocker password, Microsoft had to strengthen the protection and try to prevent data leaks. But, on the other hand, the company did not give a choice to other users who place their data in cloud storage or do not care about their safety and privacy. This is also true for companies that are not keeping pace with the times and have only recently completed the transition to Windows 10.
Anyway, it is worth checking the availability of the TMP module on your computer. To do this, you can press "Win+R" and type: "tpm.msc". The "Trusted Platform Module (TPM) Management on Local Computer" window will open. If there is a module, its settings will be displayed.
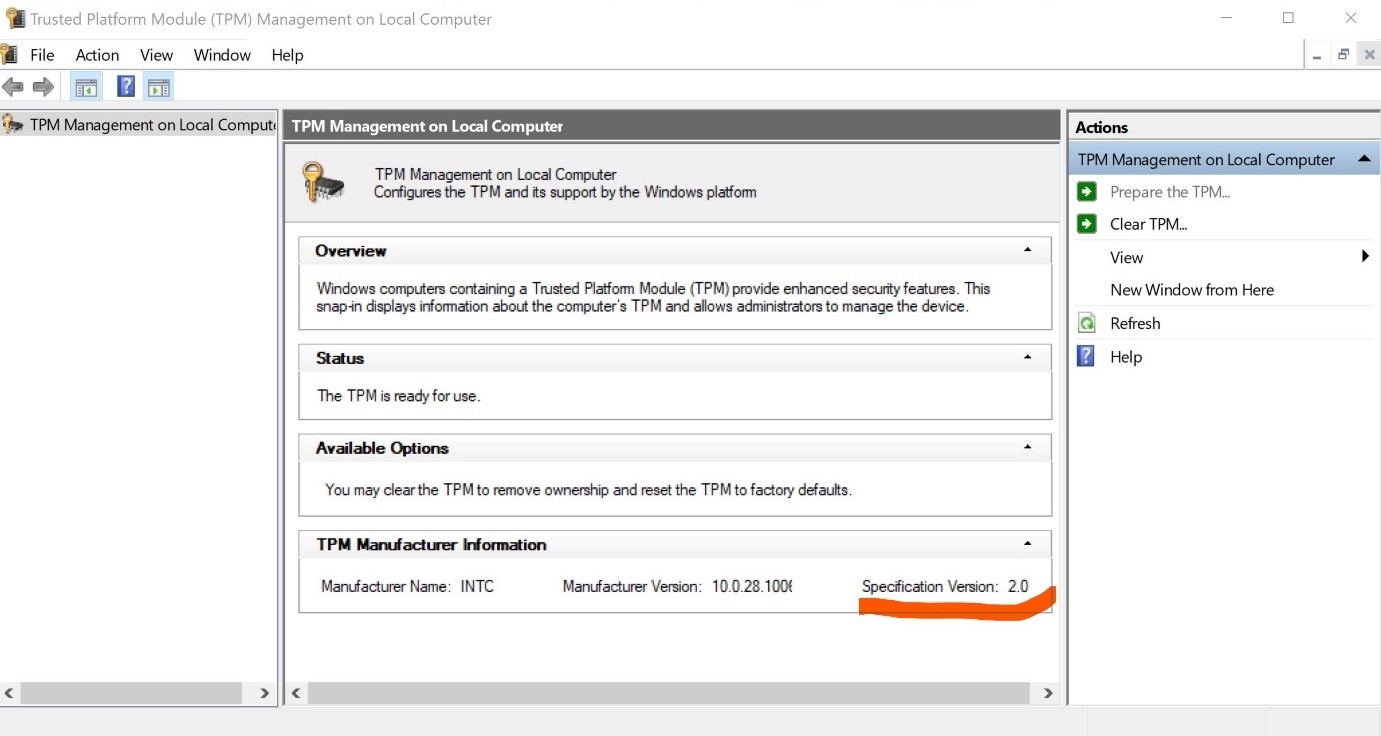
In the lower right corner of the window, the version number is displayed, which, according to the requirements, should not be lower than 2.0. If this is not the case, then either the emulation program in the BIOS is turned off, or it will not be possible to install Windows 11 "legally."
I can also say that with TPM emulation and processor virtualization enabled, Windows 11 can be installed on virtual machines without problems.
Windows Secured-Core PC
Attempts to create the most secure Windows device on the market are still just attempts. But these are the words Panasonic uses when it comes to Windows Secured-Core PC.
What is Secured-Core? In fact, there is no Core actually, but only the name. Protection is spread across individual services. It consists of two parts:
1. Protection based on Windows software.
2. Protection based on hardware and its components.
The software part, in turn, includes the following elements:
- Virtualization-based Security (VBS)
- Hypervisor-protected code integrity (HVCI)
- Secure Launch - the Dynamic Root of Trust for Measurement (DRTM)
- Windows Hello
Hardware-based protection is primarily comprised of TPM 2.0. Each manufacturer independently decides which protection methods to apply and cooperates with Microsoft to make it all work (biometrics, fingerprints, etc.)
