Securing Tomorrow: Unleashing the Power of Breach and Attack Simulation (BAS) Technology
As the cybersecurity landscape continues to evolve, the challenges associated with defending against cyber threats have grown exponentially.
As the cybersecurity landscape continues to evolve, the challenges associated with defending against cyber threats have grown exponentially. Threat vectors have expanded, and cyber attackers now employ increasingly sophisticated tools and methods. Moreover, the complexity of managing security in today's distributed hybrid/multi-cloud architecture, heavily reliant on high-speed connectivity for both people and IoT devices, further compounds the challenges of #cyberdefense.
One of the foremost concerns for corporate executives and boards of directors is the demonstrable effectiveness of cybersecurity investments. However, quantifying and justifying the appropriate level of spending remains a formidable obstacle for most enterprise security teams. Securing additional budget allocations to bolster an already robust security posture becomes particularly challenging in the face of a rising number of #cyberbreaches, which have inflicted substantial reputational and financial harm on companies across diverse industries.
The modern enterprise's IT infrastructure is an intricate web of dynamic networks, cloud resources, an array of software applications, and a multitude of endpoint devices. These enterprise IT ecosystems are vast and intricate, featuring a myriad of network solutions, a diverse array of endpoint devices, and a mix of Windows and Linux servers. Additionally, you'll find desktops and laptops running various versions of both Windows and macOS dispersed throughout this intricate landscape. Each component within this architecture boasts its own set of #securitycontrols, making the enterprise susceptible to #cyberthreats due to even the slightest misconfiguration or a shift towards less secure settings.
In this environment, a simple misconfiguration, or even a minor deviation towards less secure configurations, can provide attackers with the foothold they need to breach an organization's infrastructure, networks, devices, and software. It underscores the critical importance of maintaining a vigilant and proactive approach to cybersecurity in this ever-evolving digital era.
As organizations look for ways to demonstrate the effectiveness of their security spend and the policies and procedures put in place to remediate and respond to security threats, vulnerability testing can be an important component of a security team’s vulnerability management activities. Organizations use several testing approaches as part of their vulnerability management practices. Four of the most common are listed below:
- Penetration testing is a common testing approach that Enterprises employ to uncover vulnerabilities in their infrastructure. A Pen test involves highly skilled security experts using tools and attack methods employed by actual attackers to achieve a specific pre-defined breach objective. The pen test covers networks, applications, and endpoint devices.
- Red teaming: A red team performs “ethical hacking” by imitating advanced threat actors to test an organization's cyber defenses. They employ stealthy techniques to identify security gaps, offering valuable insights to enhance defenses. The results from a red-teaming exercise help identify needed improvements in security controls.
- Blue teaming is an internal security team that actively defends against real attackers and responds to red team activities. Blue Teams should be distinguished from standard security teams because of the mission to provide constant and continuous cyber defense against all forms of cyber-attacks.
- Purple teaming: Purple teams aim to align red and blue team efforts. By leveraging insights from both sides, they comprehensively understand cyber threats, prioritize vulnerabilities, and offer a realistic APT (Advanced Persistent Threat) experience to improve overall security.
Although organizations commonly use these vulnerability testing approaches, there are several challenges associated with them:
- These approaches are highly manual and resource-intensive, which, for many organizations, translates to high costs and a lack of skilled in-house resources to perform these tests.
- The outcome of these vulnerability tests provides vital information back to the organization to act on. They are performed infrequently due largely to the cost and lack of skilled resources mentioned previously.
- These
methods provide a point-in-time
view of an organization’s security posture, which is
becoming less effective for companies moving to a more dynamic cloud-based
IT architecture with an increasing diversity of endpoints and
applications.
Traditional vulnerability testing approaches yield very little value because the security landscape and enterprise IT architectures are dynamic and constantly changing.
Since testing organizations' cybersecurity posture is becoming a top priority, it triggered an increased demand for the latest and most comprehensive testing solutions. Moreover, from a practical standpoint, it's almost impossible for multiple enterprise security teams to manually coordinate their work and optimize configurations for all the overlapping systems. Different teams have their own management tasks, mandates, and security concerns. Additionally, performing constant optimizations and manual testing imposes a heavy burden on already short-staffed security teams. This is why security teams are turning to Breach and Attack Simulation (BAS) to mitigate constantly emerging (and mostly self-inflicted) security weaknesses.
Definition: Breach and Attack Simulation (BAS)
Gartner defines Breach and Attack Simulation (BAS) technologies as tools “that allow enterprises to continually and consistently simulate the full attack cycle (including insider threats, lateral movement, and data exfiltration) against enterprise infrastructure, using software agents, virtual machines and other means.”
BAS tools replicate real-world cyber attacker tactics, techniques, and procedures (TTPs). They assist organizations in proactively identifying vulnerabilities, evaluating security controls, and improving incident response readiness. By simulating these attacks in a controlled environment, organizations gain valuable insights into security weaknesses, enabling proactive measures to strengthen overall #cybersecurity.
BAS automates testing threat vectors, including external and insider threats, lateral movement, and data exfiltration. While it complements red teaming and penetration testing, BAS cannot entirely replace them. It validates an organization's security posture by testing its ability to detect a range of simulated attacks using SaaS platforms, software agents, and virtual machines.
Most BAS solutions operate seamlessly on LAN networks without disrupting critical business operations. They produce detailed reports highlighting security gaps and prioritize remediation efforts based on risk levels. Typical users of BAS technologies include financial institutions, insurance companies, and various other industries.
