Enhance IaC Security With Mend Scans

Learn to incorporate Mend into your IaC workflows, improve infrastructure security posture, reduce the risk of misconfigurations, and ensure compliance.
Whether on the cloud or setting up your AIOps pipeline, automation has simplified the setup, configuration, and installation of your deployment. Infrastructure as Code(IaC) especially plays an important role in setting up the infrastructure. With IaC tools, you will be able to describe the configuration and state of your infrastructure that are desirable. The popular tools for IaC include Terraform, Pulumi, AWS CloudFormation, and Ansible; each of them has different possibilities for automating the deployment and management of infrastructure both in the cloud and on-premises.
With the growing complexity of applications and heightened focus on security in software development, the tools SonarQube and Mend are more predisposed. SonarQube is a code analysis tool aimed at helping developers have high-quality code by spotting bugs and vulnerabilities across several programming languages. SonarQube is very well integrated into pipelines of Continuous Integration/Continuous Deployment, producing continuous feedback while forcing enforcement of coding standards.
Mend deals with software composition analysis (SCA) helping organizations manage and secure their open-source OS components. Mend, formerly WhiteSource, is a very well-integrated security solution with IaC tools for improving the security posture of infrastructure deployments. Mend automates vulnerability scanning and management for IaC code, allowing their customers to manage incubated security issues very early in the development cycle.
Terraform for Infrastructure as Code
Terraform is a HashiCorp-developed tool that enables developers and operations teams to define, provision, and manage infrastructure using a declarative language known as HashiCorp Configuration Language, HCL. HCL2 is the current version. Terraform is a provider-agnostic tool that provides the ability to manage resources across several cloud platforms and services by use of a single tool.
Some of Terraform's standout features include:
1. Declarative syntax: This is a way of telling the user what they want, and Terraform basically figures out how to create it.
2. Plan and apply workflow: Terraform's plan command shows what changes will be made before actually applying them. This reduces the risk of unintended modifications.
3. State management: Terraform keeps track of your current state. This will turn on incremental changes and detect drift.
4. Modularity: Reusable modules allow teams to standardize and share infrastructure elements across projects.
IaC Tools in the Ecosystem
Alongside Terraform, a number of other tools offer different capabilities based on what users need and where they are running out of the IaC tool.
1. AWS CloudFormation: Specifically designed for AWS, it provides deep integration with AWS services but lacks multi-cloud support.
2. Azure Resource Manager (ARM) templates: Similar to CloudFormation, but for Azure resources
3. Google Cloud Deployment Manager: Google Cloud's native IaC solution
4. Pulumi: Allows developers to use familiar programming languages like Python, TypeScript, and Go to define infrastructure
5. Ansible: While primarily a configuration management tool, Ansible can also be used for infrastructure provisioning.
6. Chef and Puppet: Configuration management tools that can be extended for infrastructure provisioning
Enhancing Security With Mend
With the growth of IaC adoption, the demand for better security management also grows. This is where Mend comes in to provide a robust scanning and securing solution for IaC code. Mend will enable smooth incorporation into the development process as well as continuous security scanning of Terraform and other IaC tools. The following are some ways through which Mend boosts security measures without compromising on productivity:
- Automated scanning: Mend can scan your IaC code automatically in search of vulnerabilities, misconfigurations, and compliance issues.
- Early detection: If integrated with CI/CD pipelines, Mend will spot security vulnerabilities at an early stage during the development phase thus reducing cost and effort for fixing them later on.
- Custom policies: Teams can develop custom security policies to meet their specific needs and compliance requirements.
- Remediation guidance: Upon detection of a problem, Mend provides clear instructions on what steps should be taken to rectify it helping developers address security concerns promptly.
- Compliance mapping: Issues identified are mapped by mend as per the particular requirements of different standards or regulations so that organizations can maintain compliance.
- Continuous monitoring: Even after deployment, Mend continues to monitor your infrastructure for new vulnerabilities or drift from secure configurations.
- Integration with DevOps tools: Mend integrates with famous version control systems, CI/CD platforms, and ticketing systems, making it part of existing workflows.
This proactive approach to security allows teams to move fast and innovate while significantly minimizing the risk of security breaches, misconfigurations, and compliance violations when they adopt Mend in their IaC practices.
Along with Terraform, Mend supports the following IaC environments and their configuration files:
- Bicep
- CloudFormation
- Kubernetes
- ARM Templates
- Serverless
- Helm
Integrate Mend With GitHub
Mend provides several integration options and tools that GitHub users can use to further drive security and vulnerability management in their repositories.
