Public Key and Private Key Pairs: Know the Technical Difference
Read this comprehensive guide on Public and Private key Pair Cryptography and understand what and how they work in cryptography.
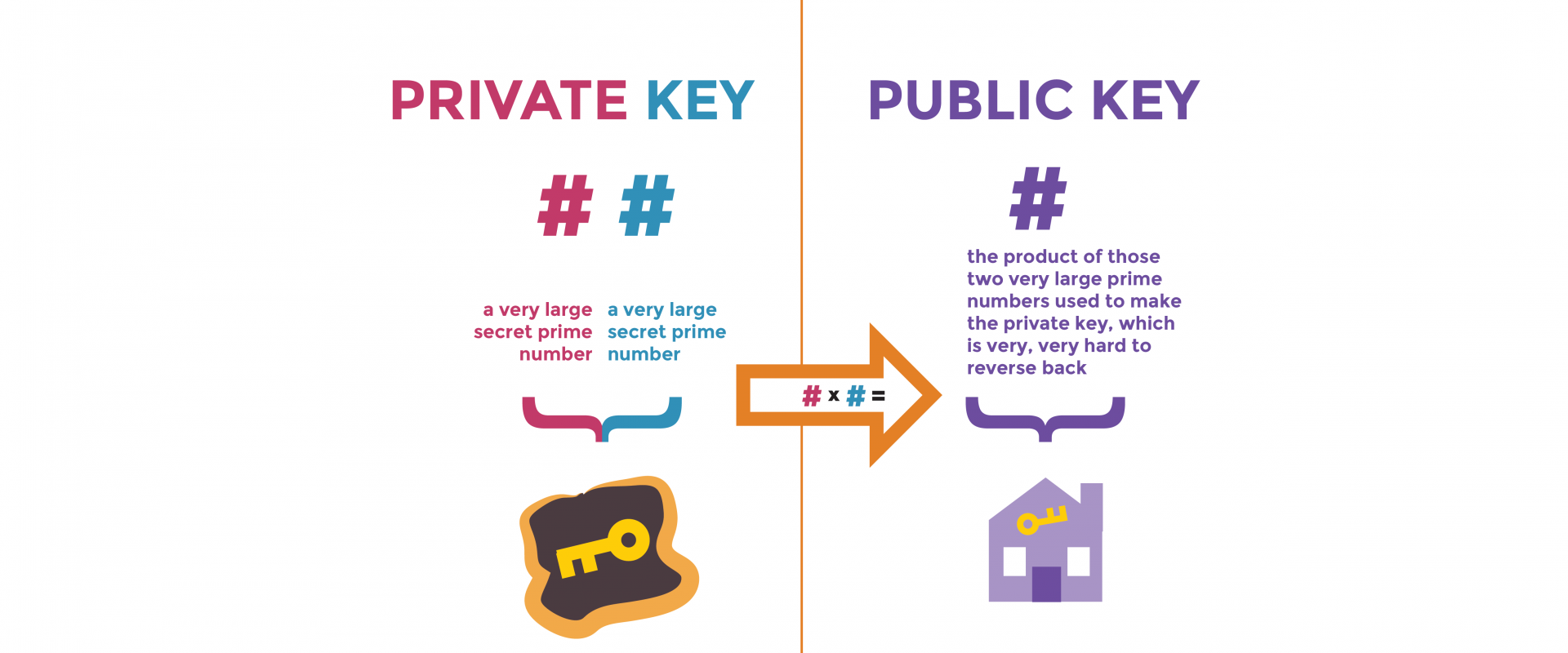
In public key cryptography, the combination of private and public keys is considered the primary component. Both the keys come in pairs. So a public or private key will only function with the associated public or private key. It means that one private key can only have one public key and vice versa.
Before we get into the part where we explain how the combination works, let us first discuss each of the keys individually. So let’s get started with the private key first.
What Is a Private Key?
A private key is a piece of information used to decrypt and encrypt data, forming an integral part of a cryptographic system used to secure communication, protect data, and verify the authenticity of messages.
By a thumb rule, public keys are shared in the open, but private keys should be confidential. When someone wants to send encrypted data to the owner of the private, a public key is used for encrypting the message. So just the owner of the private key has the ability to decipher the message because they possess the private key.
Anyone with a private key can decrypt sensitive information transmitted over an encrypted connection. Therefore, private keys are often stored on secure servers or devices and may be protected by additional layers of security, such as passwords or biometric authentication.
Understood what private key encryption is? Let us now discuss what a public key is.