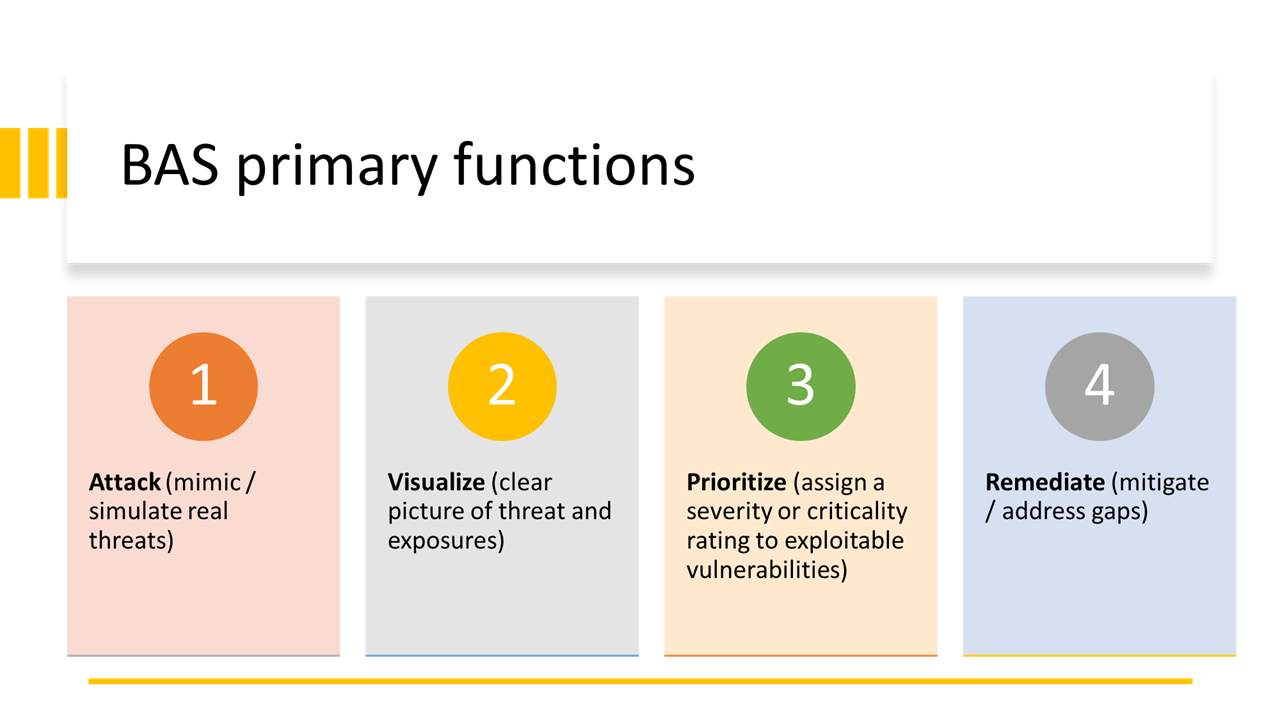
BAS Primary Functions
Typical BAS offerings encompass much of what traditional vulnerability testing includes, but it differs critically. At a high level, BAS's primary functions are as follows:
- Attack (mimic / simulate real threats)
- Visualize (clear picture of threat and exposures)
- Prioritize (assign a severity or criticality rating to exploitable vulnerabilities)
- Remediate (mitigate/address gaps)
BAS differs from traditional approaches in the use of closed-loop automation that allows IT/security teams to evaluate an environment for threat indicators and attack behaviors, unprotected assets, misconfigurations, human errors, log gaps, and basic IT hygiene issues. Armed with this information, security personnel can take the recommended actions to close gaps, fix misconfigurations, and strengthen credential management. The other key differentiator for BAS is in the variety of ways (on-demand, continuous, or set interval) vulnerability tests can be performed. This gives security teams much greater flexibility in the frequency with which they can conduct vulnerability tests.
Three Categories of BAS Technologies
BAS technologies fall into three main categories, depending on the approach they use:
- Agent-based vulnerability scanners: This category involves deploying agents directly on target devices within an organization's LAN to identify known vulnerabilities. These agents are distributed across multiple machines, helping map potential attack paths within the network. Unlike remote protocols like SSH, this approach focuses on assessing devices from within.
- Malicious traffic generation: BAS tools in this category evaluate an organization's security by generating simulated 'malicious' traffic within the internal network. Virtual machines are set up as targets, and a database of attack scenarios is used. The BAS initiates attacks between these machines and assesses the organization's security solutions to ensure they can detect and block such traffic.
- Multi-vector simulated attacks: Among the most advanced and true-to-life simulations, this 'black box' approach deploys lightweight agents on workstations within the network. Typically cloud-based, these assessments employ diverse attack tactics to test the internal and external security within the organization's LAN.
These categories encompass various methods of assessing an
organization's cybersecurity defenses and readiness, each with its own
strengths and suitability depending on the organization's specific security
needs and goals.
More security controls do not
make your enterprise more secure.
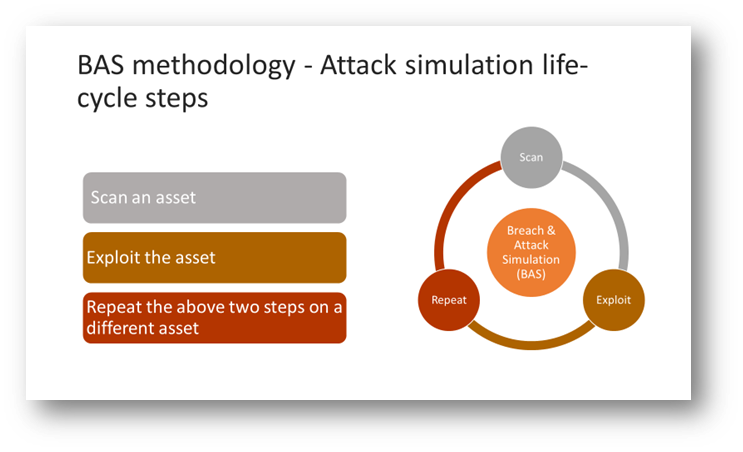
BAS Methodology: Attack Simulation Life-Cycle Steps
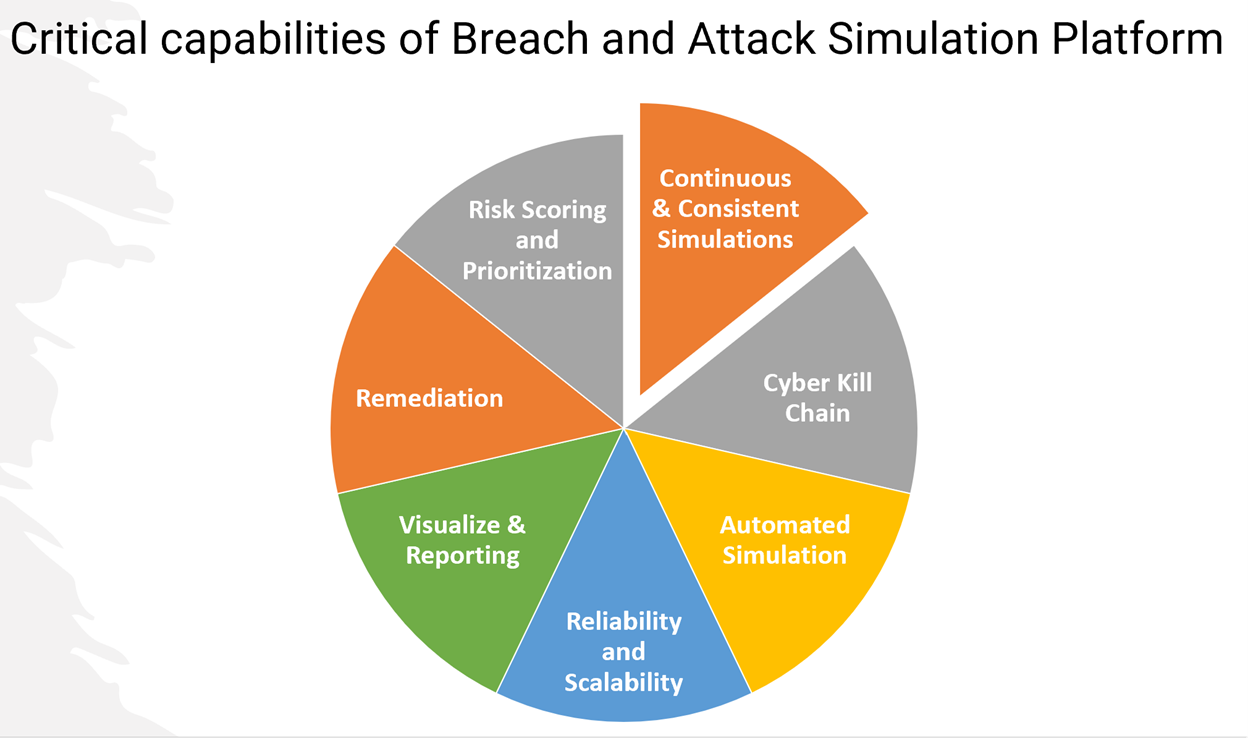
Critical Capabilities of BAS
In the realm of cybersecurity, Breach and Attack Simulation (BAS) solutions stand as indispensable tools, demanding a specific set of critical capabilities to excel within the complexities of the modern enterprise. While BAS technologies offer a versatile range of applications for security and risk management teams, it's common for buyers to focus on only a subset of these capabilities. For Security and Risk Management (SRM) leaders, the evaluation of BAS capabilities becomes paramount in gauging their potential to enhance security postures and mitigate exposure to evolving threats.
- Continuous and consistent simulations
- Cyber kill chain
- Automated simulation
- Reliability and scalability
- Visualize and reporting
- Remediation
- Risk scoring and prioritization
- Simple to configure and deploy: It's crucial that the BAS platform operates without demanding intricate configurations to effectively execute attack simulations within the network. Complex setups could place undue burdens on security teams and hinder reporting processes.
- Offer the flexibility of deployment model (e.g., SaaS and an on-premises). Currently, most regulated environments (financial services, health care, government) require on-premises deployment. BAS platform must support major cloud environments, including Microsoft Azure, AWS, and GCP. A BAS solution must accommodate these evolving hybrid architectures.
-
BAS
tools should run attack simulations continuously, consistently, and
automatically. They assess validity and efficacy, such as whether the
network segmentation is working and which types of vulnerabilities are
accessible. Also, they ensure that security tools are operating as
designed — for example, detecting and blocking known threat techniques. BAS tools provide a view of multiple, if
not all, stages of the cyber kill chain and where threat campaigns will
likely be successful.
The continuous simulations enable the enterprise to progressively improve its security posture. - A scalable BAS platform must have the ability to abstract individual results and automatically deduce mitigation actions so that security and infrastructure teams can work holistically at a higher level to improve security posture based on business risk. BAS solutions should bring together critical data to help an organization understand its overall security posture. BAS platform should be able to detect misconfigurations and security holes and should go further to clearly indicate the highest priority mitigations. This lets security teams accomplish more with fewer resources and move from a reactive to a proactive security stance, providing their organization with far greater assurance that IT infrastructure and data are — and will remain — secure.
- BAS Platform must have a clear process for keeping up on the latest threat landscape and the research-backed product roadmap and release strategy.
- BAS Platform must have an ever-evolving library of Safe malware samples that will trigger security controls but will never impact production environments.
