Linux Kernel Bugs and How to Combat Them

Read to learn more on how to keep your Linux security systems watertight. Follow these easy steps to avoid destructive bags.
The importance of secure IT systems cannot be overstated. Every day, new cyber threats emerge. As well as online networks, operating systems can also be vulnerable. Although Linux is more secure than other operating systems, no operating system is 100% safe from attacks.
In fact, there has been a rise in cyber attacks targeting Linux operating systems. High-value targets are often powered by Linux, making Linux security very important. For example, organizations who aim to stay HIPAA compliant in their communications need to make sure every piece of software they use—including their operating systems and even their digital workplace software—is as secure as possible.
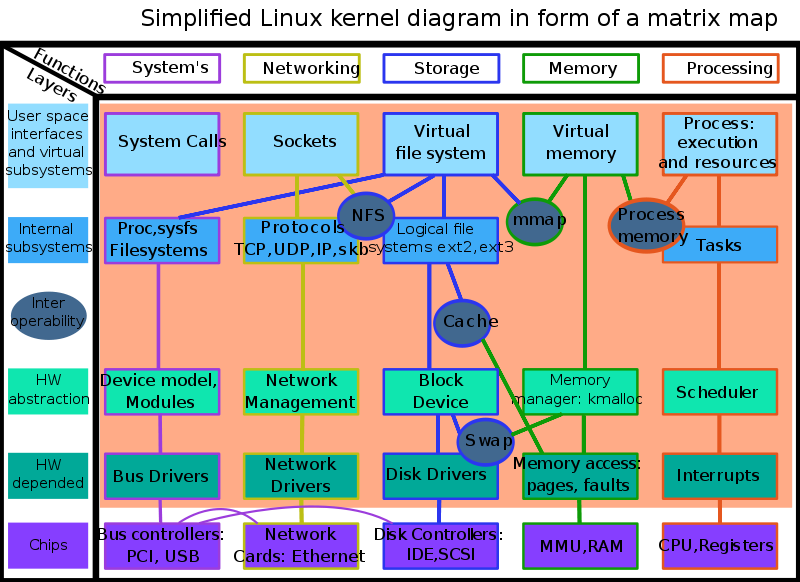
The security of the Linux kernel—or the core interface of the operating system, which powers all other processes—is crucial for overall system security. Most successful attacks on the Linux kernel can be attributed to poor configuration, administration, and common bugs in the system.
Many applications and systems are built with Linux (this mobile app flowchart is useful if you are thinking of creating an app), and security is paramount if many people are using them.
Thankfully, there are useful security tips to be found on sites and other content hubs. This article will explore the most common bugs that affect the Linux kernel and how you can secure the kernel against vulnerabilities and attacks.
Notorious Linux Kernel Security Bugs

While protocols such as blockchain are protected by encryption, Linux has its own open-source community, where many “eyes” scrutinize the technology for security bugs. However, kernel vulnerabilities are still an ongoing, serious threat to all Linux-based systems.
Many Linux kernel bugs can cause security issues. These can be easily exploited by remote cyber attackers, often without any human error on the part of the victim—even if all other security technologies and measures are robust, a Linux kernel bug can render your systems vulnerable to DoS (denial of service) attacks, privilege escalation, and other forms of cyberattacks, and cyberwarfare.
Here are a few notorious recent Linux kernel bugs:
· CVE-2017-18017: This bug can affect all kernel versions up to 4.11. It can be found in the netfilter tcpmss_mangle_packet function, which helps filter network communications. This bug can result in DoS attacks and overflow.
· CVE-2016-10229: This bug can affect all kernel versions up to 4.5. It can be found in udp.c. This bug can enable remote attackers to use UDP traffic to execute code.
· CVE-2016-10150: This bug can affect all kernel versions up to 4.8.13. It can allow hackers to carry out DoS attacks and gain unauthorized admin privileges.
· CVE-2015-8812: This bug can affect all kernel versions up to 4.5. It can enable remote attackers to carry out DoS attacks using crafted packets.
· CVE-2014-2523: This bug can affect all kernel versions up to 3.13.6. It is caused by DCCP header pointers used incorrectly and enables remote attackers to execute code via DCCP packets or carry out a DoS attack that crashes the system.
Top Tips for Securing the Linux Kernel Against Vulnerabilities and Attacks
Thankfully, there are several ways you can keep your Linux kernel secure against bugs:
Keep the Kernel Version Updated and Apply Security Patches
As most vulnerabilities are fixed by patches, the most important thing you can do is to keep your kernel version up to date. Apply security patches as soon as they are available. Tracking distribution security advisories is a good way of keeping updated on new patches.
You can apply kernel security patches in the following ways:
Update the kernel from the command line: Although this method requires rebooting the system, it may be the most accessible as the documentation of your Linux distribution probably covers how to do so.
Use kexec system call for quicker reboots: Using the kexec system call enables administrators to speed up the rebooting process. However, while this method is faster, it can result in loss or corruption of data.
Update the kernel without rebooting the system: To avoid rebooting the system entirely, you can use a live kernel patching tool (e.g., Ksplice, Kgraft, Kpatch, KernelCare, or Livepatch). However, this method only applies critical patches and fixes for vulnerabilities and bugs; it is not as exhaustive as a full kernel upgrade.
Enable Kernel Module Signing and Module Loading Rules
Enabling kernel module signing (which uses digital signatures) on loadable kernel modules ensures that only verified modules can be loaded. This reduces the attack surface of your system. Of course, disabling modules will reduce the attack surface further and likely prevent your system’s essential processes.
CONFIG_MODULE_SIG enables administrators to configure the kernel module settings. The kernel can be configured to require specific digital signatures. The hash algorithm can also be changed, and automatic module signing can be enabled during the build phase. The sysctl kernel.modules_disabled=1 command can also help direct communication with the kernel.
Use Linux Kernel Lockdown