Overview of Mend's Presence on GitHub
Mend for GitHub.com App
This GitHub App has both SCA and SAST capabilities. It can be installed directly from the GitHub Marketplace to allow easy integration with your repositories.
Mend Bolt
Mend Bolt performs repository scans looking for vulnerabilities in open-source components. It is available free of cost as an app on the GitHub Marketplace, supporting over 200 programming languages while supporting the following features:
· Scanning: This happens automatically after every "push." It detects vulnerabilities in open-source libraries and has a five-scan per-day limit per repository.
· Opening issues for vulnerable, open-source libraries
· Dependency tree management, along with the visualizing of dependency trees
· Checks for suggested fixes for vulnerabilities
· Integration with GitHub Checks stops pull requests with new vulnerabilities from getting merged.
Mend Toolkit
Mend maintains a GitHub Organization, "mend-toolkit", containing various repositories that host integration knowledge bases, examples of implementation, and tools. This includes:
· Mend implementation examples
· Mend SBOM Exporter CLI
· Parsing scripts for YAML files
· Import tools for SPDX or CSV SBOM into Mend
Mend Examples Repository
Under the mend-toolkit organization, there is a "mend-examples" repository with examples of several scanning and result-pulling techniques in Mend. This includes, among other things:
· SCM integration
· Integrating self-hosted repo setup
· Integration of CI/CD
· Examples of policy checks
· Mend prioritizes scans by language
· Terms Mend SAST and Mend SCA implementations
Set Up Mend for GitHub
In this article, you will learn how to set up Mend Bolt.
1. Install the Mend App
- Go to the GitHub Marketplace.
- Click "Install" and select the repositories you want to scan.
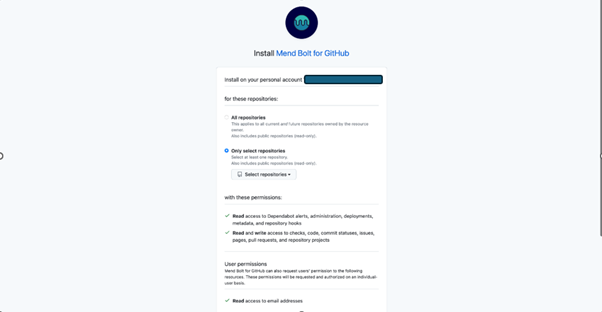
Install Mend Bolt for GitHub
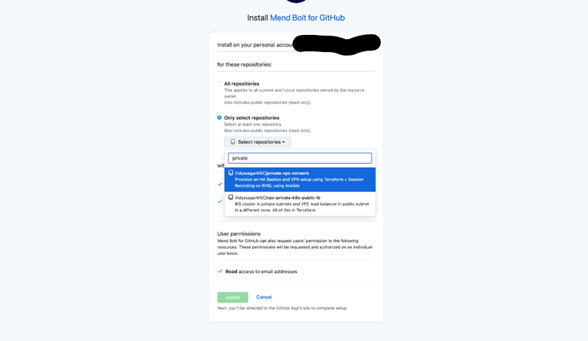
- After selecting the repositories, click on Install and complete authorization.
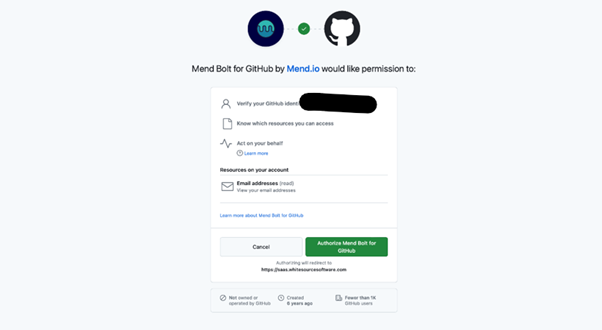
2. Complete the Mend Registration
- You'll be redirected to the Mend registration page.
- Complete the registration if you are a new Mend user and click on Submit.