What Is a Public Key?
A public key is a piece of information that is used to encrypt data and verify the authenticity of a message or document.
In a cryptographic system that uses a public key, a parallel private key is used to decrypt messages or data encrypted using the public key. The public key can be shared freely, while the private key must be kept secret. By using the public key to encrypt the message, a person can send encrypted data to the owner of the private key. This way, just the private key owner can decrypt the message because they are the only ones with access to the private key.
Now that we know what private and public keys mean individually let us understand what a pair of public and private keys are.
What Are Pairs of Public and Private Keys?
As discussed, a public-private key pair is a set of two unique keys used for symmetric and asymmetric encryption and decryption of data. For example, in a cryptographic system that uses a pair of public and private keys, there is a private key and a parallel public key. The private key stays confidential and is used for decrypting messages or encrypted data using the parallel public key. On the other hand, the public key can be shared freely and is used to encrypt messages or data intended for the private key’s owner.
It is important to ensure that the correct public key is used to encrypt a message or document, as only the parallel private key will be able to decrypt the message. Similarly, it is important to keep the private key secure and protect it from unauthorized access, as anyone with access to it would be able to decrypt sensitive information transmitted over an encrypted connection.
So how do they work to establish security? Let us discuss that.
How Do a Pair of Public and Private Keys Work?
Here’s an example of how a pair of public and private keys might be used when it comes to encrypted messages:
- The sender generates a pair of public and private keys using different forms of encryption algorithms such as RSA, DSA, and ECC (Elliptic Curve Cryptography). The private key is kept secret, while the public key is shared with the intended recipient.
- For the sender to send an encrypted message, they will employ the recipient’s public key for the encryption of the message.
- The recipient is sent the encrypted message.
- With the help of a private key, the recipient can decrypt the message, as the person with the private key is the one who can decrypt the message because it is the only key that can reverse the encryption process performed using the public key.
This is how the combination of a public key and private key encryption works. Now that we know they work, let us see how this combination benefits the security of data on the internet.
What Are the Benefits of Public-Private Key Pair?
A pair of public and private keys are used in public key cryptography, which is a method of secure communication that allows people to exchange messages without needing to agree on a shared secret key in advance. The benefits of pair of public and private keys include the following:
The pair of public and private keys helps in protecting communication by allowing messages to be encrypted with a public key and decrypted only with the parallel private key. This means that only the owner of the private key can decrypt the message, providing a high level of security.
For example, Mike has some confidential information that he wants to send to Dustin. However, he wants to ensure that only Dustin receives it. For that, he will encrypt the information with the public key Dustin, and since only Dustin can access the parallel private key, he can read and decrypt the encrypted information and access the information.
In this case, even if someone other than Dustin gets access to the encrypted information, it will still remain unreadable as they would not have access to the private key that only Dustin has.
A pair of public and private keys can help to establish non-repudiation, which is the ability to prove that a particular message was sent by a specific sender and cannot be denied by that sender.
To understand how a pair of public and private keys can be used for non-repudiation, we will consider the same example as above.
Mike wants to send confidential information to Dustin. But in this case, Dustin wants to make sure either Mike or Dustin himself cannot deny the information. So Dustin can use Mike’s public key to encrypt the information and then send the encrypted message to Mike. So, only Mike, who has the parallel private key, can decrypt the message and read it.
Because the message was encrypted with Mike’s public key, it can only be decrypted with his private key. This means that the message could only have been sent by someone who had access to Mike’s public key. So in case, Mike refuses to receive any information, Dustin can prove that the information was sent by showing the encrypted message and Mike’s public key.
In this way, a pair of public and private keys can be used to establish non-repudiation by providing evidence that a message was sent by a specific sender and cannot be denied by that sender. This can be useful in cases where it is important to establish the authenticity of a message.
A pair of public and private keys can make secure communication easier to use because they allow users to exchange messages without needing to agree on a shared secret key in advance. This can be particularly useful in cases where it is difficult to securely exchange a secret key, such as when the users are located in different countries or when the users do not have a secure way to communicate.
Let’s take the same example of Dustin and Mike. The scenario remains the same. But in this case, Mike and Dustin need not exchange a secret key in advance or look for a secure way of communicating the key. Rather, they can use the public-private key for securely exchanging messages. This process can reduce the risk of key management problems and make it easier for users to use secure communication.
A pair of public and private keys can help make secure communication scalable because they allow many users to exchange messages without the need to agree on a shared secret key for each pair of users.
