App Developers Are the First Line of Defense Against Cyberattacks
Cyberattacks have become more common than ever, so app developers must develop tools to help fight them. You can find more information about this here.
A growing number of developers are creating new apps dedicated to improving cybersecurity. Their work is going to be even more important than ever as cyberattacks become a greater threat.
In order to thwart would-be cybercriminals, app developers need to understand how these crimes are conducted. You can find more information about this below.
App Developers Must Appreciate the Threats Cybercriminals Play to Counteract Them
The field of cybersecurity is dynamic.
Systems that companies use are ever-changing and upgraded constantly. Essentially, they have to be prepared for new hacking methods before threat actors get a chance to exploit weaknesses in their security.
In 2020, some key problems for cybersecurity had been a lack of cybersecurity measures, misconfigurations in the cloud, Distributed Denial of Attacks, and the shift to remote work.
App developers can help mitigate these threats by properly understanding them. In 2021, businesses of all sizes will invest in cybersecurity more than ever before, but known security issues have remained. The top difficulties included things such as ransomware, phishing, software vulnerabilities, cryptocurrency attacks, and more.
Increased Attack Surface With Remote Teams
Business infrastructures have changed beyond recognition compared to their state back in 2020. The assets and devices that have to be protected against cyber breaches now additionally include remote worker’s devices and intricate cloud environments.
The attack surface is also larger because of the increased demand for remote work. As many companies don’t intend to return to offices and stay entirely remote or allow hybrid solutions, this issue is one that remains relevant.
The pandemic sped up the process of digitization of a company's assets. They had to adjust their systems for remote work and shift much of their activity online but continue advancing the newly created infrastructures.
After two years, businesses have fewer gaps in security, but they are still relying on remotely accessible networks and adding new features to improve their infrastructures.
Deploying complex multi-cloud environments and with every new tool and home device that connects to the system, there is a greater chance that a business can open up a vulnerability that will be exploited by criminals.
Social Engineering Attacks
As Bruce Schneier said: “Amateurs hack systems, professionals hack people.”
This is still true in 2022.
Hackers are more likely to be successful if they target unsuspecting employees that are just doing their job but don’t know a lot about cybersecurity trends and issues facing them.
To protect their devices and possible vulnerabilities in the system, most companies have even more solutions that they could use. Therefore, it’s more difficult to breach systems by targeting them directly.
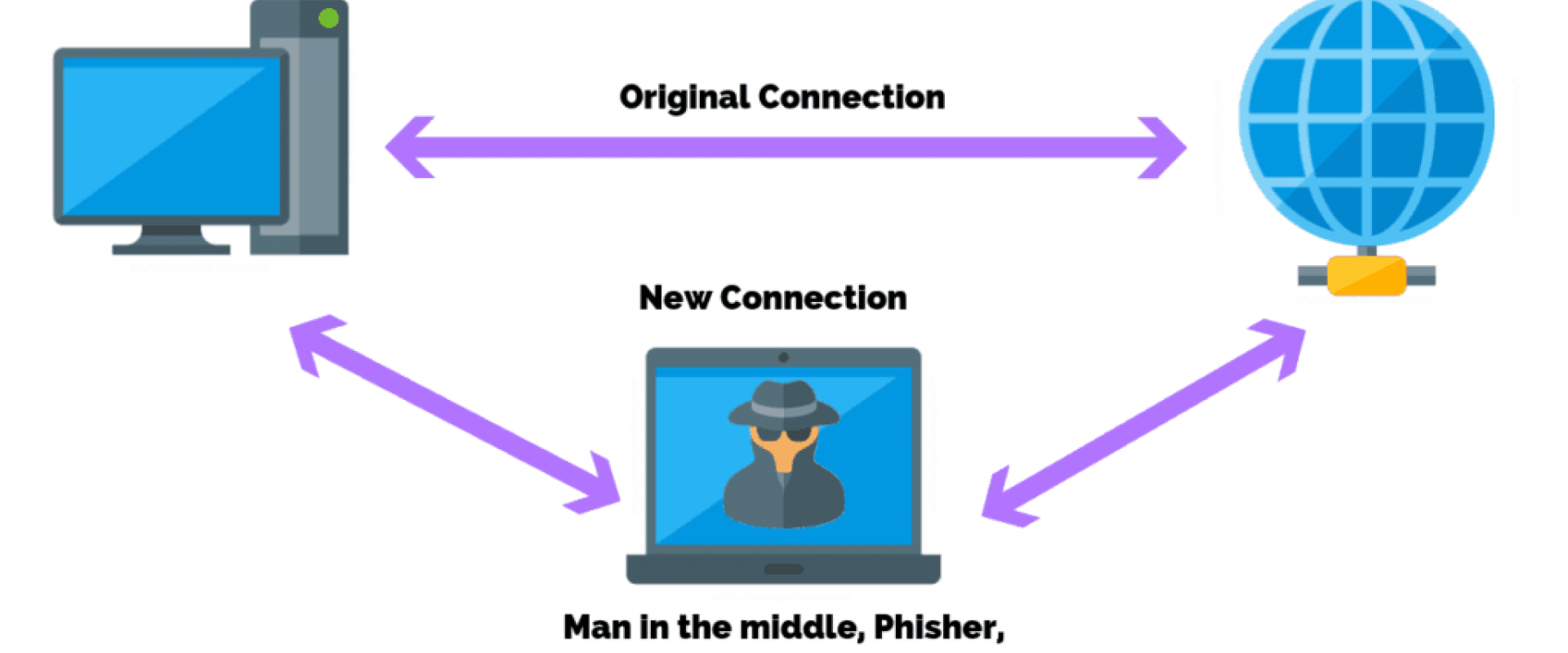
Exploiting weak passwords, leaked intelligence online, and impersonating authorities to gain the trust of employees are more likely to result in unauthorized access and a breach of the database of the targeted company.