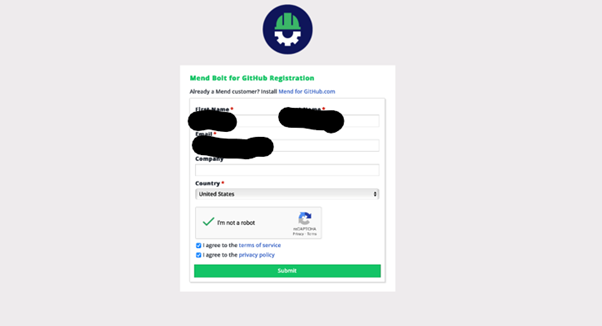
Mend Registration
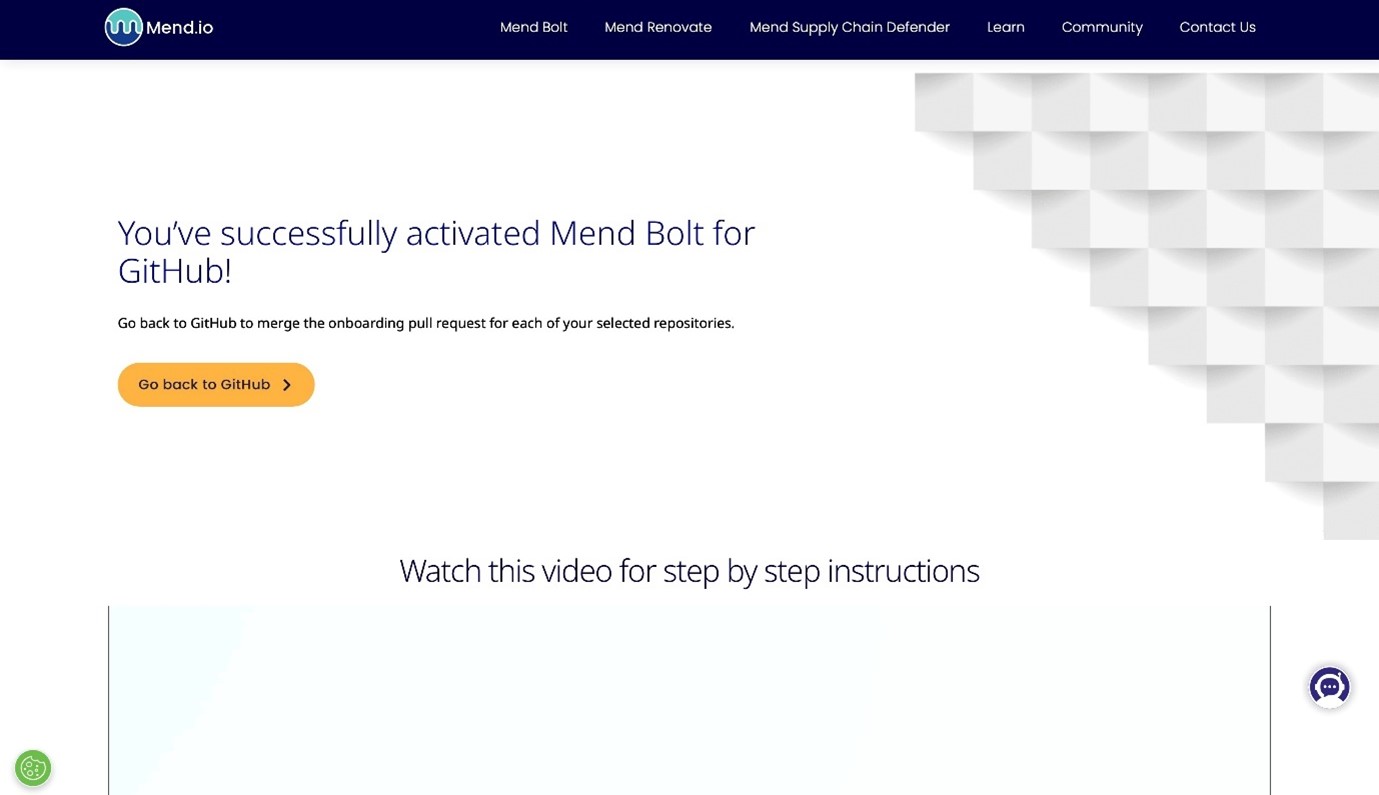
3. Merge the Configuration Pull Request
- Mend will automatically create a pull request(PR) in your repository.