-
BAS
tools should support reporting frameworks like MITRE ATT&CK
to represent details on specific methods if the security control was
circumvented and prove which attacks worked and which ones failed.
Ransomware is a common threat often covered well by BAS tools to answer
the question: “Am I at risk to ransomware?” BAS can be used to report on specific
named “threat” or “threat actor” perspectives, where you
may want to answer a question such as, “How might
breach my environment?” BAS platform adoption can bring together different security teams by applying a risk rating approach that is driven by comprehensive data. To make this capability broadly useful, a good BAS platform should support: - Dashboards- Key Risk indicators: Risk indicators help track your organization’s progress, validate that your security posture is improving, and understand trends over time. The types of risk indicators tracked should reflect what your organization cares about most. For example, % of attack attempts that pass through defenses, the success rate of defense against attacks is measured as the percentage of blocked MITER framework attacks. An organization may want to calculate risks against its critical segments and elevate the risk value of services that involve business-critical transactions or store healthcare data and PII. A BAS should make it easy to select, calibrate, and then measure against these indicators.
-
Heat
mapping and visualization tools: Utilizing heat
mapping and visualization tools within the framework of MITRE ATT&CK
provides a shared language for the cybersecurity community. By harnessing
the ATT&CK navigator, a BAS platform can create heat maps that
illuminate vulnerabilities, facilitating collaborative efforts among
teams for remediation. Simulating a wide range of attacks, including
those associated with specific threat groups or techniques targeting the
organization, proves highly valuable. Heat maps generated from simulation
results swiftly direct teams' attention to areas of vulnerability. When
integrated into the MITRE ATT&CK framework, these heat maps offer a
comprehensive overview of the security posture concerning all tested
attacks. This visual aid assists teams in selecting tests that delve into
specific attack techniques, providing a detailed view of detected and
prevented simulations and available remediation options.
Note: Immersive and interactive visualization capabilities empower security teams to comprehensively assess and understand their organization's entire attack surface - Mapping attack paths: To help teams properly prioritize different mitigation tasks, it is valuable to visualize how attacks may reach an asset from the outside. A map or diagram of the kill chain helps the information security team see how to break the chain most efficiently. A rich visualization capability helps security teams comprehend and assess the entire attack surface of their organization. Visual interaction like zooming in or out of different parts of the infrastructure or filtering results based on key attributes can be a nice value add. The visualization helps with prioritization by enabling teams to see and analyze the kill chains of the highest-threat security risks identified by the BAS. Visualizations can also show an attack's entire series or steps, from initial infiltration modalities, host compromises, lateral movements, and propagation to exfiltration, sequestration (ransomware), or destruction (wiping attacks).
- Executive and automated reporting: While executive reports may not impact the prioritization of day-to-day operations, they help teams communicate their strategy for prioritizing security actions and allocating security assets. Key expected features of executive reports in a BAS solution are:
- Depict clear picture organization-wide security posture.
- Supporting business cases for configuration or strategy changes.
- Assisting business case development, such as budget requests.
- Reflecting real-time trends and activities in the security landscape.
- Detailing security posture concerning specific Threat Group TTPs
- Self Service Analytics
- Enabling configuration of alerts based on progress tracking over time.
- Accurate prioritization with manual prioritization override: Because a BAS platform will continually run hundreds of thousands of breach methods to test the efficacy of all your security solutions and controls across known TTPs, this generates an enormous number of alerts and suggestions for mitigation. Features such as risk scores, heat maps, and network exposure maps help security teams and leaders see and quantify the areas to focus on for remediation. A well-designed BAS platform will aggregate results from all the simulations to provide holistic remediation actions, which is more efficient than fixing security gaps one by one. Categories like network, web, endpoint, and email should group threats. This makes it more feasible to coordinate security, IT, network, endpoint, and risk team efforts in a holistic remediation plan. To help security and infrastructure teams remediate the most critical security gaps first, the BAS solution should prioritize suggested mitigation actions in a stack ranked by business risk. The BAS platform should create a top-priority unified workspace or dashboard where the full team can focus on the highest priority remediations to improve security posture based on business risk. For example, updating one rule in a NextGen firewall may greatly impact protecting the most valuable IT assets of a business or a customized patch management priority list focused on mitigating business risk. BAS Platform should provide accurate prioritization capabilities to prevent a “remediation paralysis dilemma.” While I expect the BAS tool prioritization engine to do its job effectively, I would suggest the BAS tool needs to support manual override and schedule.
These help users to easily absorb and comprehend BAS simulation findings and recommended next steps. More specifically, this risk and prioritization capability should include the following components:
- BAS should be able to calculate the exposure time from discovery of a breach until it is resolved, as well as the success rate of remediation, to track:
- Efficiency and responsiveness of a security team
- Effectiveness of improving security posture
- Using BAS only for diagnostics is not enough, and wisdom comes from actioning the recommended improvements in the areas described below. In other words, a good tool should help drive remediation, not simply tell what’s not going well.
- BAS platforms should be able to scale intelligently: To scale intelligently and easily, the BAS platform needs to determine which attacks should run against specific points in the attack surface. It must be able to determine automatically which types of attacks to run, where to run them in the infrastructure, and in what sequences or rotations. For example, a BAS platform should run Linux attacks only on Linux servers and Windows Servers attacks only on Windows Servers.
- BAS platform should recognize the context of IT assets and, for example, run data exfiltration exploits only against databases and other parts of the data infrastructure. This intelligence in using these capabilities helps the BAS system scale automatically to a large organization without stressing the operations team. In addition, the BAS needs to be able to test attack playbooks across the entire kill chain to spot enhanced security remediation opportunities, even if the attack was blocked higher up in the chain by a control or other remediation measure.
