Strategy for Combating New Threat Actors and Emerging Cyberattacks and Risks
This article proposes a security strategy that builds upon the well-established Defense-in-Depth concept, complemented by Zero trust.
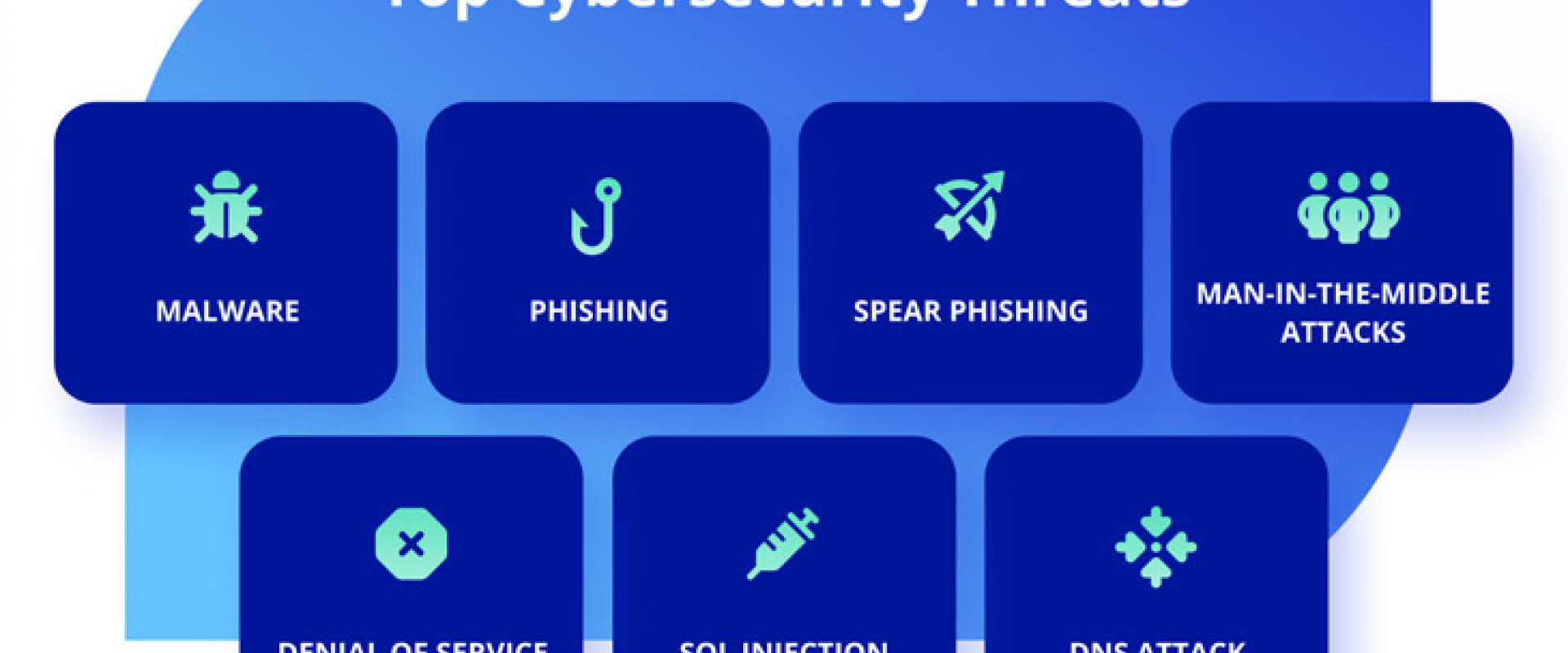
With the cyber threat landscape growing constantly and cyberattacks becoming more sophisticated, it is imperative for any organization to be well-prepared with a clear and actionable cyber defense strategy. As noted by Chuck Robbins, Chairman, and CEO at Cisco, during his keynote at the RSA Conference 2021, cybercrime caused an estimated $6 Trillion in damage globally in 2021 (1). Furthermore, the damage caused by cybercrime globally is estimated to grow about 15% per year, reaching $10.5 Trillion by 2025 (2). With remote working becoming a norm post-covid-19 pandemic in many organizations, the enterprise network perimeter has shifted, and more vulnerable points have been created. The Cyber security strategy needs to adapt to emerging attacks.
This article proposes a security strategy that builds upon the well-established Defense-in-Depth concept, complemented by a more recent paradigm known as Zero trust. After giving a brief overview of both concepts, we will provide more details on specific actions that, if implemented correctly, will increase your organization’s capabilities in combatting emerging cyberattacks and risks.