The Linux Kernel Lockdown configuration option was designed to strengthen the division between the kernel code and userland processes. This stops the root account from being able to modify kernel code. If a root account is hacked or otherwise compromised, enabling this mode makes it significantly harder for this account to compromise other aspects of the operating system.
There are two modes of the Linux Kernel Lockdown configuration:
· The “integrity” mode: This mode is best to use in most cases.
· The “confidentiality” mode: This mode is best for systems that host sensitive data (e.g., the EVM signing key) protected from even the root account. The confidentiality mode prevents administrators from accessing kernel memory entirely.
It is worth noting that using either Linux Kernel Lockdown mode does restrict some administrative features.
Enable UEFI Secure Boot in Full or Thorough Mode
UEFI Secure Boot was developed to stop malicious code from executing on boot. It ensures that only a device’s UEFI firmware can launch code on startup.
Enabling UEFI Secure Boot in either “full” or “thorough” mode can decrease your system’s attack surface. It ensures that only cryptographically-signed firmware can boot the OS, making it more difficult for malicious kernel modules or unsigned rootkits to access systems.
It is worth noting that enabling UEFI Secure Boot requires manual administration when any modules or kernels are upgraded. It also enables Linux Kernel Lockdown by default.
Enable Mandatory Access Control (MAC) With SELinux, or AppArmor
SELinux and AppArmor are two security systems designed to protect against vulnerabilities, server misconfigurations, and zero-day attacks. They provide an extra layer of security and enable granular access control (known as Mandatory Access Control, or MAC) of your security policies.
Depending on your Linux distribution, either one of these systems is probably installed and enabled by default. However, some users disable these systems in response to various issues. This is not recommended, as doing so can leave your system vulnerable to bugs and attacks!
If your system has SELinux or AppArmor disabled, you should enable it immediately. For systems with SELinux, they recommend setting it to permissive mode.
Implement Strict Permissions

Strict permissions are the cornerstone of system security, and administrators should make permissions very strict while retaining the functionality of a system. This applies whether you are using a single pane of glass system or something more complex.
The basic settings that should be applied are:
Executive code and read-only data must not be writable: When kernel memory and read-only data are writable, execution flow can be reconfigured, and security is breached. Although most architectures have these unwritable by default, you should still check the settings to make sure.
Function pointers and sensitive variables must not be writable: These can be configured to be read-only by changing their settings to “const.”
Kernel memory must be segregated from userspace memory: When kernel memory and userspace memory are shared, attackers can access both if they breach security. Segregating these reduces the damage that attackers can do. This is achievable with emulation or with hardware-based rules.
Harden the sysctl.conf File
The sysctl.conf file is vital for system security. This file is the central configuration point for kernel parameters. Using secure defaults is recommended here.
You can also use the /etc/sysctl.conf file to configure settings to increase overall system security. Security can be hardened by limiting network-transmitted configuration for IPv4 and IPv6, enabling execshield protection and source IP address verification, and logging suspicious packets.
Use the Linux Auditing System (AuditD) for Ongoing System Monitoring
Whether your organization is a store or a software development firm using IBM cloud modernization to streamline your auditing process, monitoring the activity of your essential systems is recommended if you want to be aware of any potential issues.
Regular audits are crucial when it comes to security. Administrators should regularly check syslogs for any suspicious or unexpected activity.
While manual audits are recommended periodically, a handy feature of the Linux kernel automatically collects system activity information. AuditD, which is installed on most distributions by default, logs information that can be used to investigate potential security violations.
While AuditD has its own auditing rules, it is recommended to configure it (e.g., check that logs are stored in a secure and centralized location such as a bespoke server and integrate with a software integration tool), and set any additional rules necessary.
A combination of regular manual and automatic system auditing is usually the strongest.
Key Takeaways
From workplace communications with a VoIP device to repositories of sensitive data, organizations have plenty of information that must be protected from cybercriminals. Linux distributions are becoming increasingly popular and attractive targets for security breaches, so it is more critical than ever that Linux security is watertight.
Linux kernel bugs are one of the biggest threats to overall system security. Following the tips and best practices covered here can help you avoid destructive bugs and keep your system secure.
We Provide consulting, implementation, and management services on DevOps, DevSecOps, DataOps, Cloud, Automated Ops, Microservices, Infrastructure, and Security
Services offered by us: https://www.zippyops.com/services
Our Products: https://www.zippyops.com/products
Our Solutions: https://www.zippyops.com/solutions
For Demo, videos check out YouTube Playlist: https://www.youtube.com/watch?v=4FYvPooN_Tg&list=PLCJ3JpanNyCfXlHahZhYgJH9-rV6ouPro
If this seems interesting, please email us at [email protected] for a call.
Relevant Blogs:
Never Use Credentials in a CI/CD Pipeline Again
Enhancing Collaboration and Efficiency in DataOps With Git
Comparing Cloud Hosting vs. Self Hosting
Microsoft Azure Key Vault Service
Recent Comments
No comments
Leave a Comment
We will be happy to hear what you think about this post