Such out-of-the-box PCs come with everything preinstalled and configured. Windows 11 will also be included in this pipeline. However, it is not entirely clear why the above is listed among the new security elements of the operating system. All this is not new at all and was already present in Windows 11.
Windows Hello
People in Microsoft believe that traditional passwords are insecure because they are difficult to remember. Therefore, users either choose passwords that are easy to guess or write down their passwords. Windows Hello is designed to provide "passwordless" protection for PCs and accounts.
Windows Hello is actually a biometrics tool. Many laptops, ultrabooks, and other mobile devices are equipped with special cameras or fingerprint readers.
However, in practice, this technology has several disadvantages:
- You still have to set and remember the password. And it should be a cryptographically strong combination. Yet, at the moment, this is the last layer of protection.
- In case of unsuccessful attempts to read biometrics, Windows prompts you to enter a PIN-code, which consists of numbers. Due to the limited number of characters (there are only 10 of them), it is not very difficult to launch a brute-force attack and guess the PIN code. And we know that people use simple combinations.
- This solution is aimed more at home users than enterprises; otherwise, many businesses will have to equip desktop PCs with biometrics readers.
It is also worth noting that this approach has long been introduced in Windows 10. It is strange to apply the word "new" to it.
Microsoft Azure Attestation
Azure Attestation is a mechanism for checking the integrity and reliability of software. This check happens when you add a provider. You can read more about it here. The description of this system is dated the second half of 2020.
Windows 11 Telemetry
Windows telemetry has been rumored since the release of version 10. Many people believe that Microsoft collects sensitive data that can identify a person. This is partially true, but only partially.
According to the corporation, Microsoft uses telemetry data to identify security and reliability problems. This allows to analyze and fix software problems and improve product quality in the future. That is, telemetry is system data that is loaded by the Connected User Experience and Telemetry component, also known as the Universal Telemetry Client (UTC). This feature runs as a service called DiagTrack.

Before moving on to the description of the telemetry in Windows 11, I would like to figure out whether Microsoft can actually identify a person.
When installing Windows, it gives you the right to select data that will be transmitted as telemetry. With most settings enabled, yes, Windows collects enough data to know almost everything about the user.
If you narrow telemetry settings, the collection process is structured in such a way that the component dealing with this tries to avoid collecting information that can directly identify a person. But when Windows or an application crashes or hangs, the memory contents of the process that caused the crash is included in the diagnostic report, and this crash report may contain sensitive information.
When installing Windows 11, it allows you to disable sending the following data:
- Location.
- Diagnostic data (It includes info on visited websites and applications used. There is a note here that this is considered additional information and that there is also mandatory information that cannot be disabled).
- Handwriting and keyboard input.
- Personal diagnostic data.
- Advertising ID.
It turns out that if you do not disable the transmission of this telemetry, then Microsoft will know the user's location, visited sites, data entered using the keyboard, preferences, etc. But again, Windows 10 has already prepared us for this.
If you do not disable most telemetry, you can track the list of open connections by using the TCPView program.
If you compare open connections in Windows 11 and Windows 10, you can clearly see a stable set of connections involving 20.190.120.* IP addresses. Whois lookup says they all belong to Microsoft. From time to time, multiple connections appear and quickly close.
Of course, we should not forget that "svchost.exe" is responsible for almost any data transfer, for example, downloading updates. However, after long observation on both versions of Windows, DiagTrack data transfer can be noticed.
Conclusion
In this article, I analyzed the claimed security features of Windows 11. In my opinion, the word "new" cannot actually be applied to them. There are no significant innovations (like Windows Defender in version 10).
Windows 11 may become more stable as Microsoft has reduced the list of allowed processors, but this looks more like a race with Apple in stability and performance. Both companies now create software for specific hardware.
As for telemetry, everything remains the same as in Windows 10. It can be partially disabled. If you want to disable it completely, you will have to catch the data transfer and block it with third-party software. Besides, Microsoft tacitly declares that there are mandatory diagnostic data, the transmission of which cannot be disabled. All this is transmitted in encrypted form, so only Microsoft should know what is inside these packages.
We ZippyOPS, Provide consulting, implementation, and management services on DevOps, DevSecOps, Cloud, Automated Ops, Microservices, Infrastructure, and Security
Services offered by us: https://www.zippyops.com/services
Our Products: https://www.zippyops.com/products
Our Solutions: https://www.zippyops.com/solutions
For
Demo, videos check out YouTube Playlist: https://www.youtube.com/watch?v=4FYvPooN_Tg&list=PLCJ3JpanNyCfXlHahZhYgJH9-rV6ouPro
Relevant Blogs:
Kubernetes Logging in Production
Getting Started With Kubernetes In 2 Days
What Managed Kubernetes Service is Best for SREs?
What Keycloak Is and What It Does?
Alfred Jones says: