Linux jump host for Linux node

To connect with Linux Target Server through Linux Jump Host From Ansible Controller.
Basically, Ansible will connect to Linux using SSH.
Secure Shell (SSH) includes several tricks up its sleeve. One particular trick you may not know about is the ability to use a jump host. A jump host is used as an intermediate hop between your source machine and your target destination. In other words, you can access X from Y using a gateway.
There are many reasons to use a jump server. For example, Jump servers are often placed between a secure zone and a DMZ(demilitarized zone). These jump servers provide for the transparent management of devices within the DMZ, as well as a single point of entry. Regardless of why you might want to use a jump server, do know that it must be a hardened machine (so don't just depend upon an unhardened Linux machine to serve this purpose). By using a machine that hasn't been hardened, you're just as insecure as if you weren't using the jump.
Prerequisites
Make Sure Ansible Installed With 2.9 Version
Ansible server
Linux server (jump host)
Linux target server
Ansible server
SSH key for connecting from Ansible server to the jump host. This can be user /root key
[root@ansible~]ssh-keygen
Generating public/private rsa key pair.
Enter file in which to save the key (/root/.ssh/id_rsa):
Enter passphrase (empty for no passphrase):
Enter same passphrase again:
Your identification has been saved in /root/.ssh/id_rsa.
Your public key has been saved in /root/.ssh/id_rsa.pub.
The key fingerprint is:
SHA256:Up6KjbnEV4Hgfo75YM393QdQsK3Z0aTNBz0DoirrW+c [email protected]
The key's randomart image is:
+---[RSA 2048]----+
| . ..oo..|
| . . . . .o.X.|
| . . o. ..+ B|
| . o.o .+ ..|
| ..o.S o.. |
| . %o= . |
| @.B... . |
| o.=. o. . . .|
| .oo E. . .. |
+----[SHA256]-----+
[root@ansible~]ssh-copy-id [email protected]
here, 192.168.0.35 - Jump host IP
Linux server
SSH key from jump host to all target servers. This can also be either user or root key.
[root@jump~]ssh-keygen
Generating public/private rsa key pair.
Enter file in which to save the key (/root/.ssh/id_rsa):
Enter passphrase (empty for no passphrase):
Enter the same passphrase again:
Your identification has been saved in /root/.ssh/id_rsa.
Your public key has been saved in /root/.ssh/id_rsa.pub.
The key fingerprint is:
SHA256:/DgUTD3nYZmgi+36frJGvg1Bj5JKQSoPS96zoGf+WHw [email protected]
The key's randomart image is:
+---[RSA 2048]----+
| . .... o |
| o o .o * |
|o.. . = = . |
|o=. . * = . |
|.o.o. + S . |
|. .oo. +.+ |
|. o.+ Eo= . |
| + o . .++. |
| o.. .+==. |
+----[SHA256]-----+
[root@ansible~]ssh-copy-id [email protected]
Here, 192.168.0.71 - target server IP
For security reasons, it is advised to use the user key from the jump host to target servers. If you set up the root key, any user who can become a root user jump host can access these servers and can do anything.
use 2 different users for this purpose.
ex: user1 can be used for SSH from Ansible server to jump host and user2 can be used for connecting from jump host to all target servers.
You must export the jump host private key file (SSH Key2) and copy it into a safe location in the Ansible server.
[root@jump~] scp id_rsa [email protected]:home/zippyops/id_rsa
Here, 192.168.0.143 - Ansible server IP
Configure Ansible
Now you have to configure /etc/ansible/ansible.cfg file enters the path of the private key file you copied from the jump host.
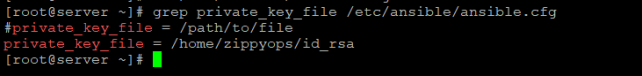
This is all you need to do as a configuration change.
Update Host Variables
You now need to update host variables.
Create a new file vi hosts_test
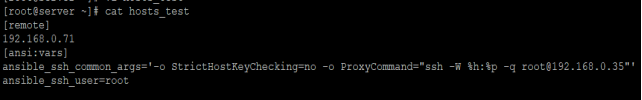
ansible_ssh_common_args and ansible_ssh_user. The common argument parameter will define SSH proxy for all hosts defined under that host group. If you want strict host key checking to be enabled, you can remove the line -o StrictHostKeyChecking=no, as shown above. Otherwise, you can leave that as it may help if you have any failure with running playbooks.
In this lab, we are used root user for Ansible host to jump host. So, SSH Key1 is a root user key.
Now, we have defined a parameter ansible_ssh_user. This will tell Ansible that when you connect from jump host to target servers, use that user. If you don’t define any user here, Ansible will assume that you are running the command as the root user. If you want to run as a root user, then your SSH Key 2 should be the root user key of the jump host.
Finally, run a hosts_test
Test run
Simply run ansible all -i hosts_test -m ping and ansible all -i hosts_test -a "/usr/bin/uptime" to test if the setup is working or not.
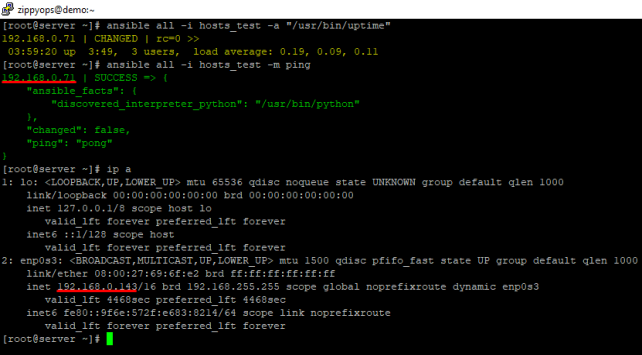
The test run is successful for the target machine.
Recent Comments
No comments
Leave a Comment
We will be happy to hear what you think about this post