In traditional symmetric key cryptography, a shared secret key was used for encrypting and decrypting messages. This means that a separate secret must be exchanged and agreed upon by each pair of users who want to communicate securely with each other. However, this proved to be a time-taking and impractical process in cases where a large number of people were involved in communicating securely.
In contrast, public key cryptography facilitates users to exchange messages using a public-private key pair. The public key is used to encrypt the message, and the private key is used to decrypt it. This means that each user only needs to share their public key with others instead of agreeing on a separate secret key for each pair of users.
For example, suppose there is a group of 1000 users who want to communicate securely. With traditional symmetric key cryptography, this would require the exchange and agreement of 99000 secret keys (one for each pair of users). However, with public key cryptography, each user would only need to share their public key with the other 990 users, making it much more scalable.
This can make it more practical and efficient to use secure communication in large systems.
Where Is Public-Private Key Pair Used?
A pair of public and private keys are used in many cryptographic protocols to securely transmit data between two parties. In these protocols, one party (typically called the sender) has a private key to encrypt data, and the other party (typically called the receiver) has a parallel public key to decrypt the data.
A pair of public and private keys are used in many other applications, including;
Secure Sockets Layer (SSL) protocol is a common application of a pair of private, public keys for securing communications over the web. These protocols use a pair of public and private keys for launching a secure connection between the central server and the client-server.
A digital signature is responsible for verifying the authenticity and integrity of software or digital file. It works by using a private key to develop a distinct signature for the file, which can then be verified using the parallel public key. The basic idea is that a private key is used to develop a unique signature for a piece of information, and the parallel public key is used for the purpose of validating the information’s authenticity and integrity.
A pair of public and private keys can be used to securely send and receive emails in a process called email encryption. Email encryption works by using a private key to encrypt the content of an email message and a public key to decrypt it. In addition to encrypting the content of the data, the sender can also create a digital signature of the data by using their private key. Thus, the recipient can validate the information’s authenticity and integrity as well as the sender’s identity.
Authenticating SSH Connections
The Secure Shell (SSH) protocol is a secure network protocol used for launching secure connections between servers. With the help of public-key cryptography, SSH authenticates the remote computer and paves the way for remote computers to authenticate the user. In this process, the user generates a pair of public and private keys and then installs their public key on the remote computer. After this process, the user begins an SSH connection to the remote computer. Later, by using their public key, the remote computer validates the user.
There are many technical details involved in implementing public-key authentication for SSH in practice, but the basic idea is that the user’s private key is used to authenticate the user to the remote computer, and the remote computer uses the parallel public key to verify the authenticity of the user.
Ethereum and Other Blockchain Platforms
A pair of public and private keys are widely used in Ethereum and other blockchain platforms to securely sign transactions and provide proof of ownership of a blockchain account.
In these platforms, users generate a pair of public and private keys and install their public keys on the blockchain. Then, when the user wants to send a transaction on the blockchain, they use their private key to sign the transaction. The signed transaction is then broadcast to the network, where it is verified using the user’s public key. If the signature is valid, the transaction is processed by the network.
For signing the transaction and proving the ownership of their blockchain account, the user’s private key is used. The network uses the parallel public key to establish the authenticity and integrity of the transaction. A pair of public and private keys are used to securely sign transactions on these platforms.
These are some of the places where private-public keys are used.
Stay Encrypted, and Stay Safe!
A private and public key pair is a set of two keys you use to encrypt and decrypt confidential information on the web. Thus, they make for robust encryption and data security. Leveraging this pair of keys, you can enjoy seamless, enhanced security. We hope the blog gives you an idea about private and public keys and how it is instrumental in keeping the data safe and secure.
We Provide consulting, implementation, and management services on DevOps, DevSecOps, Cloud, Automated Ops, Microservices, Infrastructure, and Security
Services offered by us: https://www.zippyops.com/services
Our Products: https://www.zippyops.com/products
Our Solutions: https://www.zippyops.com/solutions
For Demo, videos check out YouTube Playlist: https://www.youtube.com/watch?v=4FYvPooN_Tg&list=PLCJ3JpanNyCfXlHahZhYgJH9-rV6ouPro
If this seems interesting, please email us at [email protected] for a call.
Relevant Blogs:
Getting Started With Kubernetes In 2 Days
Why Training Labs are mandatory for good training
Solving the Kubernetes Security Puzzle
19 Most Common OpenSSL Commands for 2023
Recent Comments
No comments
Leave a Comment
We will be happy to hear what you think about this post