Social engineering attacks that rely on human mistakes, such as employees clicking on a malicious link in a phishing email, remain among the top concerns for security experts.
The main goal of the phishing attack stays the same, as well as its monetary gain. Most phishing attacks are conducted via email, and they typically target financial institutions.
This difficulty comes hand in hand with inadequate employee training. By far, basic cybersecurity training has been narrowed down to awareness and has focused on the more tech-savvy employees, particularly when it’s by choice. Employees that aren’t well acquainted with technology tend to shy away, and those that do have an interest are usually already well-versed.
There is also a lack in the overall company culture that makes it easy to report possible incidents.
Understaffed Cybersecurity Teams
A workforce shortage and the inability to hire suitable employees in the field and unfilled positions have presented an issue in the IT industry as well. As many as 68% of companies have reported that they haven’t been able to find suitable candidates to hire in 2022. A favorable statistic for cybercriminals.
Retaining talented cybersecurity experts has been one of the major challenges in 2021, and that trend continues in 2022 for many companies.
The aftermath of this issue is that teams that do work in cybersecurity are understaffed and suffer from poor work conditions.
Long hours with night shifts, heavy workloads, and poor management have led many talented IT professionals experiencing burnout and leave the industry.
If they lack support from the management and are insufficiently compensated for their efforts, employees are also likely to accept opportunities in other companies.
Poor Data Management
Ensuring that the information is safe and keeping up with the complex policies that govern the privacy of the data has been a major issue for businesses, especially those with global users.
Adhering to different laws that govern the privacy policies of users that use applications from different parts of the world has been difficult.
Poor data management has plagued 2022. Companies might not have a clear overview of where sensitive information is circulating in the system or safe backups in the case of a cyberattack.
With common threats such as ransomware that encrypts data until the target pays the ransom, it means that during the time that the system is under attack, teams can’t work. The solution is to have a backup that can be accessed if that happens.
Unmanaged data paired with the breach can result in the disrupted workflow of your employees that can't access the encrypted systems remotely and major financial losses.
Cybersecurity Is Continually Evolving
Some of the other obstacles that we haven’t mentioned include misconfigurations and poor cybersecurity hygiene.
Also, it’s safe to say that most of the mentioned issues are not new either.
Social engineering attacks such as phishing are on the top of the list of major concerns because they target the weakest spot in security, which is people. They rely on human error and get more sophisticated with every year.
What Could the Future Hold for This Industry?
Complex attack surfaces, understaffed teams that guard and image security, and new hacking techniques are some of the challenges that require drastic changes in the way we approach cybersecurity today.
This could include increased reliance on AI or altering the way cybersecurity experts and IT teams are managed within companies.
We Provide consulting, implementation, and management services on DevOps, DevSecOps, Cloud, Automated Ops, Microservices, Infrastructure, and Security
Services offered by us: https://www.zippyops.com/services
Our Products: https://www.zippyops.com/products
Our Solutions: https://www.zippyops.com/solutions
For Demo, videos check out YouTube Playlist: https://www.youtube.com/watch?v=4FYvPooN_Tg&list=PLCJ3JpanNyCfXlHahZhYgJH9-rV6ouPro
If this seems interesting, please email us at [email protected] for a call.
Relevant blogs:
Security and Compliance Considerations for the Public Cloud
Everything You Need to Know About SaaS Security Certification
Securing Kubernetes Secrets With HashiCorp Vault
Introduction to IAM in Google Cloud Platform (GCP)
Recent Comments
No comments
Leave a Comment
We will be happy to hear what you think about this post