-
BAS
platforms should not require manual tuning and interactions to configure
attack profiles and simulation parameters. For a BAS platform to
report accurately on enterprise security posture, it must run in the
production environment and not in a mirrored production environment. Running
simulations in a lab or air-gapping them from production does not
effectively test all the moving parts of a real enterprise network. For a
BAS Platform, it’s
important to distinguish between running simulations “in production” and
“running against production applications.”Simulations must not impact live
applications or services.BAS platform must ensure no interaction with real
live production systems occurs while performing simulated attacks. The
simulators must be installed in production traversing the production
network, and they must represent and run on all the endpoints in the
enterprise (Windows desktop OSs, Windows Servers OSs, Linux Server OSs,
Mac OSs) and their security settings.
Note: Running simulations that interact with live production applications would introduce the risk of causing downtime, lost revenues, and excessive burdens on IT security and DevOps teams. If a BAS platform takes down or slows down any production services, then it will likely face resistance from the production support team and application owners. - BAS platform framework should ensure that any operation carried out as part of BAS activity is completely reversible and easy to roll back programmatically. This ensures the safe execution of the attacks in a production environment. "Ensure all BAS operations can be undone."
- A BAS platform should be easy to use and measurably increase the ease of use of other security tools and controls that an organization uses. Most security teams suffer from “tool sprawl,” which has added significant complexity to their jobs. Tool sprawl makes it harder to maintain security due to the complexity of using and configuring 70 to 100 security controls in place to guard against threats and maintain accurate awareness of how they work in combination.
- Enterprise-ready BAS should start by testing every security control for each solution by simulating attacks to infiltrate, exploit hosts, move laterally, and exfiltrate data. This BAS process will serve as the single testing point across all controls, simplifying the cumbersome process of manually verifying or tuning penetration testing systems.
- An effective BAS should fit without friction into existing workflows and not require additional separate workflows or significant professional services to be effectively integrated and work properly. BAS Platform should support SOAR, SIEM, ITSM tool integration, and other automated workflows and processes. Integrations with workflow systems can be used to trigger processes for additional information-gathering configuration changes and analyst approvals that are required to direct mitigation and remediation of issues. Over time, these bi-directional workflow integrations improve the security posture and reduce the risk of a breach by improving the ability of the security team to quickly and effectively mitigate issues discovered by BAS.
- BAS Platform should support automated analysis of security events — technology integrations: Understanding how the security ecosystem responds to each type of attack is key to improving the security posture. BAS platforms must integrate with endpoint, network, and SIEM solutions to automatically correlate security events to simulated attacks. This saves significant time for the security team in analyzing and searching for key events and recognizing gaps. Effective integration enables the BAS platform to automatically determine if the security ecosystem prevented, detected, or completely missed a simulated attack.
- BAS solution must support Role Based access (RBAC) assignment — For example — Executives can view reports and dashboards, while blue teams can configure and execute the various simulations. Red teams would be unique in having the ability to create new and custom breach methods.
- BAS Solutions should be able to deploy simulators of various operating systems, including Windows, Linux, and MacOS.
- Covering known threats is not enough. A comprehensive BAS platform must have sufficient coverage of attacker behaviors and general cybersecurity tactics, techniques, and procedures to cover unknown threats and patterns that may not be obvious. Ideally, this coverage will leverage well-known attack information sources like GitHub and Reddit. Each organization should be able to determine which information sources are the most important and add those attacks to continuously update the attack playbooks.
Real World Use Cases for Breach and Attack Simulation (BAS) Technologies
To get true value from BAS Technologies, the organization needs to select BAS tools carefully and deploy them to cover the below nine use cases:

1. Attack Technique, Security Posture and Readiness Assessment
With automated attacks escalating and growing in volume and severity, attackers try numerous exploits and test different types of weaknesses when they attempt to breach a target. Additionally, hackers can often ascertain which security controls and systems an organization is running and tune their attacks to map to the blind and weak spots of those systems.
Ensure you use BAS tools' comprehensive playbook to draw upon, containing attack tactics, techniques, and procedures (TTPs) covering all Advanced Persistent Threats (APTs).
Validating and tracking the security posture of complex and dynamic environments is extremely challenging and burdens security and operations teams. Ensure you use the BAS platform to cover the major attack surfaces: network, endpoint, cloud, and email. For example, test all major operating systems you run on-premises, local and distributed machines, and in the cloud. Use BAS to cover all security controls because they are often subject to inadvertent misconfigurations as part of patching, updating, and other normal IT processes.
Ensure you use BAS Tool to simulate attacks against public and private cloud infrastructure (IaaS), addressing the control plane, including IAM, network, storage, and administrator access. Moving up the cloud technology stack and addressing the data plane is crucial, covering lateral movement, system abuse, privilege escalation, and running unapproved processes. With attacks now focusing on container-based applications, do use the BAS platform for Containers (e.g., Docker, Kubernetes).
Many BAS vendors leverage the MITRE ATT&CK framework to build dashboards that enable users to categorize findings and facilitate a discussion about exposure reduction and security readiness. Organizations should use attack simulation to hypothesize the outcomes of real-world scenarios and obtain an attacker’s view of their environment.
For example, the security operations team should use the BAS tool to simulate/emulate a high-profile threat technique related to 'known threat actor groups.' By doing this, the BAS tool should be able to show how a possible first step of the breach (also known as “named attack”) would work without the risks or approval required for traditional penetration testing. They would be able to utilize the results from the simulation to prepare accordingly.
2. Security Control Validation and Efficacy
This is a core function of BAS tools. In-depth attack coverage
is imperative for BAS to ensure the enterprise is secure from all known
attacks. For efficiency and better interpretation of results, the BAS platform
should emphasize and give testing priority to attack methods that are
potentially damaging today.