The Defense in Depth Concept
The concept of defense in depth originated from the military as a strategy to provide barriers to impede the progress of intruders while monitoring their progress and implementing a response to the incident. This concept has been translated and used mainly in cybersecurity as a layered set of detective and protective security measures designed to stop cyberattacks and reduce the consequences of a breach.
Because the information system architecture can be very complex in large organizations, potential vulnerabilities that can have lasting consequences can go undetected for a long time if exploited. Therefore, the defense-in-depth strategy uses a multi-layered multitier approach to improve the probability of detecting cyber intrusion and the capability to defend against malicious threat actors. The following table shows solutions and strategies that are recommended when implementing Defense-in-depth security.
|
Defense in Depth Strategy Solutions |
|
|
Risk Management Program |
|
|
Cybersecurity Architecture |
|
|
Physical Security |
|
|
Network Architecture |
|
|
Network Perimeter Security |
|
|
Host Security |
|
|
Security Monitoring |
|
|
Vendor Management |
|
|
Users Management |
|
Leveraging the Zero Trust Principle to Enable a Stronger Security Posture and Create a More Flexible Environment
Zero trust is an emerging concept that is quickly becoming a norm. According to research by Gartner, over 60% of organizations will embrace zero trust as a starting place for security by 2025.
Zero trust is a security paradigm that does not implicitly trust any user. With the Zero trust principle, each user must be explicitly identified, and access is only given to resources required for the user to perform their business function with minimal friction while the risk is reduced.

As shown in the above figure, zero trust enables the independence of work location. This is important in a post covid context where the need to work from home or from any remote location has grown dramatically.
This presents a shift from a location-centric model to a more data-centric approach and enables fine-grained security controls between users, systems, data, and assets.
Implementing the Strategy
We understand that our security strategy will be based on the Defense-in-Depth and the Zero trust concept so that we can implement specific actions within our information security program.
Identify Threat Actors and Assets
A successful information security program starts with a security risk assessment aligned with business objectives and goals. As part of the risk assessment, threat actors and any exposure to those threats must be identified.
The level of exposure can be determined, after identifying and classifying all information assets, with a risk profile associated with each asset.
It should be noted that threats to any business vary in size, capabilities, intentions, and means of operation. In addition, threat actors may also be internal to the organization (Insider threat) and may cause security breaches intentionally or by simple human error.
After extensive research, identification, and classification of threat actors, and information assets, the next phase is to start prioritizing.
Prioritize Areas of Work
In a large enterprise environment, the list of items to review after a risk assessment report can seem overwhelming; however, because failure is not an option, it is imperative to set a priority list of items, depending on the risk profile, lost expectancy, time to recovery, cost of replacement …etc.
The next step is to start setting up Security controls, which can be technical, administrative, or physical, depending on the nature of the activity and target asset.
Set Up Controls to Deter, Detect, Prevent, and Correct
First, the current state of existing controls should be identified, and their effectiveness for risk mitigation should be evaluated.
With attackers constantly advancing their capabilities using more sophisticated techniques, defense mechanisms should adapt and stay ahead regarding capabilities, technology, and security staff abilities. Technologies that use Artificial intelligence (IA) and Machine Learning (ML) techniques can be leveraged for more accurate detection, prevention, and alerting to reduce the burden on human resources, with fewer false positive alerts.
Security controls are usually preventive, deterrent, detective, or corrective.
As described in the ISO/IEC 27001:2022 framework for Information Security Management Systems (ISMS), preventive, deterrent, or detective types of controls are used to reduce the likelihood of the risk happening in the first place or at least to make it more difficult for the risk to occur (3). Therefore, risk and control analysis results should be reviewed to assess any gaps between the current and desired state of the information assets.
Preventing Attacks (Preventive Controls)
The goal of preventive controls is to prevent incidents from occurring, which means effectively barring threat actors from reaching their goals.
The best-expected outcome is for preventive controls to work all the time. Unfortunately, this is not always the case. Preventive controls are implemented based on the risk assessment result, asset classification, and prioritization.
Examples of Preventive Controls
- Security awareness training for all staff. The training should be conducted regularly, and cover a broad number of topics, giving staff example scenarios where they could be victims of attacks and explaining how to reduce the risk to themselves and the organization. Typical examples should be training staff to identify fishing emails, how to create a strong password and best practices on password usage, understanding social Engineering techniques, etc. Targeted training should be assigned based on the job functions performed by the personnel, and care must be taken to ensure that instructions are set at the appropriate level for easy consumption.
