Product Security (DevSecOps Practices)
In this article, we will discuss product security, why it is needed, DevSecOps best practices, and its benefits.
What Is Product Security?
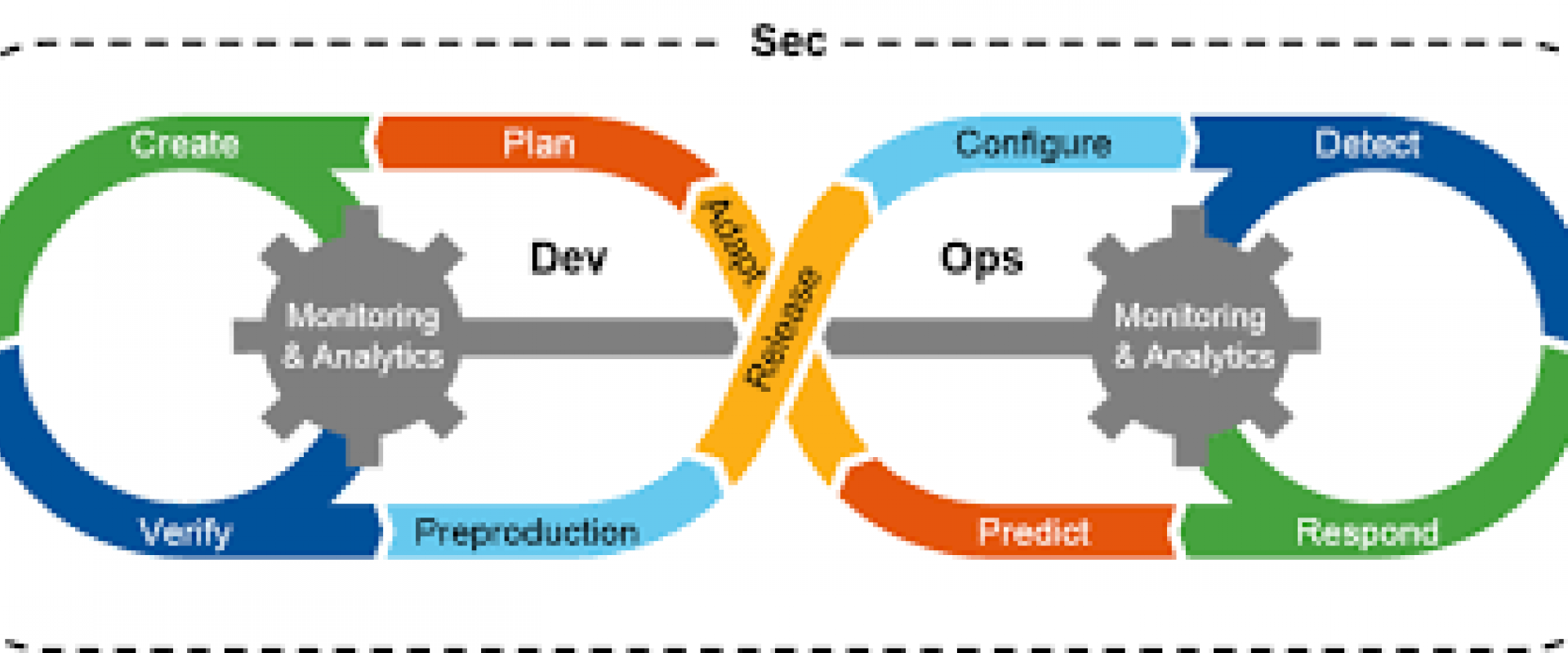
Product Security is a process within the Cybersecurity function which aims to deliver a secure product, which includes the organization's Web applications, Web services, Mobile applications, or any hardware manufactured. This focuses on considering security at every stage, starting from design, development, and implementation, i.e., the secure SDLC process.
Product Security involves multiple activities, including threat modeling, Security testing (Static application security testing (SAST)), Dynamic application security testing (DAST), Penetration Testing, Secure coding practices, Incident response, and Continuous monitoring. The primary goal of product security is to protect the CIA (Confidentiality, Integrity, and Availability).
Standards used: OWASP Top 10, SAN 25, Penetration testing standards.
Why Do We Need Product Security?