Just because an attack is
known, it does not make it currently relevant in today’s infrastructure.
Threat exposure may be due to poorly configured security controls, lack of security controls, or inadequate processes and procedures. Simulations assist teams trying to identify how to optimize existing security technology deployments. The simulation ascertains if current security technologies are configured properly to:
- Detect active threats.
- Investigate instances where existing threat detection controls are not performing as expected.
- Identify areas where current security controls may have failed or succeeded, highlighting potential configuration issues or gaps in capabilities required for threat detection and prevention. The insights provided offer detailed guidance to enhance existing controls.
- Evaluate the processes followed by security operations teams, pinpointing areas for improvement to better prevent, detect, and respond to simulated threats.
- Assess the security controls' functionality and the security team's preparedness to respond effectively, including their skill set.
- Validate configuration changes and product updates to ensure they haven't caused configuration drift, potentially introducing new or unforeseen security control gaps.
Organizations should use BAS platforms to focus on specific tactics or techniques. For example, they will require the ability to test TTPs of specific threat groups that are a high priority for the organization. The team may decide to run all tactics and techniques associated with a specific threat group across all simulators in the enterprise. If an inquiry such as “How secure are we against threats x, y, and z?” comes from the executive suite or the board, the BAS platform should be able to quickly provide the answer.
Simulated attacks must be as close as possible to a real attack (!! Remember: Real Attacks Matter). For example, running a network recording of an attack is different than actually conducting the attack between two live, real entities running in a production or near-production environment. Likewise, scanning the environment and configurations and deducing the potential success of an attack is not equivalent to performing the attack and seeing the outcome.
3. Support Mergers and Acquisitions (M&A)
BAS technology can play a pivotal role in the context of mergers and acquisitions (M&A) by offering a unique avenue for organizations to gain valuable insights into the security posture of potential acquisition targets. Traditionally, organizations deploy BAS solutions after completing an M&A transaction to assess and reconcile security discrepancies. However, there is an emerging trend of utilizing BAS even before the acquisition to proactively evaluate the target company's security resilience.
The typical M&A process often restricts access to the target company's environment until the completion of the acquisition. This limitation hinders organizations from assessing the security landscape beforehand. Nonetheless, deploying BAS technology in this pre-acquisition phase offers several advantages.
- Visibility into the target company's security tools
- Informed integration timelines
- Tool selection and replacement
- Risk mitigation
Incorporating BAS technology into the M&A process streamlines post-acquisition security efforts and contributes to making informed decisions throughout the acquisition journey. It empowers organizations to navigate the complexities of merging two security landscapes effectively and ensures a smoother transition while preserving the integrity of both entities' security postures.
4. Third-Party Assessments
In an era where interconnectedness is paramount, organizations often collaborate with supply chain partners, vendors, and third-party entities to optimize their operations. However, these collaborations introduce a critical consideration: Security. To safeguard their networks and sensitive data, organizations frequently request that their partners undergo security assessments before gaining access to their systems. Frequently, organizations request that their supply chain partners perform a self-assessment of their security controls, should they want or need to connect to the organization’s network. BAS solutions can test without divulging or providing access to sensitive data, which addresses some of the privacy concerns of prospective partners.
BAS technology can play a vital role in enhancing third-party assessments while addressing privacy concerns.
- Facilitating secure collaboration
- Privacy-preserving security testing: One of the significant advantages of using BAS for third-party assessments is its ability to conduct comprehensive security testing without divulging or providing access to sensitive data. BAS cab acts as an impartial evaluator, assessing the effectiveness of security controls without compromising data privacy.
- Tailored reporting
- Alternative to security rating services (SRSs): While security rating services (SRSs) offer an alternative option for third-party assessments, BAS stands out as a more robust and versatile choice. SRSs primarily rely on automated reviews of publicly available data, which may not comprehensively evaluate security controls. On the other hand, BAS actively simulates attacks and assesses security measures in a controlled environment, offering a more in-depth analysis of security readiness.
- Third-party assessments powered by BAS contribute to building trust between organizations and their partners. By ensuring that partners adhere to security standards, organizations can collaborate with confidence, knowing that their network and data are safeguarded. This proactive approach strengthens security and fosters a secure and collaborative ecosystem.
5. Complement Penetration Testing
BAS introduces a transformative approach to security assessments that distinguishes it from traditional Penetration Testing and Vulnerability Management tools. While both Penetration Testing and Vulnerability Management have their merits, they often necessitate substantial manual guidance, resulting in increased workload and noise for security teams. On the other hand, BAS offers a complementary solution that expands the scope and frequency of security posture assessments in a more automated and cost-effective manner.
BAS is fundamentally different from legacy Penetration Testing and Vulnerability Management tools. Both approaches require substantial manual guidance and create more work and noise for your security teams.
Penetration testing is often performed at a point in time and normally has a specific scope that covers only a small portion of an environment. Although BAS is not a replacement for traditional penetration testing, it supplements this process to drastically increase the scope and frequency of security posture assessments and potentially at a considerably lower cost.
BAS provides a simulation of predefined attacker techniques and has lower assurance when compared to pen testing (and red teaming). Vulnerabilities are not being tested fully, nor is the process testing accessibility to the network. BAS enriches an organization's security strategy by offering continuous, broad-spectrum security assessments that complement traditional penetration testing. By leveraging the strengths of both approaches, organizations can enhance their security posture, reduce risks, and adapt to the evolving threat landscape in a more agile and cost-effective manner.
Note: Combining the attack simulation with the depth and sophistication of Penetration testing can provide a more consistent and iterative value than relying simply on one approach.