- Other preventive control measures should be selected appropriately, including firewalls, Intrusion Detection Systems (IDS), systems patching, antivirus programs installation, security settings tightening, and Role-based Access Control (RBAC) enforcement.
- Information security policies and procedures must be updated and regularly reviewed as the environment evolves.
Detecting Threat Actor’s Activity (Detective Controls)
Detective controls are used to provide visibility and reporting; this can help detect threats before they have any impact or immediately after.
It should be noted that attacks rarely happen out of the blue. Instead, attackers generally conduct activities such as information gathering and system architecture mapping through several reconnaissance activities before eventually conducting coordinated attacks from multiple random sources using spoofed IP addresses. These increasingly sophisticated attack techniques make it difficult to differentiate malicious traffic from legitimate traffic.
Following are some recommended detective measures, considering that this is not an exhaustive list. As with a “Defense in depth” approach, additional countermeasures are encouraged if they don’t conflict with or weaken existing controls.
Activity Log
Logging all activities on a system is a good starting point, and selected critical or emergency logs can be directed to designated systems such as Security Information and Event Management (SIEM) for analysis. Logging should include all failed attempts to log into the system, all successful attempts, and all modifications to system configuration and critical system data. Any other action should be logged and categorized. The SIEM can generate extensive analytics and graphs that will make it easier to identify malicious trends.
Vulnerability Scanning
Regular vulnerability scanning should be conducted as part of detection capabilities. This can be scheduled to be run automatically on all devices, and users or security specialists alert for detected vulnerabilities.
Virus and Malicious Software Scanning
Scanning all systems regularly for viruses and other malicious software is necessary. Alerts should be generated, and immediate action should be taken upon detection of any virus or suspicious software. In addition, the Antivirus signature database should be updated daily.
Identity and Access Management (IAM)
A solid Identity and access management practice will provide better visibility and reporting. When user activities are appropriately recorded, unusual activities become easier to detect. With a good IAM in place backed up with a strong password policy, multi-factor authentication, and Role-based Access Control (RBAC), legitimate users only have access to information necessary to perform their job functions (The principle of least privilege)
IDS Systems
Intrusion detection systems are a key tool to help detect suspicious network activities. They are generally positioned at a central point (or entry point) within a network architecture and receive a copy of all traffic for behavioral analysis. A modern IDS will typically use Artificial Intelligence and machine learning algorithms to discover unusual traffic patterns via predictive models (traffic pattern classification).
Audit
A regular audit is important for detecting security gaps, bad practices, and event breaches that may have gone unnoticed by other mechanisms. Audits can be conducted by internal or external auditors and will be more comprehensive if conducted against a security standard. For instance, the audit can be conducted against the ISO/IEC 27001 for the Information Security Management System, or more specifically against a specific standard such as PCI/DSS, HIPAA, SOC2, … etc., if the organization needs to comply with the standard.
Conclusion
As the number of cyber-attacks continues to grow year after year, and threat actors continue to use more sophisticated techniques, Efficiently addressing emerging cybersecurity threats requires a clear understanding of the current security challenges and specific defensive countermeasures. In this article, we have proposed a list of actionable items recommended to successfully combat emerging threats. More specifically, we recommend that a good information security management program be implemented through a strong governance and Risk management program supported by the organization’s board of directors and the executive team. On the technical side, we propose a cybersecurity strategy that implements Defense-in-Depth security methodologies and uses the zero-trust paradigm to minimize risk to the organization and minimize the impact of attacks.
We Provide consulting, implementation, and management services on DevOps, DevSecOps, Cloud, Automated Ops, Microservices, Infrastructure, and Security
Services offered by us: https://www.zippyops.com/services
Our Products: https://www.zippyops.com/products
Our Solutions: https://www.zippyops.com/solutions
For Demo, videos check out YouTube Playlist: https://www.youtube.com/watch?v=4FYvPooN_Tg&list=PLCJ3JpanNyCfXlHahZhYgJH9-rV6ouPro
If this seems interesting, please email us at [email protected] for a call.
Relevant Blogs:
5 Ways to Secure a Virtual Machine in Cloud Computing
19 Most Common OpenSSL Commands for 2023
Product Security (DevSecOps Practices)
Recent Comments
No comments
Leave a Comment
We will be happy to hear what you think about this post