- This PR adds a .whitesource configuration file:
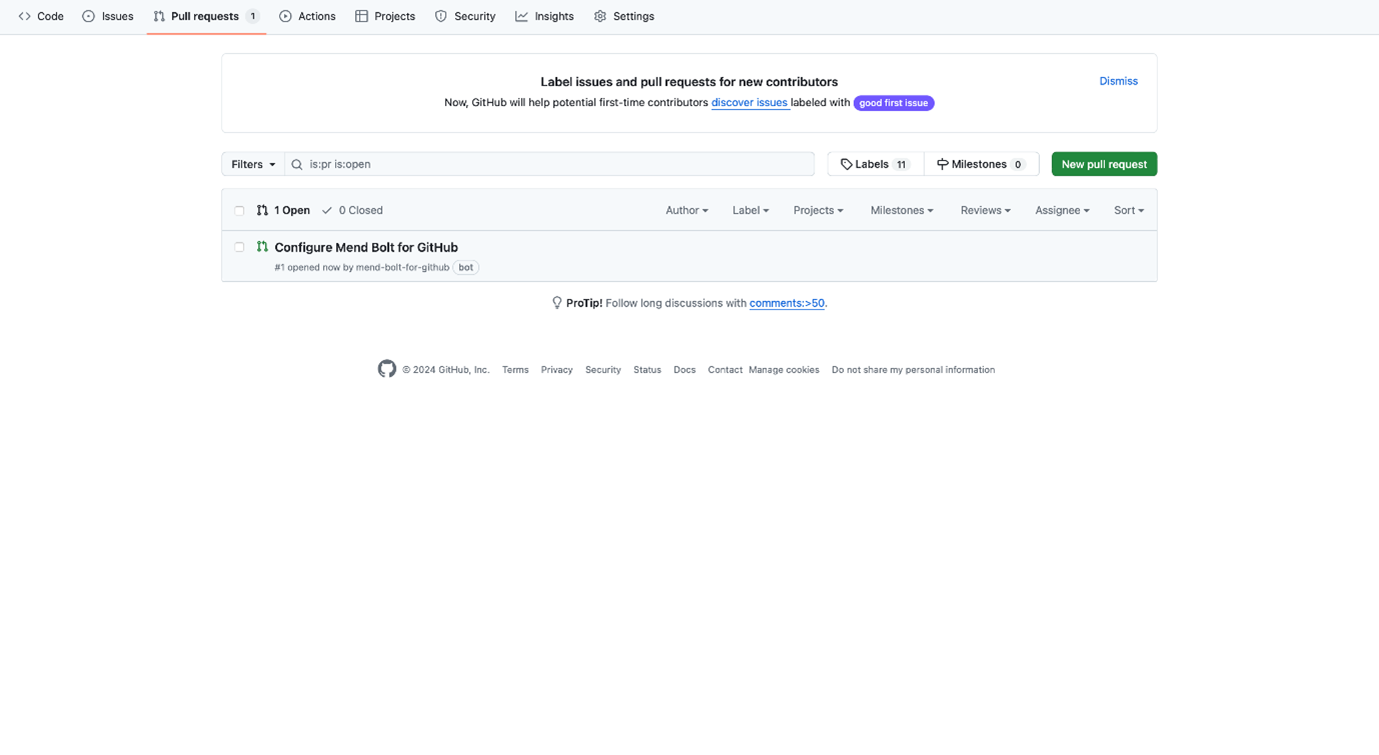
Mend PR
- Review the PR and merge it to initiate your first scan.
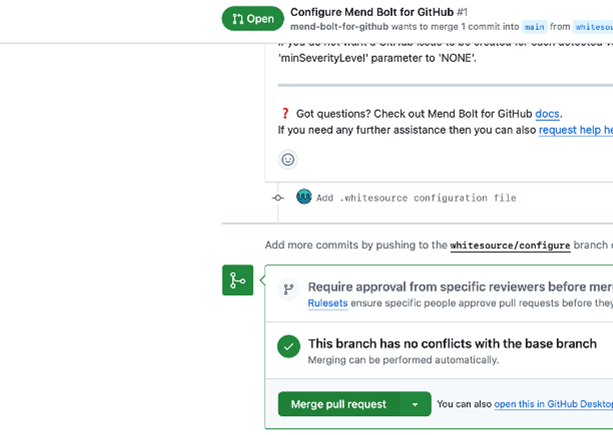
Review and merge the PR
4. Customize Scan Settings
- Open the .whitesource file in your repository.
- Modify settings as needed. The key setting to enable IaC scans is enableIaC: true.
{
"scanSettings": {
"enableIaC": true,
"baseBranches": ["main"]
},
"checkRunSettings": {
"vulnerableCheckRunConclusionLevel": "failure",
"displayMode": "diff",
"useMendCheckNames": true
},
"issueSettings": {
"minSeverityLevel": "LOW",
"issueType": "DEPENDENCY"
}
}
- Check the other configuration options (Configure Mend for GitHub.com for IaC).
- Note: Iac scans can only be performed on base branches.
{
"scanSettings": {
"enableIaC": true,
"baseBranches": ["main"]
},
"checkRunSettings": {
"useMendCheckNames": true,
"iacCheckRunConclusionLevel": "failure"
}
}
- Commit changes to update your scan configuration.