6. Unlocking Risk-Based Vulnerability Management (RBVM)
BAS and vulnerability assessment (VA) tools are complementary technologies. BAS technology offers functionality to identify which vulnerabilities will likely be successfully exploited in the environment. Testing vulnerabilities and their exploitation is a core feature of many BAS tools.
BAS can be leveraged to help with vulnerability prioritization. For example, if a vulnerability cannot be patched for any business or technical reasons, BAS tools deliver insights into “how” an asset may be compromised. Also, they provide the means to test the efficacy of the already deployed security controls and whether those compensating controls adequately address the common vulnerabilities and exposures (CVE) discovered.
The synergy between BAS technology and Vulnerability Assessment (VA) tools is a cornerstone of robust Risk-Based Vulnerability Management (RBVM). While VA tools excel at identifying vulnerabilities within an environment, BAS technology complements this by assessing which of these vulnerabilities are most likely to be successfully exploited.
Organizations must plan to use the BAS tool to enrich RBVM:
- Vulnerability prioritization: When certain vulnerabilities cannot be promptly patched due to business or technical constraints, BAS steps in to provide critical insights into the "how" of potential asset compromise. It goes beyond merely identifying vulnerabilities and delves into assessing the likelihood and consequences of successful exploitation. This information becomes instrumental in prioritizing vulnerabilities for remediation based on their real-world risk.
- Evaluating security controls: BAS tools offer a unique vantage point to evaluate the efficacy of deployed security controls. They probe whether the existing security mechanisms, including compensating controls, effectively address the identified Common Vulnerabilities and Exposures (CVEs). By simulating attacks that attempt to exploit known vulnerabilities, BAS validates the resilience of these controls. This verification ensures that security defenses are aligned with the current threat landscape and can thwart potential threats effectively.
- Holistic security posture assessment: RBVM is not solely about managing individual vulnerabilities but also about evaluating the overall security posture. BAS extends its capabilities to assess vulnerabilities' collective impact and potential exploitation on the organization's security posture. It helps security teams understand the systemic vulnerabilities that may arise from the interaction of multiple CVEs and provides actionable insights to mitigate these risks comprehensively.
- Continuous monitoring: RBVM is an ongoing process; vulnerabilities can emerge or evolve over time. BAS technology complements this need by facilitating continuous monitoring and assessment. It allows organizations to stay vigilant by simulating evolving attack techniques and adapting security controls accordingly.
7. Support Red and Purple Teams Activities
A robust BAS platform can serve as a dynamic ally for Red and Purple teams, facilitating their activities by offering scalability and versatility previously unattainable. These teams play a pivotal role in identifying vulnerabilities and weaknesses within an organization's security infrastructure. To support their endeavors effectively, an extensible BAS platform is indispensable.
An extensible BAS platform allows Red teams to scale their operations and conduct broader testing coverage. This scalability enables red teams to simulate various attack scenarios and comprehensively explore potential vulnerabilities.
Purple teaming in most organizations struggles to deliver value due to:
- Limited scenario realism: Purple teams struggle with realistic attack simulations. BAS offers a library of authentic attack scenarios based on real-world threats.
- Resource and skill constraints: BAS automates attack simulations, reducing the need for extensive personnel. Purple teams can focus on analysis.
- Lack of attack coverage: Purple teams often miss diverse attack vectors. BAS provides comprehensive attack coverage across various domains.
- Limited post-attack analysis: Manual analysis is time-consuming. BAS automates data collection and report generation for efficient post-attack assessment.
- Difficulty in tracking progress: BAS offers tracking and reporting tools, enabling purple teams to monitor security enhancements and measure progress over time.
By leveraging BAS, purple teams can overcome these challenges and enhance their effectiveness in improving security resilience.
In this context, Red Team and Purple Team can benefit from the BAS Platform with the following:
- Ability to combine building blocks of attacks that already exist in the platform to develop new attack combinations. Organizations should be able to run common attack simulations, replicating the approach and methods of genuine threat techniques in a controlled manner via automated and repeatable tasks. This enables organizations to execute timely and pragmatic improvements iteratively and improve their existing technologies and processes.
- Custom scenario modules that allow offensive security practitioners to blur the lines between simulation and real testing (taking the scope of BAS tools beyond attack simulations!!)
- Adding new attacks: Red teams benefit from the ability to introduce new attack methods through various means, including network recording (PCAP) or programming languages like Python.
- Rapid response to emerging threats: BAS platforms should be capable of swiftly covering newly introduced threats. When a new threat is identified and reported through channels like CISA or US-CERT alerts, security teams must have the means to promptly test their defenses against it. BAS vendors typically commit to shipping comprehensive sets of simulations for any newly identified or emerging threats within a short timeframe, typically within weeks/days. This ensures that organizations can promptly and effectively validate their defenses, aligning with modern cyber threats' dynamic nature.
8. Measurement of SecOps Processes and ‘Defenders’ Enablement
Measuring the effectiveness of security operations center (SOC) processes has always been challenging. However, BAS tools help enhance SOC processes and empower defenders, such as incident responders, in multiple ways.
- Quantifying SOC performance: BAS tools can maintain a comprehensive timeline and record of all security-related actions taken within the organization. This meticulous tracking will allow defenders to measure the impact of new security tools and processes. It will enable them to establish key metrics like Mean Time to Detect (#MTTD) and Mean Time to Respond (#MTTR). These metrics are crucial for assessing how efficiently security incidents are detected and addressed, providing a clear picture of SOC performance.
- Enhancing incident response planning: BAS tools can serve as a valuable supplement to tabletop exercises, which are essential for incident response planning. BAS tools offer real-time visibility into security exposure by continually testing and retesting various attack scenarios. This dynamic perspective becomes particularly valuable when new security solutions or content are introduced. It allows defenders to assess how these changes affect the organization's ability to detect and respond to threats.