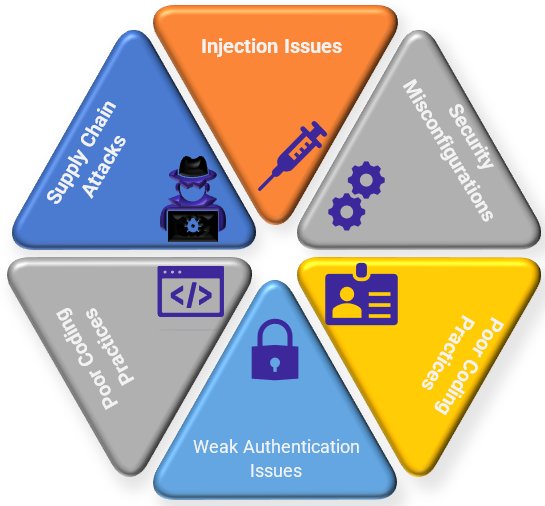
We need product security to defend the products from security threats/risks posed by the threat actors. Some of the common routes observed for product security are:
Injection Issues: This is a Security vulnerability where it allows a threat actor to inject malicious code/untrusted data when the application fails to validate or sanitize the input.
Security Misconfigurations: Opening up the unused or unsecured ports, which results in compromising the application or a product, i.e., Unauthorized access to an application and its data.
Security Updates (OS and third-party application library Vulnerabilities): When the systems, applications, or products are not patched or updated with the security vulnerabilities
Weak Authentication mechanism: Applications or systems still use the easily guessable username and passwords/using the default credentials.
Poor Coding Practices: Following poor/insecure coding practices
Supply Chain Attacks: Attack which compromises a product or its associated components, this works by carrying the malicious software or a component via a supplier or vendor.
To overcome these issues vectors and to deliver a secure product, we need to consider every stage of your SDLC (Software Development Lifecycle) process.
Product Security Threats
Below listed are some of the common product security vulnerabilities reported:
- Cross-Site Scripting (XSS): Malicious scripts are injected into trusted websites.
- SQL Injection: Used to exploit a vulnerability in a web application that uses a database. It is allowing attackers to inject malicious code into the database.
- Remote Code Execution: Attackers remotely execute commands to place malware or other malicious code on your computer or network.
- Denial of Service: An attack that attempts to make an application or any infrastructure resources to be unavailable.
- Buffer Overflow: A vulnerability that occurs when a program tries to write more data to a buffer than it can hold.
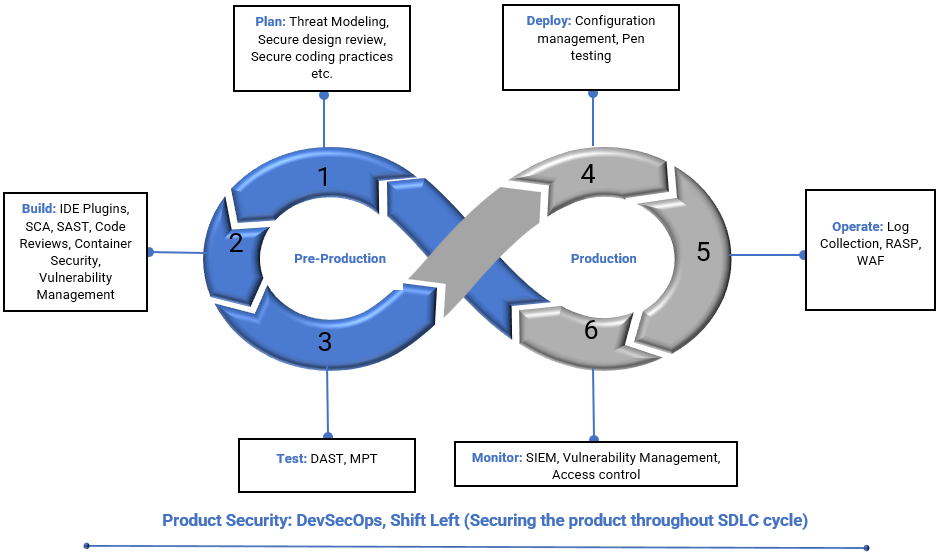
Best Practices to Be Considered for Product Security
Below listed are some of the best practices to be followed for a successful product security program.
- Ensure proper threat modeling, Security Architecture, and design reviews are performed.
- Training or empowering the developers on secure coding practices.
1. Create a security culture within your organization by offering security training and awareness programs and emphasizing the importance of security throughout the entire development and deployment process. By doing so, you can help ensure that everyone involved in the product development lifecycle is aware of the potential security risks and is equipped to address them. This can help mitigate vulnerabilities and reduce the risk of security incidents.
