XSS Attacks: Best Prevention
In this post, explore the best practices for Cross-site
scripting (XSS) prevention, types of attacks in modern web applications, and
address commonly asked questions.
What Is Cross-Site Scripting Prevention?
A Cross-site scripting attack involves the execution of malicious code on a victim’s browser. Typically, the challenges to prevent Cross-site scripting (XSS) vulnerabilities are complex, since attacks can be orchestrated at any point in a vulnerable web application. This article explores the best practices for Cross-site scripting prevention, types of attacks in modern web applications and addresses commonly asked questions.
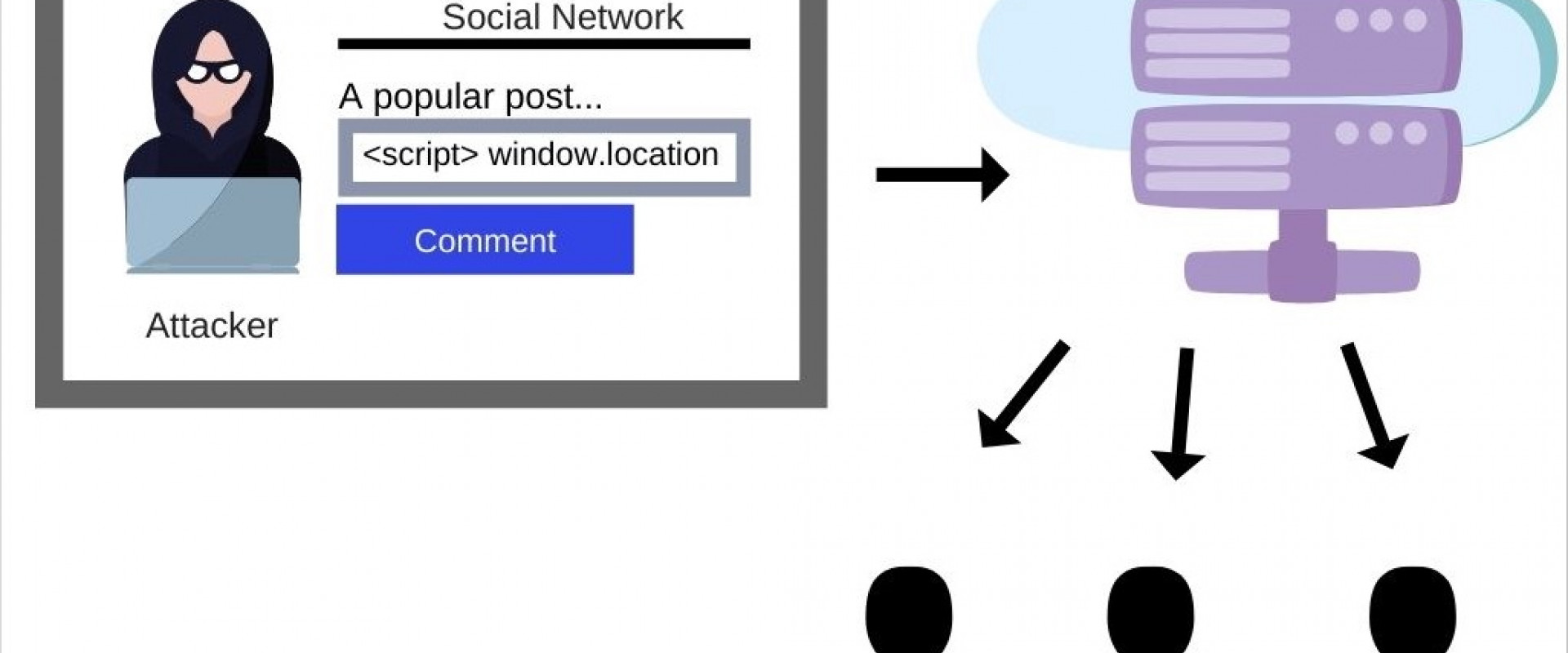
Before we look at those areas, here is a quick introduction to how an XSS attack is orchestrated.
In an XSS attack, the threat actor crafts a malicious script that is routed to the user, then executed by the application browser. This is usually perpetrated by the attacker using input fields to send crafted HTML/JavaScript code to a website, which gets interpreted by modern browsers of the victim. The web application includes the executed script as part of its response as if it is legitimate. As soon as this happens, the attacker has full access to all resources available for the current session, including cookies, local storage, form values, etc. In addition, the malicious user may also have complete control over the victim’s machine.
Benefits of Preventing XSS Vulnerabilities
If not detected and fixed on time, Cross-site scripting vulnerabilities can facilitate attacks detrimental to the organization. Through XSS attacks, threat actors can easily compromise how websites present content to users. Additionally, attackers can leverage XSS vulnerabilities to seize accounts, exploit user credentials, identity theft, impersonate users and escalate privileges. Other malicious actions they can undertake include uploading malware, phishing attacks, exposure of sensitive data, and orchestration of full-blown attacks.
How To Prevent XSS Attacks
Since its discovery in the late 1990s, XSS vulnerability has been considered a common attack vector widely exploited by attackers. Since there are several identified gaps in the sanitization of user input, security professionals often focus on fixing cross-site scripting vulnerabilities based on two factors:
1. Type of XSS attack carried out,
and,
2. Programming language used to develop the application.
While considering the factors, security professionals
categorize XSS attacks as:
Reflected attack
Stored attack
DOM-based attack
Reflected XSS Attacks
The simplest type of XSS attack is where the application immediately processes and returns unsanitized user input in a search result, error message, or other HTTP responses. The application logic returns an unsafe input as part of the response without rendering it safely or storing data generated by users. In most reflected XSS attacks, the data provided by users never even leaves the browser.
Stored XSS Attacks
This is a persistent form of XSS that relies on the application persisting user input on the target server. Unsuspecting users then retrieve this data from the application without any sanitization or validation. Modern applications that use HTML5 allow attackers to store the malicious payload permanently on the browser, typically using HTML databases.
DOM Based XSS
The Document Object model is a platform-independent interface that defines a logical structure for accessing and manipulating documents in HTML and XML. Hackers orchestrate DOM-based XSS attacks by modifying the DOM environment on the browser so that client-side code is executed in an unsafe manner.
DOM-based vulnerabilities are advanced and challenging to fix since malicious client-side scripts do not go to the server. This makes it difficult for automatic vulnerability scanners and a Web Application Firewall to detect them since they don’t leave traces on the server logs.
Strategies for preventing XSS attacks also depend on the platform/programming language used. In the sections to follow, we will explore how to prevent XSS attacks on the following application types:
Prevent XSS in PHP
Prevent XSS in Javascript
Prevent XSS in JQuery
Preventing XSS in PHP
If a PHP application accepts HTML or JavaScript input, the web client executes remote scripts while rendering content. For instance, if the client-side includes a JavaScript file:
// http://example.com/darwin.js("I'm executing");
ZippyOPS Provide consulting, implementation, and management services on DevOps, DevSecOps, Cloud, Automated Ops, Microservices, Infrastructure, and Security
Services offered by us: https://www.zippyops.com/services
Our Products: https://www.zippyops.com/products
Our Solutions: https://www.zippyops.com/solutions
For Demo, videos check out YouTube Playlist:
https://www.youtube.com/watch?v=4FYvPooN_Tg&list=PLCJ3JpanNyCfXlHahZhYgJH9-rV6ouPro
If this seems interesting, please email us at [email protected] for a call.
Relevant Blogs:
Terraform execution in pipeline
Recent Comments
No comments
Leave a Comment
We will be happy to hear what you think about this post