- Facilitating strategic security roadmap: BAS reports can serve as powerful conversation starters when planning the organization's strategic security roadmap. They offer a wealth of metrics related to residual risk, security posture, and attack surface. These metrics provide valuable insights into the organization's security landscape, helping security leaders make informed decisions. Moreover, they play a crucial role in demonstrating security initiatives' return on investment (ROI), validating security budget allocations, and ensuring alignment with strategic security goals. BAS tools measure the effectiveness of SecOps processes and empower defenders with actionable insights. They enable security teams to continuously refine their processes, adapt to evolving threats, and make data-driven decisions that enhance the organization's overall security posture.
9. Actionable Threat Intelligence
In a cybersecurity landscape characterized by rapid and dynamic threats, actionable and adaptive threat intelligence is critical for effective defense. BAS technology elevates threat intelligence from passive information sources to proactive and strategic assets. By leveraging BAS-generated insights, organizations can fortify their security posture, respond agilely to emerging threats, and ensure that their defenses remain resilient in the face of evolving cyber challenges.
BAS solutions can offer a multifaceted approach to threat intelligence, providing valuable insights that empower security teams to make informed decisions and proactively protect their infrastructure. Here's how BAS transforms threat intelligence into actionable strategies:
- Threat profiling: BAS solutions excel in threat profiling, tailoring threat intelligence to suit the organization's specific industry and geographical location. By customizing threat feeds, BAS can ensure that security teams receive information about threats that are directly relevant to their operations.
- Continuous threat monitoring
- Enhancing Purple Teaming exercises: Purple teaming exercises benefit significantly from BAS-generated threat intelligence, where defensive and offensive security teams collaborate to assess security readiness. Armed with BAS insights, security teams can strategically select and simulate relevant threats during these exercises.
- Proactive threat mitigation
- Decision Support: The actionable threat intelligence provided by BAS serves as a valuable decision support tool. Security leaders can use this intelligence to allocate resources, prioritize security initiatives, and make informed choices about which threats require immediate attention. It enhances the overall strategic alignment of cybersecurity efforts with the organization's goals and risk tolerance.
Key Players in the BAS Domain
- AttackIQ Platform
- Cymulate: Exposure Management and Security Validation
- Picus: The Complete Security Validation Platform
- Threat Simulator
- Qualys
- Rapid7
- XM Cyber
- Skybox Security
- SafeBreach
- Firemon
- Verdoin (FireEye)
- NopSec
Note: The above list is not in any order of preference, maturity, or capability mapping. 3rd party links shared on as-is-basis. Please do check the applicability or look for authoritative BAS evaluation from your Security partner or leading research firms.
Future Outlook
The global BAS market is expected to reach $1.68 billion by 2027 — a 37.8% growth from 2018’s figures — primarily driven by demand for prioritizing security investments as vulnerability management grows ever more complicated. BAS technologies were highlighted as one of the top solutions for CISOs to consider in a recent report from Gartner, because of its effectiveness at testing against known threats.
There are a few additional areas where I see BAS technology needs more work:
- Resource Optimization during simulations executed by BAS platforms.
- Zero Trust Architecture (ZTA) Compatibility
- Integration with SOAR and ITSM tools
- Leveraging GenAI for sophisticated, realistic attack simulations.
- Securing emerging technologies like 5G, Blockchain, IoT, GenAI LLM models
- Potential regulatory changes that may impact BAS adoption.
- The adaptation of BAS for cloud-native environments
- Intelligent Management of false positives/negatives during simulations.
- Collaborative Threat Intelligence Sharing
Summary
In conclusion, Breach and Attack Simulation (BAS) stands as a cornerstone of modern cybersecurity, providing enterprises with a powerful arsenal of features and functionalities. Not only does it serve as a litmus test for the effectiveness of security controls, but it also champions a proactive approach to cyber defense through automation. In today's security landscape, where the pursuit of cyber resilience hinges on vigilant monitoring and swift remediation, BAS emerges as a pivotal strategy to minimize the impact of threats on business operations.
Looking forward, BAS is poised to become an indispensable component of an enterprise's cyber defense strategy. However, for BAS to thrive in this dynamic landscape, it must embody the listed critical set of features and capabilities currently and in its future roadmap. Any deficiency in these elements could limit an organization's ability to harness the full potential of BAS technology. It is crucial to underscore that a BAS solution lacking these critical capabilities and integrations could mire an organization into confusion, resource drain, and potential disruptions to production services. Conversely, a fully featured and well-integrated BAS platform serves as a force multiplier, elevating security posture through profound insights into the attack surface and efficient remediation. Such an investment has the potential to pay for itself within a matter of months, empowering information security teams to enhance their effectiveness without the need for additional personnel or the purchase of additional security tools. In this ever-evolving realm of cybersecurity, BAS shines as a beacon of resilience, guiding enterprises toward proactive defense and heightened cyber preparedness.
We Provide consulting, implementation, and management services on DevOps, DevSecOps, DataOps, Cloud, Automated Ops, Microservices, Infrastructure, and Security
Services offered by us: https://www.zippyops.com/services
Our Products: https://www.zippyops.com/products
Our Solutions: https://www.zippyops.com/solutions
For Demo, videos check out YouTube Playlist: https://www.youtube.com/watch?v=4FYvPooN_Tg&list=PLCJ3JpanNyCfXlHahZhYgJH9-rV6ouPro
If this seems interesting, please email us at [email protected] for a call.
Recent Comments
No comments
Leave a Comment
We will be happy to hear what you think about this post