- Following the established coding standards and frameworks, such as OWASP or SANS Top 25, ensure that your code is secure.
- Integrating Spell checkers to the Developer IDEs (e.g., Secure Code warrior) identifies the vulnerabilities within the code as the developer types their code.
- Secrets management allows organizations to remove these hard-coded secrets from DevOps tools within the CI/CD pipeline.
- Ensure the developed code is fully tested, and adequate security testing is performed (E.g., SAST, DAST, and Manual Penetration testing).
- Proper access controls and authorization are to be set up.
- Data Encryption: Ensure data is encrypted both in transit and at rest.
- Monitoring and logging: To continuously monitor, which helps detect or respond to security incidents.
- Setting up strong Vulnerability management and configuration management programs.
- Follow the principle of least privilege to prevent unauthorized access.
Benefits of Product Security
- Protects the applications/Products from unauthorized access and sensitive data exposure.
- Reduces the cost of security incidents.
- Great saving of remediation timelines, as we implement the security at every stage of this process.
- Maintains customer trust and loyalty.
- Great brand reputation.
- Protects from financial losses.
Key Components of Product Security (Testing Standards)
The OWASP Top 10 serves as a guide for developers and organizations to prioritize and address security risks in their products.
Below listed is the OWASP TOP 10 standards list:
1. Injection Flaws
Attackers can exploit these vulnerabilities by injecting malicious code into an application's input fields. Once injected, this code can be executed by the application's backend, potentially allowing the attacker to take control of the system or steal sensitive information.
2. Broken Authentication and Session Management
The application fails to adequately manage user authentication and session tokens; it can create vulnerabilities that enable unauthorized access to sensitive information or functionality. These vulnerabilities can pose a significant threat to the security and integrity of an application and its users' data.
3. Improper Input Validation
The application fails to perform sufficient input data validation; it can create vulnerabilities that attackers can exploit by submitting malicious input. This leads to various injection attacks, cross-site scripting attacks, and other types of data manipulation. These vulnerabilities can be especially dangerous because they allow attackers to control the application or gain access to sensitive data.
4. Security Misconfiguration
Vulnerabilities can arise when an application is not configured correctly; attackers can exploit the vulnerabilities and gain unauthorized access to sensitive data or systems. This may lead to complete control of the system.
5. Insecure Communication
This occurs when an application communicates through a secure channel (Plain text); this enables the threat actor to intercept and extract the data.
6. Poor Access Control
The application fails or does not properly restrict access to sensitive functionality or data, allowing unauthorized users to access or modify information they should not have access to.
7. Insecure Design
Vulnerabilities occur when an application is designed with security flaws.
8. Insufficient Logging and Monitoring
Vulnerabilities occur when the application does not properly log security events or monitor for suspicious activity, which makes it a difficult response to threat attacks.
9. Software and Data Integrity Failures
When an application doesn't check that it's software and data are correct and haven't been changed by attackers, it can create vulnerabilities that allow attackers to manipulate or damage the system. This can lead to data breaches or other types of security incidents that could cause significant harm.
10. Server-Side Request Forgery (SSRF)
Vulnerabilities can arise when an application handles URLs supplied by users. Attackers can take advantage of these vulnerabilities by sending malicious requests to internal resources, which could result in data theft or unauthorized access. These types of attacks can be particularly dangerous because they may allow attackers to gain access to sensitive data or systems that are not intended to be accessible from the outside.
Conclusion
In conclusion, implementing product security is key for any organization to secure applications or products from external threat attacks. Allows Organizations to measure, detect, identify, prevent, and mitigate security risks. By adopting product security, culture organizations can protect their assets and clients.
We Provide consulting, implementation, and management services on DevOps, DevSecOps, Cloud, Automated Ops, Microservices, Infrastructure, and Security
Services offered by us: https://www.zippyops.com/services
Our Products: https://www.zippyops.com/products
Our Solutions: https://www.zippyops.com/solutions
For Demo, videos check out YouTube Playlist: https://www.youtube.com/watch?v=4FYvPooN_Tg&list=PLCJ3JpanNyCfXlHahZhYgJH9-rV6ouPro
If this seems interesting, please email us at [email protected] for a call.
Relevant Blogs:
Untold Benefits of Application Modernization
RSA Algorithm: A Trusted Method for Encrypting and Securing Data
5 Ways to Secure a Virtual Machine in Cloud Computing
19 Most Common OpenSSL Commands for 2023
Recent Comments
No comments
Leave a Comment
We will be happy to hear what you think about this post