5. Monitor and Review Results
- Mend will now scan your repository on each push (limited to 5 scans/day per repo for Mend Bolt).
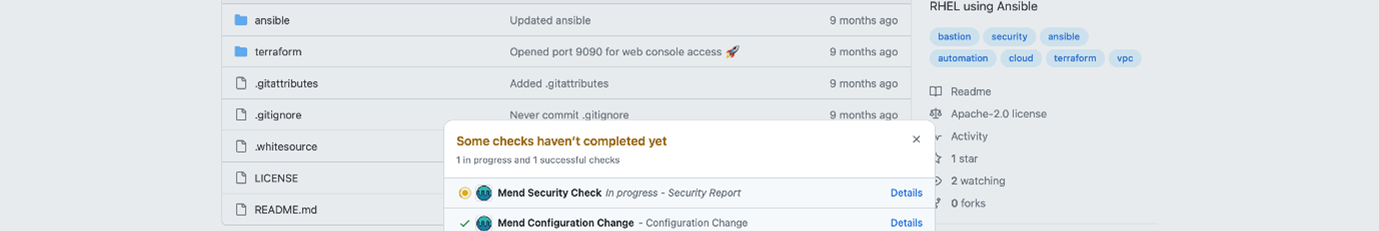
Mend scan report
- Check the "Issues" tab in your GitHub repository for vulnerability reports.
- Review the Mend dashboard for a comprehensive overview of your security status.
6. Remediate Issues
- For each vulnerability, Mend provides detailed information and suggested fixes.
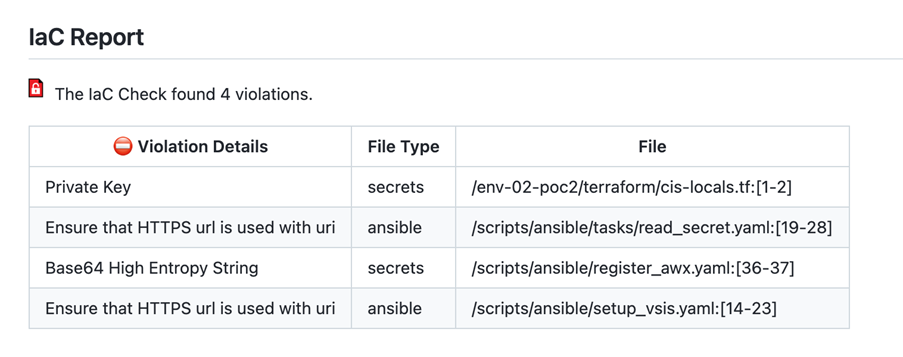
- Create pull requests to update vulnerable dependencies based on Mend's recommendations.
7. Continuous Monitoring
- Regularly review Mend scan results and GitHub issues.
- sKeep your .whitesource configuration file updated as your security needs evolve.
You have successfully integrated Mend with GitHub, enabling automated security scanning and vulnerability management for your repositories. Along with GitHub, Mend supports, Git Enterprise, GitLab, BitBucket, etc., You can find the supported platforms in the Mend documentation.
Conclusion
The power of IaC tools like Terraform, combined with robust security solutions such as Mend, sets any infrastructure management base on very strong ground. These technologies and best practices help keep organizations safe while ensuring adaptability and scalability for modern, fast-moving digital environments. Indeed, the importance of integrating security throughout the whole life cycle of our infrastructure cannot be overemphasized as we continue raising the bar on what is possible with infrastructure automation. There are additional best practices like version control, modularization, use of right access permissions, auditing your code for compliance, etc., providing added security to your IaC code.
We ZippyOPS Provide consulting, implementation, and management services on DevOps, DevSecOps, DataOps, MLOps, AIOps, Cloud, Automated Ops, Microservices, Infrastructure, and Security
Services offered by us: https://www.zippyops.com/services
Our Products: https://www.zippyops.com/products
Our Solutions: https://www.zippyops.com/solutions
For Demo, videos check out YouTube Playlist: https://www.youtube.com/watch?v=4FYvPooN_Tg&list=PLCJ3JpanNyCfXlHahZhYgJH9-rV6ouPro
If this seems interesting, please email us at [email protected] for a quick call.
Relevant Blogs:
Comparing IaC Tools for Azure: Terraform and Bicep
Terraform vs. Pulumi: Which Is Better for Your IaC Requirements?
Top 10 Infrastructure as Code (IaC) Tools
Recent Comments
No comments
Leave a Comment
We will be happy to hear what you think about this post